Tcp sockets
•Descargar como PPT, PDF•
2 recomendaciones•1,681 vistas
TCP Sockets
Denunciar
Compartir
Denunciar
Compartir
Recomendados
Recomendados
Más contenido relacionado
La actualidad más candente
La actualidad más candente (20)
Destacado
Destacado (19)
1ip Tunneling And Vpn Technologies 101220042129 Phpapp01

1ip Tunneling And Vpn Technologies 101220042129 Phpapp01
UNDOCUMENTED Vyatta vRouter: Unbreakable VPN Tunneling (MEMO) 

UNDOCUMENTED Vyatta vRouter: Unbreakable VPN Tunneling (MEMO)
VPN, Its Types,VPN Protocols,Configuration and Benefits

VPN, Its Types,VPN Protocols,Configuration and Benefits
Similar a Tcp sockets
Similar a Tcp sockets (20)
Más de babak danyal
Más de babak danyal (20)
Classical Encryption Techniques in Network Security

Classical Encryption Techniques in Network Security
Último
APM Welcome
Tuesday 30 April 2024
APM North West Network Conference, Synergies Across Sectors
Presented by:
Professor Adam Boddison OBE, Chief Executive Officer, APM
Conference overview:
https://www.apm.org.uk/community/apm-north-west-branch-conference/
Content description:
APM welcome from CEO
The main conference objective was to promote the Project Management profession with interaction between project practitioners, APM Corporate members, current project management students, academia and all who have an interest in projects.APM Welcome, APM North West Network Conference, Synergies Across Sectors

APM Welcome, APM North West Network Conference, Synergies Across SectorsAssociation for Project Management
God is a creative God Gen 1:1. All that He created was “good”, could also be translated “beautiful”. God created man in His own image Gen 1:27. Maths helps us discover the beauty that God has created in His world and, in turn, create beautiful designs to serve and enrich the lives of others.
Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...

Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...christianmathematics
Último (20)
Measures of Central Tendency: Mean, Median and Mode

Measures of Central Tendency: Mean, Median and Mode
Kisan Call Centre - To harness potential of ICT in Agriculture by answer farm...

Kisan Call Centre - To harness potential of ICT in Agriculture by answer farm...
APM Welcome, APM North West Network Conference, Synergies Across Sectors

APM Welcome, APM North West Network Conference, Synergies Across Sectors
Disha NEET Physics Guide for classes 11 and 12.pdf

Disha NEET Physics Guide for classes 11 and 12.pdf
Measures of Dispersion and Variability: Range, QD, AD and SD

Measures of Dispersion and Variability: Range, QD, AD and SD
Ecosystem Interactions Class Discussion Presentation in Blue Green Lined Styl...

Ecosystem Interactions Class Discussion Presentation in Blue Green Lined Styl...
Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...

Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...
Beyond the EU: DORA and NIS 2 Directive's Global Impact

Beyond the EU: DORA and NIS 2 Directive's Global Impact
Tcp sockets
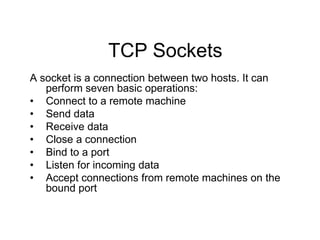
- 1. TCP Sockets A socket is a connection between two hosts. It can perform seven basic operations: • Connect to a remote machine • Send data • Receive data • Close a connection • Bind to a port • Listen for incoming data • Accept connections from remote machines on the bound port
- 2. Client Sockets • The program creates a new socket with a Socket( ) constructor. • The socket attempts to connect to the remote host. • Once the connection is established, the local and remote hosts get input and output streams from the socket and use those streams to send data to each other. • This connection is full-duplex; both hosts can send and receive data simultaneously. • What the data means depends on the protocol; different commands are sent to an FTP server than to an HTTP server. There will normally be some agreed-upon hand-shaking followed by the transmission of data from one to the other. • When the transmission of data is complete, one or both sides close the connection. Some protocols, such as HTTP 1.0, require the connection to be closed after each request is serviced. Others, such as FTP, allow multiple requests to be processed in a single connection.
- 6. Constructors Constructor creates a TCP socket to the specified port on the specified host and attempts to connect to the remote host
- 7. Continued.. public Socket(String host, int port) throws UnknownHostException, IOException • public Socket(String host, int port, InetAddress interface, int localPort) throws IOException • public Socket(InetAddress host, int port, InetAddress interface, int localPort) throws IOException if 0 is passed for the local port number, java randomly selects port number between 1024 and 65,535.
- 8. Getting Information About a Socket • public InetAddress getInetAddress( ) • public int getPort( ) • public int getLocalPort( ) • public InetAddress getLocalAddress( ) public String toString( ) (Object Method)
- 9. Sockets for Servers • Java provides a ServerSocket class to allow programmers to write servers. • A ServerSocket runs on the server and listens for incoming TCP connections. • Each ServerSocket listens on a particular port on the server machine. • When a client Socket on a remote host attempts to connect to that port, the server wakes up, negotiates the connection between the client and the server, and opens a regular Socket between the two hosts.
- 10. • The operating system stores incoming connection requests addressed to a particular port in a first-in, first-out queue. • The default length of the queue is normally 50, though this can vary from operating system to operating system.
- 11. The basic life cycle of a server 1. A new ServerSocket is created on a particular port using a ServerSocket( ) constructor. 2. The ServerSocket listens for incoming connection attempts on that port using its accept( ) method. 3. accept( ) blocks until a client attempts to make a connection, at which point accept( ) returns a Socket object connecting the client and the server. 4. Socket's getInputStream( )method, getOutputStream( ) method, are called to get input and output streams that communicate with the client. 5. The server and the client interact according to an agreed-up on protocol until it is time to close the connection. 6. The server, the client, or both close the connection. 7. The server returns to step 2 and waits for the next connection
- 12. Constructors • public ServerSocket(int port) throws IOException, BindException • public ServerSocket(int port, int queueLength)throws IOException, BindException • public ServerSocket(int port, int queueLength,InetAddress bindAddress) throws IOException • An IOException when creating a ServerSocket almost always means one of two things. – Either another server socket is already using the requested port, – or you're trying to connect to a port from 1 to 1023 on Unix without root (superuser) privileges.
- 13. get Methods • public InetAddress getInetAddress( ) • public int getLocalPort( )
