Storyboard for Bookbuilder
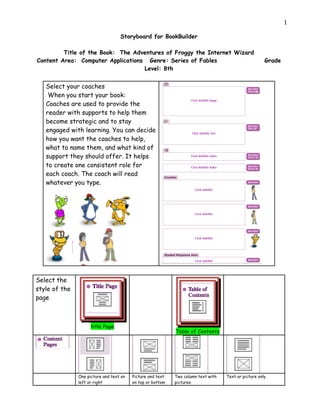
- 1. 1 Storyboard for BookBuilder Title of the Book: The Adventures of Froggy the Internet Wizard Content Area: Computer Applications Genre: Series of Fables Grade Level: 8th Select your coaches When you start your book: Coaches are used to provide the reader with supports to help them become strategic and to stay engaged with learning. You can decide how you want the coaches to help, what to name them, and what kind of support they should offer. It helps to create one consistent role for each coach. The coach will read whatever you type. Select the style of the page title Page Table of Contents One picture and text on Picture and text Two column text with Text or picture only left or right on top or bottom pictures
- 2. 2 Page 1 Element Image & “Wake up” Video embedded in Book Builder that kicks off copyright when student turns the page. info Size, Color Text Text size: 18pt Size, color Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio n/a Coach 1 n/a Coach 2 n/a Coach 3 n/a Student List at least 5 issues you saw in the video. Response
- 3. 3 Page 1 Element Image & Young boy in a neighborhood. copyright info Size, Color Text Meet the Netizens Size, color Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio n/a Coach 1 The Internet can be compared to a large neighborhood. There are good neighbors, bad neighbors and neighbors you never see. Everyone in the neighborhood is a Netizen. Coach 2 Netizens are everyone who lives on the Internet. We like some, dislike some and do not really know others. Coach 3 Netizens are everyone on the Internet. Just like in your neighborhood, there are people we can be friends with and people we should stay away from. We will meet some different netizens over the next few pages. Student n/a Response
- 4. 4 Page 2 Element Image & Young boy looking at a picture of a copyright fire/flame (campfire) info Size, Color Text Let‟s meet Fanny Flamer Size, color Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio n/a Coach 1 Flamers are rude and vicious in their attacks on others on the Internet. Sometimes the attacks are personally directed at someone the flamer knows, but many times the attack is anonymous. Coach 2 Flamers often hurt other netizens‟ feelings by attacking them for minor reasons (such as misspelling a word on FB) or in retaliation for a real or perceived injury to the Flamer. Coach 3 Flamers make rude or mean comments about other people. Just like when someone picks on someone else in school, other people may join in just to be a part of it. Student n/a Response
- 5. 5 Page 3 Element Image & Young boy running from an image of troll - on copyright wikipedia there is a common image of an info internet troll Size, Color Text Tommy the Troll strolls in... Size, color Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio n/a Coach 1 Tommy the Troll is the leader of the Flamers. He usually spreads the fuel that feeds the flamers‟ fires. He will often do this on a chatboard, social media site or the comments section of a news or entertainment article. He picks a hot-button item and gets people to engage in inflammatory converstation. Coach 2 Tommy the Troll likes to rile people up. He feels powerful by getting others to engage in mean-spirited conversations. By undermining other people‟s views and ideas, Tommy hurts other people. Coach 3 Tommy the Troll intentionally says mean things when on chat boards, facebook or other public areas of the Internet. He likes to start fights and keep egging others into negative conversations. Student n/a Response
- 6. 6 Page 4 Element Image & Young boy looking askance at an image of a copyright „shadowy‟ character (Larry the Lurker) info Size, Color Text Text size: 18pt Size, color Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio n/a Coach 1 Larry the Lurker hangs out on message boards, newsgroups, chat rooms, file sharing or other interactive systems and watches other peoples‟ activity. Larry rarely, if ever, participates in the on-line activity. Coach 2 Larry the Lurker stays in the background without building relationships with other Internet inhabitants. He does not make friends or enemies, but keeps to himself. Coach 3 Larry the Lurker is a non-active participant in on-line activities. He is a spectator, who watches what everyone is doing, without getting involved. Student n/a Response
- 7. 7 Page 5 Element Image & Young boy eyeing a hatchet copyright info Size, Color Text Hannah the Hacker breaks the law Size, color Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio n/a Coach 1 Hannah the Hacker breaks into other netizen‟s Internet houses/cars in order to steal their belongings. She might steal something we can touch, like money from a bank account or she might steal something we can‟t touch, like our identity. Coach 2 Hannah the Hacker takes things that are not hers. When someone takes things from other people, it does not matter if they do it in a store or on the Internet. Someone becomes a victim of theft Coach 3 Hannah the Hacker steals information and goods from other people. Instead of using a gun or her fists, she uses the internet. Student n/a Response
