SRX3600 Cluster & IDP
- 1. Kashif Latif
- 2. The SRX Clustering Module (SCM) is a card that you can install in the services gateway to enable the dual control link feature for chassis cluster supported in Junos OS Release 10.2.
- 3. When deploying SRX3600’s in H/A cluster, the SRX cluster module utilize the redundant architecture design of the SRX3000 line to provide full control link resiliency for mission critical environments.
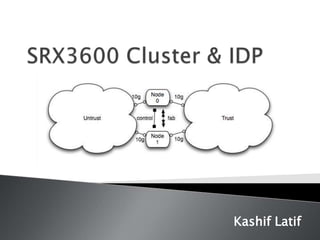
- 4. To form a chassis cluster, a pair of the same kind of supported SRX-series devices or J-series devices are combined to act as a single system that enforces the same overall security. For SRX 5600 and SRX 5800 chassis clusters, the placement and type of Services Processing Cards (SPCs) must match in the two clusters. For SRX 3400 and SRX 3600 chassis clusters, the placement and type of SPCs, Input/output Cards (IOCs), and Network Processing Cards (NPCs) must match in the two devices.
- 5. For J-series chassis clusters, although the devices must be the same kind, they can contain different Physical Interface Modules (PIMs). When a device joins a cluster, it becomes a node of that cluster. With the exception of unique node settings and management IP addresses, nodes in a cluster share the same configuration.
- 6. You can deploy up to 15 chassis clusters in a Layer 2 domain. Clusters and nodes are identified in the following way: 1. A cluster is identified by a cluster ID (cluster-id) specified as a number from 1 through 15. 2. A cluster node is identified by a node ID (node) specified as a number from 0 to 1.
- 7. Juniper Networks Intrusion Detection and Prevention (IDP) products provide comprehensive and easy-to-use in-line protection that stops network and application level attacks before they inflict any damage to the network, minimizing the time and costs associated with maintaining a secure network. Usingindustry-recognized stateful detection and prevention techniques, Juniper Networks IDP provides zero day protection against worms, Trojans, spyware, key loggers and other malware from penetrating the network or spreading from already infected users.
- 8. Juniper Networks IDP not only helps protect networks against attacks, it provides information on rogue servers, as well as types and versions of applications and operating systems that may have unknowingly been added to the network. Application signatures, available on the Juniper Networks IDP, goes a step further and enables accurate detection of specific applications such as peer-to-peer or instant messaging.
- 11. Juniper Networks IDP 75 brings full Intrusion prevention System (IPS) capability to small and mid-size businesses as well as remote offices. Juniper Networks IDP 250 and IDP 800 offer market-leading IPS capabilities to mid-size and large enterprises as well as service providers. Juniper Networks IDP 8200 offers market leading performance with 10 Gbps of real world throughput and is also suited for large enterprises and service providers.
- 12. Kashif Latif
