Answer sheet of switching & routing
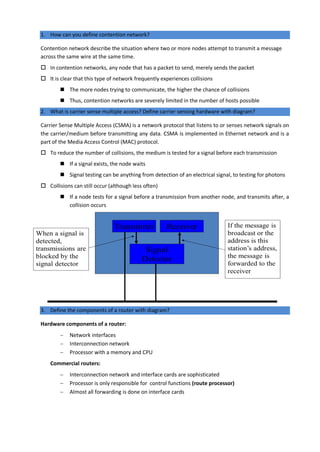
- 1. 1. How can you define contention network? Contention network describe the situation where two or more nodes attempt to transmit a message across the same wire at the same time. In contention networks, any node that has a packet to send, merely sends the packet It is clear that this type of network frequently experiences collisions The more nodes trying to communicate, the higher the chance of collisions Thus, contention networks are severely limited in the number of hosts possible 2. What is carrier sense multiple access? Define carrier sensing hardware with diagram? Carrier Sense Multiple Access (CSMA) is a network protocol that listens to or senses network signals on the carrier/medium before transmitting any data. CSMA is implemented in Ethernet network and is a part of the Media Access Control (MAC) protocol. To reduce the number of collisions, the medium is tested for a signal before each transmission If a signal exists, the node waits Signal testing can be anything from detection of an electrical signal, to testing for photons Collisions can still occur (although less often) If a node tests for a signal before a transmission from another node, and transmits after, a collision occurs 3. Define the components of a router with diagram? Hardware components of a router: Network interfaces Interconnection network Processor with a memory and CPU Commercial routers: Interconnection network and interface cards are sophisticated Processor is only responsible for control functions (route processor) Almost all forwarding is done on interface cards
- 2. Functional Components: 4. “Router has modularized network interfaces” Explain? Often, routers have modularized network interfaces a. One can add/remove/replace network interfaces as needs change b. Some routers can accept network interface modules of different types (e.g. Ethernet, Token Ring) c. Each network interface would have its own: i. Input buffer ii. Output buffer iii. Routing processor (in high-end routers) 5. What are the differences between hub, layer2 and layer3 switches? Explain with necessary diagram? Interface Card Interconnection Network Interface Card Interface Card Processor CPUMemory
- 3. Hub: Transmission from a station received by central hub and retransmitted on all outgoing lines Only one transmission at a time Layer 2 Switch: Incoming frame switched to one outgoing line Many transmissions at same time Flat address space Broadcast storm Only one path between any 2 devices Solution 1: sub networks connected by routers Solution 2: layer 3 switching, packet-forwarding logic in hardware Layer 3 Switch: Uses layer 3 routing to determine a path for packets Once a path is found, subsequent packets are switched This switching typically occurs on layer 2 6. Define packet tunneling in Internet with necessary diagram? Tunneling is the transmission of data in such a way that the routing nodes in the network are unaware that the transmission is from a different network. Working principle: Source sends packets to an intermediate gateway Intermediate gateways put the whole packet into the payload field (don't interpret it). The destination will understand the packet
- 4. Tunneling a packet from Paris to London 7. What is shortest path routing? Find the shortest path from a source node to destination node? Shortest Path Routing is a static routing algorithm that just finds the shortest path. A graph is used to represent the network. a. Each node of the graph represents a router. b. Each arc of the graph represents a communication link. c. To choose the route between a given pair of routers, the algorithm just finds the shortest path between them on the graph. Metric used in the shortest path. a. Number of hops b. Geographic distance in miles/kilometers c. Transmission delay fastest path
- 5. The first 5 steps used in computing the shortest path from A to D. The arrows indicate the working node. 8. Explain different types of packet fragmentation with diagram? Suppose a 19 byte packet to be transmitted along with 3 byte maximum segment length network. Show the segment numbering systems of the packet. The packet number is 15. Transparent Fragmentation With transparent fragmentation, end hosts (sender and receiver) are unaware that fragmentation has taken place. A router fragments a packet, and the next-hop router on the same network reassembles the fragments back into the original packet. Non-Transparent Fragmentation: As before, routers fragment packets when needed. Routers along the path do not reassemble. Destination hosts perform re-assembly (if needed). (a) Transparent fragmentation. (b) Nontransparent fragmentation. 9. Explain briefly the functions of routing processor. • Routing processors have two functions: 1. Maintain and exchange routing data with other routers in the network Often this involves computing the forwarding table from data received by other routers 2. Use the forwarding table data to configure the switching fabric to forward the packet to the correct output port