- 8. 8 Page 6 Element Image & the frog, the troll, the flame, the hatchet, copyright the shadow and the young boy info Size, Color Text How do we avoid the Bad Guys? Size, color Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio n/a Coach 1 Do you know people in real life that you could compare to the people we met today? How do you avoid them on the street or in school? Would you be as careful to avoid them on the internet? Coach 2 How do people who behave like these „bad guys‟ make you feel? What can you do to protect yourself from getting hurt? Coach 3 Can you list the people you met today? Will you promise to try and stay safe by staying away from them? Student Free response screen where student can Response type in answers
- 9. 9 Page 7 Element Image & A curtained room or maybe an oriental copyright privacy screen info Size, Color Text Chapter 2 - Privacy Size, color Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 Privacy has to do with keeping information to yourself that could be used to take advantage of you or your money. Coach 2 Private information can be used to hurt you or someone you care about. Coach 3 Privacy is that data that is yours and yours only. Student n/a Response
- 10. 10 Page 9 Element Image & A young Hispanic girl typing on the computer. copyright A picture of an address book. info Size, Color Text Typing: “Going to the mall with friends, be home Size, color soon. TMC 236-4587” Don‟t you know how unsafe that is?.... Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 People can take information like your name and your address to find out more information about you. This information can lead to them stealing your identity for any number of uses. Coach 2 People can use your personal to find you in the real world to stalk you or kidnap you. The most minor thing someone can do with your personal information is to take your e-mail address and send you unwanted e-mails. Coach 3 Personal information includes your street address, your phone number, your birthday. All this information makes it easier for people to find you. Student Give an example of putting personal information on the web where it can be harmful. What do you think could happen Response with that information?
- 11. 11 Page 10 Element Image & Image of copyright Froggy, info Facebook on a Size, Color computer monitor Text It is so easy to set your privacy on social web sites Size, color such as Facebook (video on setting privacy for Facebook embedded) Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 Setting privacy settings is a very importance step to protecting yourself online. When you protect yourself, you protect your family as well. Coach 2 People who set their privacy settings correctly on social web sites show a great deal of wisdom in protecting themselves. If you don‟t set your privacy settings, you‟re asking people to come in and change your settings or post things that will reflect poorly on you. Coach 3 It‟s important to set your privacy settings to protect yourself from mean Student n/a Response
- 12. 12 Page 11 Element Image & Evil Warlock gif, Froggy, copyright info Size, Color Size, color Text When you are on the Internet, it‟s important Size, color to safeguard yourself against Cyber Warlocks such as Impostors, Trolls, and Lurkers... Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 You should be aware of who you are communicating with. If you share your information with someone you have never met in person, you have no way of knowing, for sure they are who they say they are. Coach 2 Strangers pose as other people in order to take advantage of you or worse to embass or hurt you. Coach 3 Be careful who you talk to. If you don‟t know them, don‟t talk to them. If you feel unsafe at all, leave the web site immediately. Student n/a Response
- 13. 13 Page 12 Element Image & Hispanic girl , mask, Froggy copyright info Size, Color Text Juanita is chatting with someone online about a Size, color dance she went to last night. Froggy asks her if she knows that person... Impostors claim to be someone they‟re not. For instance.... Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 Police often catch Internet predators by posing as young people and watch for people who say things that doesn‟t sound right for a young person. Coach 2 It‟s not safe to talk to some one you don‟t know in real life, they could be older than you, a bully pretending to be your friend, or even your mother trying to catch you misbehaving. Coach 3 Never talk to some one you have never met in real life. They may not be who they say they are. Student n/a Response
