Computer Networking Lab File
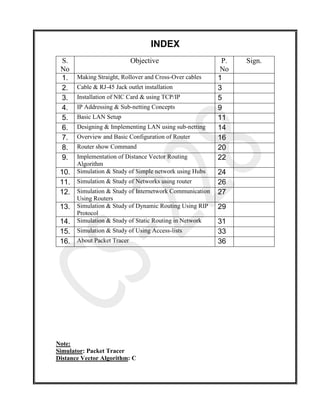
- 1. INDEX S. No Objective P. No Sign. 1. Making Straight, Rollover and Cross-Over cables 1 2. Cable & RJ-45 Jack outlet installation 3 3. Installation of NIC Card & using TCP/IP 5 4. IP Addressing & Sub-netting Concepts 9 5. Basic LAN Setup 11 6. Designing & Implementing LAN using sub-netting 14 7. Overview and Basic Configuration of Router 16 8. Router show Command 20 9. Implementation of Distance Vector Routing Algorithm 22 10. Simulation & Study of Simple network using Hubs 24 11. Simulation & Study of Networks using router 26 12. Simulation & Study of Internetwork Communication Using Routers 27 13. Simulation & Study of Dynamic Routing Using RIP Protocol 29 14. Simulation & Study of Static Routing in Network 31 15. Simulation & Study of Using Access-lists 33 16. About Packet Tracer 36 Note: Simulator: Packet Tracer Distance Vector Algorithm: C
- 2. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 1 EXPERIMENT-1 : Making Straight, Rollover and Cross-Over cables Straight Over: A straight through network cable acts as an extension enabling a device with a network interface card to be attached to a network. A common form of network media is the UTP Cat5 (Unshielded Twisted Pair Category 5) cable. The cables should have their sleeving trimmed back at each end by approximately 13mm in order to expose the wires for sorting. The wires should then be flattened out and sorted into the following order from left to right; White/Orange, Orange, White/Green, Blue, White/Blue, Green, White/Brown, Brown. At this point it is best to make sure that the wires are the same length and trim them as necessary. It’s a good idea to check the order of the wires before moving onto the next stage to make sure that orange and brown have not been mixed up as some white wires don’t have their markings coloured clearly. Once the wires are confirmed to be in the correct order then it is time to attach the RJ-45 connectors. This is a simple case of pushing the wires in as far as they will go and then using a crimping tool to secure them into place. Once one end is done simply repeat the process for the second end, after that be sure to test the cable with an appropriate device before using it in your network. RJ-45 connectors are the most common form of connectors used on UTP Cat5 cables. The RJ simply means Registered Jack and the 45 designation specifies the pin numbering scheme. The cable itself contains 4 twisted pairs of wires making a total of 8 wires. Roll Over: Crossover wired cables (commonly called crossover cables) are very much like Straight-Through cables with the exception that TX and RX lines are crossed (they are at opposite positions on either end of the cable. Using the 568-B standard as an example below you will see that Pin 1 on connector A goes to Pin 3 on connector B. Pin 2 on connector A goes to Pin 6 on connector B etc. Crossover cables are most commonly used to connect two hosts directly. Examples would be
- 3. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 2 connecting a computer directly to another computer, connecting a switch directly to another switch, or connecting a router to a router. Cross Over: Crossover wired cables (commonly called crossover cables) are very much like Straight-Through cables with the exception that TX and RX lines are crossed (they are at opposite positions on either end of the cable. Using the 568-B standard as an example below you will see that Pin 1 on connector A goes to Pin 3 on connector B. Pin 2 on connector A goes to Pin 6 on connector B etc. Crossover cables are most commonly used to connect two hosts directly. Examples would be connecting a computer directly to another computer, connecting a switch directly to another switch, or connecting a router to a router.