- 6. 10. Describe briefly the construction of routers of different generation with necessary diagram. 1st Generation • This architecture is still used in low end routers • Arriving packets are copied to main memory via direct memory access (DMA) • Interconnection network is shared bus • All IP forwarding functions are performed in the central processor. • Routing cache at processor can accelerate the routing table lookup. 2nd Generation • Keeps shared bus architecture, but offloads most IP forwarding to interface cards • Interface cards have local route cache and processing elements Fast path: If routing entry is found in local cache, forward packet directly to outgoing interface Slow path: If routing table entry is not in cache, packet must be handled by central CPU 3rd Generation • Interconnection network is a switch fabric (e.g., a crossbar switch) • Distributed architecture: Memory Shared Bus DMA MAC DMA MAC Interface Card DMA MAC Route Processor Interface Card Interface Card CacheCPU Shared Bus Interface Cards DMA MAC DMA MAC DMA MAC Route Cache Memory Route Cache Memory Route Cache Memory Route Processor slow path fast path MemoryCacheCPU slow path fast path
- 7. – Interface cards operate independently of each other – No centralized processing for IP forwarding • These routers can be scaled to many hundred interface cards and to aggregate capacity of > 1 Terabit per second 11. Find the minimum spanning tree for the weighted graph in figure. https://www.youtube.com/watch?v=3isltkMwxEs 12. Describe the routing protocol for mobile host with necessary diagram. All hosts are assumed to have a permanent home location (home address) that never changes. Each area has one or more foreign agents (FA), keeping track of all mobile hosts (MH) visiting the area. Each area has a home agent (HA), which keep track of hosts whose home is in the area but are currently visiting another area. A WAN to which LANs, MANs, and wireless cells are attached • When a new host enters an area, it registers with the FA. – Each FA periodically announces its existence and address. The newly-arrived mobile host (MH) waits for one of these messages. If no message is received, it broadcasts a message and asks for FAs. – The MH sends its home address, link layer address, and some security info to the FA. Interface Cards CPU Memory Route Processor Memory Route Processing MAC Switch Fabric Interface Switch Fabric Memory Route Processing MAC Switch Fabric Interface
- 8. – The FA contracts the HA. – The HA examines the security info and records the temporary location of the MH. – The FA gets ACK from HA, and informs MH that it has been registered. Packet routing for mobile users 13. How can you define TCP/IP tunneling over ATM? Explain the categories of services that ATM provides. TCP/IP tunneling allows transmission of TCP/IP packets over ATM (and other non-TCP/IP) networks The use of TCP/IP over these networks allows applications which normally only run on TCP/IP networks to operate on all networks ATM provides 4 service categories: o CBR (Constant Bit Rate): A constant bandwidth is reserved and guaranteed by the network o UBR (Unspecified Bit Rate): Data is transmitted when bandwidth is available, and not when bandwidth is not available o ABR (Available Bit Rate): The network will provide feedback about network congestion, under the assumption the node will adjust its transmission to meet the current availability of network bandwidth o VBR (Variable Bit Rate): A minimum bandwidth is reserved and guaranteed by the network, although available bandwidth may increase/peak above this value RT (Real Time): Fluctuation of bandwidth is minimized Used for non-guaranteed streaming audio/video NRT (Non Real Time): Any bandwidth available is used Used for downloads 14. What is distance vector routing? Explain with example. Distance Vector Routing algorithm – Dynamic routing a. Each router maintains a table (vector), giving the best known distance to each destination and the outgoing line to get there. b. These tables are updated by exchanging information with the neighbors. c. The metric used might be the number of hops, the time delay, or the number of queued packets.
- 9. d. The router is assumed to know the “distance” to each of its neighbors. (a) A subnet. (b) Input from A, I, H, K, and the new routing table for J. 15. Explain the link state routing construction routing packets for a subnet. Link State Routing is a dynamic routing. Each router must do the following: a. Discover its neighbors, learn their network address. b. Measure the delay or cost to each of its neighbors. c. Construct a packet telling all it has just learned. d. Send this packet to all other routers. e. Compute the shortest path to every other router. (a) A subnet. (b) The link state packets for this subnet 16. Explain the hierarchical routing with necessary diagram. With the increase of network/routers, it is infeasible to have an entry for each router. The hierarchical routing is required. a. Divide the routers into regions. b. The router only knows details to route packets to the destination within the same region.