- 14. 14 Page 13 Element Image & Hispanic girl, Froggy, Picture of Tommy the copyright Troll info Size, Color Size, color Text Trolls are people who verbally abuse people Size, color online, on web sites such as chat rooms, facebook, blogs.... Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 People who make mean comments, or want to talk about things that are off-topic, are verbally abusing the privilege of using the Internet. If someone says something to you that make you unconfortable, get out of there and let an adult know. Coach 2 People who say inflammatory things are just trying to get a response out of you. If you respond to them, you are giving them what they want and are setting yourself up for trouble. Coach 3 Trolls are just like in story books. They are mean and don‟t deserve your time. Don‟t let them get you mad. Student n/a Response
- 15. 15 Page 14 Element Image & Pictures of a Lurker (from gaming), Froggy, copyright Hispanic Girl info Size, Color Text Be careful what you say because you never Size, color know who‟s listening... Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 People who tend to hang out and watch or listen to conversations are not necessarily bad, on the other hand, it can lead to problems if you say something without thinking. Coach 2 You never know who‟s lurking on a website or in a chat room so you should use good judgement about what you are saying. Never say anything in a public chat room about someone you would not say to their face. Coach 3 Be careful what you say online. You never know who is “listening” and may get mad. Student Lurkers can monitor public chat rooms but Response generally can not enter a private chat. What are the dangers of chatting in a private chat room?
- 16. 16 Page 15 Element Image & Hispanic girl at computer, looking at e-mail window copyright (google mail or yahoo mail) Froggy info Size, Color Text Juanita, don‟t open that email, do you know that Size, color person? Only open e-mail from people you know... Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 (Logical)Even if the email is from someone you know, if the email doesn‟t seem to make sense or is asking you for personal information delete it and contact the person to let them know. Coach 2 E-mails coming from people you know, or even people you don‟t know but think you do (like a celebrity) can be generated by a virus or program that create e-mails to fish for information. These e-mails are not real and should be deleted immediately. Coach 3 (Low Level) Immediately delete emails that come from people you don‟t know. Student n/a Response
- 17. 17 Page 16 Element Image & Hispanic girl at computer, Froggy copyright info Size, Color Text “Look, I won a new X-Box 360, bonus!!!” Size, color That‟s spam, don‟t respond to it, you should delete it.... Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 (Logical)Don‟t ever unsubscribe when given an option in a SPAM email. This is how they know they have a working email address and you will get even more SPAM Coach 2 (Emotional) Those e-mails look great and exciting but the people do that on purpose to get you to click on it and give them information they need to take advantage of you. Coach 3 (Low Level)SPAM emails will sometime give you an option of unsubscribing. Never do this because it will cause you to get more SPAM emails. Delete it immediately. Student n/a Response
- 18. 18 Page 17 Element Image & Hispanic girl at computer about to click copyright attachment, Froggy info Size, Color Text “This is that song I asked Mackenzie for!! I Size, color can‟t wait to her Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 (Logical)The most common way that viruses are spread on the Internet is through email attachments. If you receive an email with an attachment answer the following questions before you open it. Is this from someone I know, does the email make sense. If not then delete it immediately.. Coach 2 (Emotional) Always be suspicious of attachments that come in email. ….... Coach 3 (Low Level)Never open an email attachment unless someone you know told you they were sending it. Email attachments are the most common way viruses are spread. Student If you receive an email that contains an attachment what should you do? Response