- 4. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 3 EXPERIMENT-2 : Cable & RJ-45 Jack outlet installation Do not strip the insulation off of the individual paired wires. Just remove about 40mm of the jacket as shown below photo 1. The way the stripper tool works is the cable is inserted into the stripper and then the stripper is rotated a couple of times allowing the tools cutting blade to score the cable‘s outer jacket only. BE CAREFUL NOT TO CUT THROUGH ANY COLOURED WIRES. Untwist the twisted paired wires. Then arrange them in the correct order. Use guide below to arranging the wire colours in the proper order Diagram c. Get the eight wires arranged in the proper order and pressing the eight wires FLAT between your thumb and index fingers is an important step to get the wires setup to slide into the RJ45 connector. Once the wires are FLAT and in the right order cut them so they are 13mm long as shown in the photo 4 Insert the flattened wire into the the RJ45 connector as shown photo 5. Put your RJ45 crimping tool to work. Read the directions for your tool. Drawing B below shows what the crimp tool is doing. The crimp tool presses in the gold plated electrical contact down such that they pierce through insulation of all eight wire and make contact with the copper conductor. This is called insulation displacement hence no need to strip the insulation off of the individual wires. The crimp tool presses down on a hinged tab that grips onto the cables outer jacket to provide a strain relief action and helps to keep the cable and the connector intact. See diagrams A and B PIN COLOUR PAIR NAME 1 Orange/White 2 Transmit Data + 2 Orange 2 Transmit Data - 3 white/Green 3 Receive Data + 4 Blue 1 Not Used-POE 5 White/Blue 1 Not Used-POE 6 Green 3 Receive Data - 7 White/ Brown 4 Not Used-POE 8 Brown 4 Not Used-POE 1. Fit Boot - Expose 40mm Wires 2. Straighten Wires Put in Order
- 5. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 4 3. Use Crimper to Trim Wires 4. Trim to 13mm 5. Insert into RJ45 Connector 6. Crimp Cable to RJ45 Connector 7. Completed Connection (Action Of Crimping Tool)
- 6. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 5 EXPERIMENT-3: Installation of NIC Card & using TCP/IP Network adapters are hardware devices, such as network interface cards, that are used to communicate on networks. We can install and configure network adapters by doing the following: Configure the network adapter card following the manufacturer's instructions. For example, we may need to set jumpers on the adapter board. Disconnect the computer and unplug it, then install the adapter board into the appropriate slot on the computer. When we're finished, boot the system. Tell Windows NT about the new network adapter card by means of the Network Control Panel utility. Start the utility by double-clicking on the Network icon in the Control Panel. Select the Adapters tab to display the dialog box shown in Figure. The fields of this tab areused as follows: Network Adapters Shows the currently installed network adapters. Add Adds network adapters to the system. Remove Removes network adapters. Properties Sets the properties of the currently selected network adapter. Update Updates the drivers for an adapter card. If we have difficulty updating an adapter's drivers, we may want to remove the adapter and then put it back. This ensures that the adapter's new drivers are properly installed. Item Notes Shows additional information for the currently selected adapter. Figure: The Adapter Properties dialog box lets us change the adapter's basic settings and test it. The test only works if we have installed the TCP/IP protocol service. If the new network adapter isn't shown in the Network Adapters list box, click on the Add button. Using the Select Network Adapter dialog box, select the appropriate network adapter. Ifwe don't see the adapter we installed, click on the Have Disk button and insert the adapter's installation disk when prompted.
- 7. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 6 Note: Adding the adapter also installs the drivers for the adapter. Because of this, be sure that you use the correct installation disk. The dialog boxwe see next depends on the type of adapter we're installing. With most network interface cards, we see the Adapter Properties dialog box shown in Figure. Click on the Change button, then configure the adapter's basic settings, such as network speed and duplex mode. If we've already configured the TCP/IP protocol service and the computer is attached to the network, you can use the Test button to test the network card. Click OK to continue. Close the Network properties dialog box by clicking on the Close button. Windows NT installs the network bindings for the network adapter. Afterward, if TCP/IP is installed on the computer, we'll see the Microsoft TCP/IP Properties dialog box. We use this dialog box to configure the TCP/IP protocol service as detailed in the section of this chapter titled "Configuring TCP/IP Networking." Change TCP/IP settings TCP/IP defines how your computer communicates with other computers. To make it easier to manage TCP/IP settings, we recommend using automated Dynamic Host Configuration Protocol (DHCP). DHCP automatically assigns Internet Protocol (IP) addresses to the computers on your network, if your network supports it. If you use DHCP, then you don't have to change your TCP/IP settings if you move your computer to another location, and DHCP doesn't require you to manually configure TCP/IP settings, such as Domain Name System (DNS) and Windows Internet Name Service (WINS). To enable DHCP or change other TCP/IP settings, follow these steps: 1. Open Network Connections by clicking the Start button , and then clicking Control Panel. In the search box, type adapter, and then, under Network and Sharing Center, click View network connections. 2. Right-click the connection that you want to change, and then click Properties. If you're prompted for an administrator password or confirmation, type the password or provide confirmation. 3. Click the Networking tab. Under This connection uses the following items, click either Internet Protocol Version 4 (TCP/IPv4) or Internet Protocol Version 6 (TCP/IPv6), and then click Properties.