- 10. c. But may not be optimal (e.g., the best route from 1A to 5C is via region 2, but since the route via region 3 is better for most nodes in region 5. Hierarchical routing 17. Name and define the hardware components of a router. Show the routers functional components with diagram. Check number 3 answer. 18. What is ATM network? Define the logical connections used in ATM networks. ATM networks are packet-switched, but still create a (virtual) circuit through the network a. Before transfer can occur, the network must create a path (called a virtual circuit) between the two machines b. Once the virtual circuit (VC) has been established, packets can be transferred between the machines Use optical fiber similar to that used for FDDI networks - ATM runs on network hardware called SONET ATM cells (packets) are 53 octets long - 5 bytes of header information - 48 bytes of data Logical Connections: - VCC (Virtual Channel Connection): a logical connection analogous to virtual circuit in X.25 - VPC (Virtual Path Connection): a bundle of VCCs with same endpoints
- 11. 19. Explain ATM protocol architecture. Define ATM cell format. Fixed-size packets called cells Streamlined: minimal error and flow control 2 protocol layers relate to ATM functions: a. Common layer providing packet transfers b. Service dependent ATM adaptation layer (AAL) AAL maps other protocols to ATM Protocol model has three planes: • User • Control • management ATM Cell Format: Data Cells • Generic flow control: Control traffic flow. • Virtual path identifier: An identifier for the virtual path/circuit • Virtual channel identifier: An identifier to identify which channel within the specified virtual path/circuit • Payload Type: 3 flag bits • Cell loss priority: Should the cell be discarded in the event of a congested switch? • Header error check: Cyclical redundancy check for the cell header 20. Explain the way of creating ATM virtual circuits Creating a virtual circuit has been compared to making a telephone call A network node sends a request to the ATM switch specifying the destination
- 12. The switch interacts with any other switches necessary to align themselves to form a complete path When communication is complete, the node sends a disconnect message to the switch The switch will then notify all switches involved to release the connection 21. What do you mean by segmentation & reassembly in ATM network? Define ATM switching with necessary diagram. Segmentation: • Segmentation is the process of turning a chunk of data into a group of ATM cells – For example, the chunk of data might be a packet from another type of network • e.g. An Ethernet frame • Since ATM cells travel on the same virtual circuit, they do not arrive out of order – Thus sequencing information is not necessary • Each sequence of 48 octets is sent in its own cell Reassembly: • Reassembly is the process of recombining ATM cells into the original data chunk • As the destination node receives cells, it removes the 48 octets and appends it to the end of a buffer • One of the configuration parameters, called ‘Payload Type’ is used to indicate the final cell ATM Switching: • As can be seen in the diagram, ATM switches exist entirely in the hardware layer • As a result, they are much faster than routers, which require software execution – Routers must read packets from electronic signals into a memory buffer (which is slow) – Routers then convert packets back into electronic signals onto a new network connection 22. Write the drawbacks of ATM network. Small, finite sized cells provide faster transmission speeds - However, 53 octet cells are incompatible with other technologies which are in widespread use
- 13. ATM addressing also differs significantly from other forms of addressing - For example the TCP/IP protocol suite is the most common network protocol system - Most Internet applications are based on TCP/IP ATM networks are not broadcast networks - Each cell only arrives at its intended destination - Broadcasting & multicasting are not directly supported 23. Show the internetworking using concatenated virtual circuits and connectionless internetworking. Concatenated Virtual Circuits: a. A connection to a remote host is set up by concatenating virtual circuits in all networks it passes by. b. Gateways response for converting packet format and maintaining VC. c. Work best when all network have the same properties. i. All reliable or all unreliable. Can also be done on transport layer Internetworking using concatenated virtual circuits Connectionless internetworking: – inject datagram’s into subnets and hope for the best – packets may not follow the same route – Also works on VC subnet. A connectionless internet