- 19. 19 Page 18 Element Image & Juanita is looking at an pop up message about copyright having her computer checked for viruses. info Size, Color Text Juanita, anytime you see a pop up like that, Size, color never click on it. This is actually a virus waiting to happen and could seriously damage your computer... Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 Before clicking on a link on a web site or e-mail, always check on Snopes to see if it‟s an urban legend or the real thing. Also, make sure you have a GOOD anti-virus software on your computer and that you keep it up-to-date. Coach 2 Pop ups are annoying and can carry viruses and the like that can cause you great heart ache and stress. Really bad ones could cause you to have to have your computer repaired, which could be costly. Coach 3 (Low Level)If you get a pop up message saying your computer has a virus and to click here to fix it, don‟t. Shut down your computer and scan your computer with your own virus software. Student If you receive an email that contains a hyperlink what should you do? Response
- 20. 20 Page 19 Element Image & Computer and cellphone - Microsoft Clipart copyright Frog info Size, Color Text Text size: 18pt Size, color Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 Most of the things you do on the internet you do on your smart phone. Following the advice from the earlier sections of this book will keep you informed and safer. Coach 2 There are bad things that can happen if you don‟t use your cell phone properly. With these dangers, you could end up with our feelings hurt or worse. Coach 3 Almost everything you do on the computer or internet can be done on cell phones. You have to be just as careful on a cell phone as you do on the computer Student n/a Response
- 21. 21 Page 20 Element Image & Advertisment - Microsoft Clipart copyright Frog info Size, Color Text Text size: 18pt Size, color Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 Advertisers are always looking for ways to make extra money. They can ask you to text to vote for someone, get ringtones, or join groups. If you look at the small writing on these ads, they often charge you for their products. Some ads are scams and can steal your information or give you a virus, so be very careful. Coach 2 You might want that singer to win or think that ringtone is to die for, but be very careful when texting advertisers. Always ask for permission first. Coach 3 Sometimes, television or radio shows, magazine articles, and commercials ask you to send a text to a certain number. Always ask a parent before you do this because sometimes these texts charge you money or they can be fake. These fake numbers steal your information or can give your phone a virus. Student Where have you seen ads that ask you to Response text?
- 22. 22 Page 21 Element Image & Cell phone photo by OCAL copyright Frog by info Size, Color Text Text size: 18pt Size, color Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 Once you send a picture or message, it is saved on your cell phone company‟s server forever. These messages can be used by authorities to prove that you were doing something wrong. If someone sends you one of these messages, tell your parents immediately. Coach 2 You might be tempted to send pictures or write something hurtful, but you can get in a lot of trouble for doing it. Remember, these messages are out there forever and can not be erased. Coach 3 Never send pictures of yourself or others that are inappropriate. Also, never send hateful messages. These are saved forever by the cell phone company and you can not erase them. Erasing them off your phone does not erase them from your cell phone company. Student What should you do if you get inappropriate Response pictures or words?
- 23. 23 Page 22 Element Image & Link: copyright http://www.youtube.com/watch?v=bdQBurXQOeQ info Created by the AD Council Size, Color Text Text size: 18pt Size, color Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 You should never spread rumors or gossip, especially with your cellphone. Chances are, if the person you are talking about finds out, they could tell the authorities and you would get in trouble. Coach 2 You may think that story about someone in class is funny, but if it is hurtful, don‟t text it. Coach 3 Spreading gossip and rumors with your cellphone is not only hurtful, but could get you in trouble. Police can look up your pictures and messages and charge you and your parents with cyber bullying. Student n/a Response
- 24. 24 Page 23 Element Image & “Wake up” Video embedded in Book Builder that kicks off copyright when student turns the page. info Size, Color Text Text size: 18pt Size, color Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio n/a Coach 1 n/a Coach 2 n/a Coach 3 n/a Student List all issues you saw in the video. How did Response these change from the first time you viewed it?
- 25. 25 Index A Element Image & Picture of a dictionary copyright info Size, Color Text Glossary Size, color Text size: 18pt Font: Comic Sans Color: Black Audio Text to Speech via BookBuilder Audio Coach 1 N/A Coach 2 N/A Coach 3 N/A Student n/a Response
- 26. 26