INFOGRAPHIC: 4 Imperatives to Safeguard Your Move to Cloud and Reduce Risk
•
4 recomendaciones•2,682 vistas
Enterprises are moving to the cloud as they realize the business advantages but they still have security concerns. Considering the complexity and various ways cloud is used, security leaders and IT teams feel overwhelmed by the spate of information that they have to keep track. This infographic provides a framework to help implement cloud security across all cloud types - private, public, hybrid as well as cloud utilization models like IaaS, PaaS and SaaS. This framework provides details on the specific steps that need to be taken to help achieve cloud security. http://securityintelligence.com/media/infographic-top-3-cloud-security-concerns/
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
Más contenido relacionado
Más de IBM Security
Más de IBM Security (20)
How to Build a Faster, Laser-Sharp SOC with Intelligent Orchestration

How to Build a Faster, Laser-Sharp SOC with Intelligent Orchestration
Orchestrate Your Security Defenses to Optimize the Impact of Threat Intelligence

Orchestrate Your Security Defenses to Optimize the Impact of Threat Intelligence
Your Mainframe Environment is a Treasure Trove: Is Your Sensitive Data Protec...

Your Mainframe Environment is a Treasure Trove: Is Your Sensitive Data Protec...
Meet the New IBM i2 QRadar Offense Investigator App and Start Threat Hunting ...

Meet the New IBM i2 QRadar Offense Investigator App and Start Threat Hunting ...
Understanding the Impact of Today's Security Breaches: The 2017 Ponemon Cost ...

Understanding the Impact of Today's Security Breaches: The 2017 Ponemon Cost ...
How to Improve Threat Detection & Simplify Security Operations

How to Improve Threat Detection & Simplify Security Operations
Orchestrate Your Security Defenses; Protect Against Insider Threats 

Orchestrate Your Security Defenses; Protect Against Insider Threats
Ponemon Institute Reviews Key Findings from “2017 State of Mobile & IoT Appli...

Ponemon Institute Reviews Key Findings from “2017 State of Mobile & IoT Appli...
See How You Measure Up With MaaS360 Mobile Metrics

See How You Measure Up With MaaS360 Mobile Metrics
Nowhere to Hide: Expose Threats in Real-time with IBM QRadar Network Insights

Nowhere to Hide: Expose Threats in Real-time with IBM QRadar Network Insights
Safeguard Healthcare Identities and Data with Identity Governance and Intelli...

Safeguard Healthcare Identities and Data with Identity Governance and Intelli...
Cybersecurity In The Cognitive Era: Priming Your Digital Immune System

Cybersecurity In The Cognitive Era: Priming Your Digital Immune System
Último
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Último (20)
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...

Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...

Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024

Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
INFOGRAPHIC: 4 Imperatives to Safeguard Your Move to Cloud and Reduce Risk
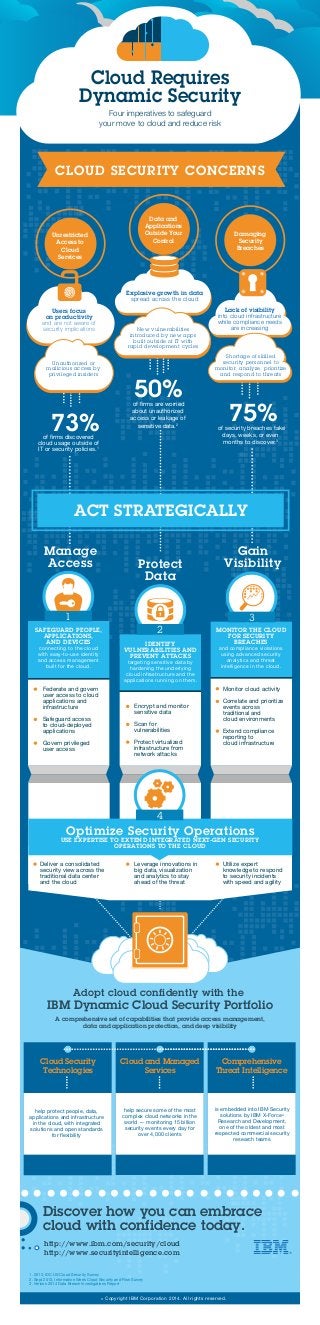
- 1. Cloud Requires Dynamic Security CLOUD SECURITY CONCERNS Unrestricted Access to Cloud Services Explosive growth in data spread across the cloud New vulnerabilities introduced by new apps built outside of IT with rapid development cycles Unauthorized or malicious access by privileged insiders Shortage of skilled security personnel to monitor, analyze, prioritize and respond to threats ACT STRATEGICALLY Manage Access Protect Data Gain Visibility Encrypt and monitor sensitive data Scan for vulnerabilities Protect virtualized infrastructure from network attacks Optimize Security Operations USE EXPERTISE TO EXTEND INTEGRATED NEXT-GEN SECURITY OPERATIONS TO THE CLOUD Adopt cloud confidently with the IBM Dynamic Cloud Security Portfolio A comprehensive set of capabilities that provide access management, data and application protection, and deep visibility help protect people, data, applications and infrastructure in the cloud, with integrated solutions and open standards 1. 2013, IDC US Cloud Security Survey 2. Sept 2013, Information Week Cloud Security and Risk Survey 3. Verizon 2014 Data Breach Investigations Report Monitor cloud activity Correlate and prioritize events across traditional and cloud environments Extend compliance reporting to cloud infrastructure Federate and govern user access to cloud applications and infrastructure Safeguard access to cloud-deployed applications Govern privileged user access Data and Applications Outside Your Control Damaging Security Breaches 50% of firms are worried 73% about unauthorized 75% access or leakage of of firms discovered cloud usage outside of IT or security policies.1 sensitive data.2 of security breaches take days, weeks, or even months to discover.3 Users focus on productivity and are not aware of security implications Unauthorized or malicious access by privileged insiders Lack of visibility into cloud infrastructure while compliance needs are increasing Four imperatives to safeguard your move to cloud and reduce risk Cloud Security Technologies Cloud and Managed Services Comprehensive Threat Intelligence Deliver a consolidated security view across the traditional data center and the cloud Leverage innovations in big data, visualization and analytics to stay ahead of the threat Utilize expert knowledge to respond to security incidents with speed and agility Discover how you can embrace cloud with confidence today. http://www.ibm.com/security/cloud http://www.securityintelligence.com © Copyright IBM Corporation 2014. All rights reserved. for flexibility is embedded into IBM Security solutions by IBM X-Force® Research and Development, one of the oldest and most respected commercial security research teams help secure some of the most complex cloud networks in the world — monitoring 15 billion security events every day for over 4,000 clients SAFEGUARD PEOPLE, APPLICATIONS, AND DEVICES connecting to the cloud with easy-to-use identity and access management built for the cloud. IDENTIFY VULNERABILITIES AND PREVENT ATTACKS targeting sensitive data by hardening the underlying cloud infrastructure and the applications running on them. MONITOR THE CLOUD FOR SECURITY BREACHES and compliance violations using advanced security analytics and threat intelligence in the cloud. 1 2 3 4