- 14. 24. Name and define the network properties. Scope: A network should provide services to several applications Scalability: A network should operate efficiently when deployed on a small-scale as well as on a large- scale Robustness: A network should operate in spite of failures or lost data Self-Stabilization: A network, after a failure or other problem, should return to normal (or near normal) without human intervention Auto configurability: A network should optimize its own parameters in order to achieve better performance Safety: A network should prevent failures as well as prevent failures from affecting other areas of the network Configurability: A network’s parameters should be configurable to improve performance Determinism: Two networks with identical conditions should yield identical results Migration: It should be possible to add new features to a network without disruption of network service 25. Explain the TCP/IP protocol in action using a simplified network route. The TCP/IP Protocol in Action Consider the following simplified network route The source (S) and destination (D) are separated by two routers (R1, R2) S DR1 R2 51 The TCP/IP Protocol in Action Let’s consider a web browser, using HTTP The web browser on S sends a packet to the web server on D The application layer (i.e. the browser) provides the logical (IP) addresses for S (IPS) and D (IPD) The application layer also provides the port numbers for the source (PortS) and destination (PortD) S DR1 R2 HTTP Req 52 The TCP/IP Protocol in Action The Transport layer (TCP) uses the port numbers (e.g. 2765 and 80) to create a TCP packet (sometimes called a segment): S DR1 R2 Source Port: 2765 Destination Port: 80 HTTP Req 53 Source IP: 137.207.140.71 Dest IP: 24.87.204.16 The TCP/IP Protocol in Action The Internet (i.e. IP) layer uses the IP addresses specified by the application layer to create an IP datagram e.g. 137.207.140.71, 24.87.204.16 Next, a route is determined for the packet, using S’s routing table S only needs one router’s address (R1) S DR1 R2 TCP Segment HTTP Req 54
- 15. Source MAC: MACS Dest MAC: MACR1 IP Datagram The TCP/IP Protocol in Action The MAC addresses of S and R1 (MACS and MACR1) are used to create a network frame If the MAC address of R1 is not known, ARP (address resolution protocol) is used S DR1 R2 TCP Segment HTTP Req 55 Source MAC: MACS Dest MAC: MACR1 IP Datagram The TCP/IP Protocol in Action Let’s simplify the picture (for clarity) In subsequent steps the IP datagram and its contents will not change very much S DR1 R2 56 Source MAC: MACS Dest MAC: MACR1 IP Datagram The TCP/IP Protocol in Action The network frame is transmitted on the network to R1 This is possible since S and R1 are both members of the same network S DR1 R2 57 IP Datagram The TCP/IP Protocol in Action R1 will extract the IP datagram from the payload of the network frame R1 looks up the destination IP address (IPD) in it’s routing table, to determine which router should get the datagram next (R2) S DR1 R2 58 Source MAC: MACR1 Dest MAC: MACR2 IP Datagram The TCP/IP Protocol in Action R1 uses its own MAC address (MACR1) and R2’s MAC address (MACR2) to create another network frame S DR1 R2 59 Source MAC: MACR1 Dest MAC: MACR2 IP Datagram The TCP/IP Protocol in Action The network frame is received by R2, and the IP datagram is extracted from it’s payload R2 uses its routing table to lookup IPD In this case, R2 is directly connected to D This is called direct routing S DR1 R2 60 ARP Request IP: 24.87.204.16 MAC: ? IP Datagram The TCP/IP Protocol in Action Most likely, R2 does not have the MAC address of D (MACD) The address resolution protocol (ARP) is used to determine the MAC address: S DR1 R2 61 ARP Response IP: 24.87.204.16 MAC: 08-7F-3C-90-0C-DF IP Datagram The TCP/IP Protocol in Action D recognizes it’s IP address and responds with its MAC address (MACD) e.g. 08-7F-3C-90-0C-DF S DR1 R2 62
- 16. Source MAC: MACR2 Dest MAC: MACD IP Datagram The TCP/IP Protocol in Action A network frame is created by R2 now that the MAC address is known The frame is sent directly to D S DR1 R2 63 Source MAC: MACR2 Dest MAC: MACD IP Datagram The TCP/IP Protocol in Action D extracts the IP datagram from the network frame (which is discarded) The IP datagram’s payload is passed to the transport layer S DR1 R2 64 The TCP/IP Protocol in Action The Transport layer (within D’s operating system), will use the port numbers specified in the TCP segment to determine to which application it should send the segment In this case, to the application bound to port 80 (the web server) S DR1 R2 Source Port: 2765 Destination Port: 80 HTTP Req65 The TCP/IP Protocol in Action Now, the web server on D has the HTTP request, and it processes it An HTTP response is sent back using the same process The web server uses the same IP addresses and logical addresses as the last message S DR1 R2 HTTP Req 66 26. Name & define different types of network bridges. There are four types of network bridges: 1. Transparent basic bridge 2. Source routing bridge 3. Transparent learning bridge 4. Transparent spanning bridge The Transparent Basic Bridge The simplest type of bridge is the transparent basic bridge. It stores the traffic until it can transmit it to the next network. The amount of time the data is stored is very brief. Traffic is sent to all ports except the port from which the bridge received the data. No conversion of traffic is performed by a bridge. In this regard, the bridge is similar to a repeater. Source Routing Bridge The route through the LAN internet is determined by the source (originator) of the traffic hence this bridge is called as source routing bridge. The routing information field (RIF) in the LAN frame header, contains the information of route followed by the LAN network. The Transparent Learning Bridge The transparent bridge finds the location of user using the source and destination address. When the frame is received at the bridge it checks its source address and the destination address. The destination address is stored if it was not found in a routing table. Then the frame sent to all LAN excluding the LAN from which it came. The source address is also stored in the routing table. If another frame is arrived in which the previous source address is now its destination address then it is forwarded to that port.
