CRC in Data Communication DC19
•Descargar como PPT, PDF•
3 recomendaciones•1,916 vistas
Denunciar
Compartir
Denunciar
Compartir
Recomendados
Más contenido relacionado
La actualidad más candente
La actualidad más candente (16)
Similar a CRC in Data Communication DC19
Similar a CRC in Data Communication DC19 (20)
Más de koolkampus
Más de koolkampus (17)
Transmission of Digital Data(Data Communication) DC11

Transmission of Digital Data(Data Communication) DC11
Analog to Digital Encoding in Data Communication DC9

Analog to Digital Encoding in Data Communication DC9
Analog to Analog Modulation in Data Communication DC10

Analog to Analog Modulation in Data Communication DC10
Authentication Application in Network Security NS4

Authentication Application in Network Security NS4
Último
Último (20)
Unblocking The Main Thread Solving ANRs and Frozen Frames

Unblocking The Main Thread Solving ANRs and Frozen Frames
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service

WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service
Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365

Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365
Enhancing Worker Digital Experience: A Hands-on Workshop for Partners

Enhancing Worker Digital Experience: A Hands-on Workshop for Partners
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Swan(sea) Song – personal research during my six years at Swansea ... and bey...

Swan(sea) Song – personal research during my six years at Swansea ... and bey...
CRC in Data Communication DC19
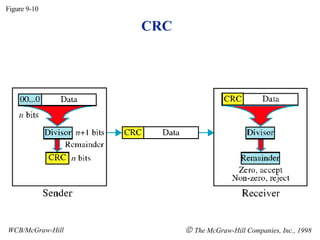
- 1. CRC Figure 9-10 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 2. Binary Division Figure 9-11 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 3. Polynomial Figure 9-12 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 4. Figure 9-13 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Polynomial and Divisor
- 5. Standard Polynomials Figure 9-14 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 6. Checksum Figure 9-15 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 7. Figure 9-16 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Data Unit and Checksum
- 8. Error Correction Figure 9-17 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 9. Hamming Code Figure 9-18 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 10. Figure 9-19 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Hamming Code
- 11. Figure 9-19-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Hamming Code
- 12. Figure 9-20 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Example of Hamming Code
- 13. Single-bit error Figure 9-21 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 14. Figure 9-22 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Error Detection