- 17. The Transparent Spanning Tree Bridge These bridges use a subnet of the full topology to create a loop free operation. 27. Short notes on routers input buffer, output buffer, processor, switching fabric. Input Buffer: The incoming packets of a network interface are placed in input buffers These are banks of very high speed memory for packet queuing prior to processing The packet is stored here until the routing processor is available The network interface may have a routing processor, which would: a. have a copy of the forwarding table (to prevent concurrent access) b. lookup the destination address in this forwarding table, to determine the correct output port c. configure the switching fabric to forward the packet to the correct output buffer Low-end routers would share one routing processor Output Buffer: The switching fabric gets the packet to the right output port However, that port’s network may not be immediately available The packets are stored in the output buffer until the network is available Routing Processor: • A routing processor is software which executes on a CPU: – Off-the-shelf CPU • These are very inexpensive • However, the performance of these CPUs is low since they are not optimized for the types of operations a router typically needs to perform – Application-Specific Integrated Circuit (ASIC) • These are expensive to design (time and money) • They are optimized for typical routing operations • High-end routers use these to achieve higher performance levels Switching Fabric: • Switching fabric’s job is to move packets from the input buffer into the correct output buffer – The routing processor determines the correct output port, using the forwarding table • Switching fabric comes in 3 major types: – In-memory switching fabric: • The packets are input into the routing processor’s memory, and output into the correct output buffer – Bus-based switching fabric:
- 18. • The packets move along a shared bus (similar to a network bus) to the correct output buffer – Crossbar switching fabric: • The packets move along a grid of redundant buses • If any bus fails, alternate paths exist so that forwarding can continue 28. What is switching? Write the reasons for switching in communication. The establishing, on-demand, of an individual connection from a desired inlet to a desired outlet within a set of inlets and outlets for as long as is required for the transfer of information. Switching implies directing of information flows in communications networks based on known rules Switching takes place in specialized network nodes Data switched on bit, octet, frame or packet level Size of a switched data unit is variable or fixed Reasons for switching in communication: Switches allow reduction in overall network cost by reducing number and/or cost of transmission links required to enable a given user population to communicate Limited number of physical connections implies need for sharing of transport resources, which means better utilization of transport capacity use of switching Switching systems are central components in communications networks 29. Describe the main building block of a switch. Define basic type of switching networks.
- 19. 30. Explain different types of switching modes. Define label switching. Types of switching modes: • Circuit switching • Cell switching • Packet switching – Routing – Layer 3 - 7 switching – Label switching Circuit Switching: End-to-end circuit established for a connection Signaling used to set-up, maintain and release circuits Circuit offers constant bit rate and constant transport delay Equal quality offered to all connections Transport capacity of a circuit cannot be shared Applied in conventional telecommunications networks (e.g. PDH/PCM and N-ISDN) Cell switching: • Virtual circuit (VC) established for a connection • Data transported in fixed length frames (cells), which carry information needed for routing cells along established VCs • Forwarding tables in network nodes • Signaling used to set-up, maintain and release VCs as well as update forwarding tables • VCs offer constant or variable bit rates and transport delay • Transport capacity of links shared by a number of connections (statistical multiplexing) • Different quality classes supported • Applied, e.g. in ATM networks Packet switching: No special transport path established for a connection Variable length data packets carry information used by network nodes in making forwarding decisions No signaling needed for connection setup
- 20. Forwarding tables in network nodes are updated by routing protocols No guarantees for bit rate or transport delay Best effort service for all connections in conventional packet switched networks Transport capacity of links shared effectively Applied in IP (Internet Protocol) based networks Label Switching: Evolved from the need to speed up connectionless packet switching and utilize L2-switching in packet forwarding A label switched path (LSP) established for a connection Forwarding tables in network nodes Signaling used to set-up, maintain and release LSPs A label is inserted in front of a L3 packet (behind L2 frame header) Packets forwarded along established LSPs by using labels in L2 frames Quality of service supported Applied, e.g. in ATM, Ethernet and PPP Generalized label switching scheme (GMPLS) extends MPLS to be applied also in optical networks, i.e., enables light waves to be used as LSPs