- 8. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 7 The Network Connection Properties dialog box 4. To specify IPv4 IP address settings, do one of the following: To get IP settings automatically using DHCP, click Obtain an IP address automatically, and then click OK. To specify an IP address, click Use the following IP address, and then, in the IP address, Subnet mask, and Default gateway boxes, type the IP address settings. 5. To specify IPv6 IP address settings, do one of the following: To get IP settings automatically using DHCP, click Obtain an IPv6 address automatically, and then click OK. To specify an IP address, click Use the following IPv6 address, and then, in the IPv6 address, Subnet prefix length, and Default gateway boxes, type the IP address settings. 6. To specify DNS server address settings, do one of the following: To get a DNS server address automatically using DHCP, click Obtain DNS server address automatically, and then click OK.
- 9. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 8 To specify a DNS server address, click Use the following DNS server addresses, and then, in the Preferred DNS server and Alternate DNS server boxes, type the addresses of the primary and secondary DNS servers. The Internet Protocol Version 4 (TCP/IPv4) Properties dialog box 7. To change advanced DNS, WINS, and IP settings, click Advanced.
- 10. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 9 EXPERIMENT-4: IP Addressing & Sub-netting Concepts Introduction to IP addressing: Each Network Interface Card (NIC or Network card) present in a PC is assigned one Network address called as IP address [or Network address]. This IP address is assigned by the administrator of the network. No two PCs can have the same IP address. There is a burned-in address on the NIC called as Physical Address [or MAC address or Hardware address]. The MAC address of a network card indicates the vendor of that card and a unique serial number. Rules of IPv4 addressing: 1. Format of IP address IPv4 is made up of four parts, in the pattern as w.x.y.z. Each part has 8 binary bits and the values in decimal can range from 0 to 255. 2. IP address classes IP addresses are divided into different classes. These classes determine the maximum number of hosts per network ID. Only three classes are actually used for network connectivity. The following table lists all of the address class. IP address class Value of the leftmost byte Class A 1-126 [0 and 127 are not allowed] Class B 128-191 Class C 192-223 3. Grouping of IP addresses into different classes. a. Class A: first bit in w is 0 and others can be anything i. 0.0.0.0 to 127.255.255.255 ii. First bits are used for network part and the remaining for host part. b. Class B: First bit in w is 1 and second bit is 0. i. 128.0.0.0 to 191.255.255.255 ii. First 16 bits for network part and remaining host part c. Class C: first bit in w is 1, second bit in w is 1 and third bit is 0 i. 192.0.0.0 to 223.255.255.255 ii. First 24 bits for network part and last 8 bits for host part. d. Class D: first, second, third bits in w are 1 and fourth bit is 0; used for multicast. i. 224.0.0.0 to 247.255.255.255 e. Class E: future use or experimental purposes. 4. Default Subnet mask it is used to identify the network part from the host part. Put binary one for the parts that represent network part and zero for the part that represent host part.
- 11. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 10 a. Class A: 255.0.0.0 b. Class B: 255.255.0.0 c. Class C: 255.255.255.0 d. We can’t have mix of 1s and 0s in subnet mask. Only consecutive 1s is followed by consecutive 0s Class A 1.0.0.1 to 126.255.255.254 Supports 16 million hosts on each of 127 networks. Class B 128.1.0.1 to 191.255.255.254 Supports 65,000 hosts on each of 16,000 networks. Class C 192.0.1.1 to 223.255.254.254 Supports 254 hosts on each of 2 million networks. Class D 224.0.0.0 to 239.255.255.255 Reserved for multicast groups. Class E 240.0.0.0 to 254.255.255.254 Reserved. 5. Invalid IP address. a. If the network part is all 0s, the address belongs to class A. But this is an invalid ip address because for an IP address all the network or host part should not be all 1s or all 0s. i. 0.0.0.0 is not valid. Routers use it internally. b. If the network part is all 1s, this address belongs to class E. But due to presence of all 1s, it is not valid. This represent broadcast to all networks. i. 255.255.255.255 is not valid. c. If the host part is all 0s, this represents network address. This is not a valid IP address. d. If the host part is all 1s, this represents broadcast address. This is not a valid IP address. e. We can‘t use the IP address represented within private address range as part of public IP address. i. Class A: 10.0.0.0 to 10.255.255.255 ii. Class B: 172.16.0.0 to 172.31.255.255 iii. Class C: 192.168.0.0 to 192.168.255.255 f. 127.0.0.0 network address is used for loop-back testing. This will help you to check the network card of your own PC [local host]. . 6. Default subnet masks for standard IP address classes The following table lists the default subnet masks for each available class of TCP/IP networks. Address Class Bits for Subnet Mask Subnet Mask Class A 11111111 00000000 00000000 00000000 255.0.0.0 Class B 11111111 11111111 00000000 00000000 255.255.0.0 Class C 11111111 11111111 11111111 00000000 255.255.255.0
- 12. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 11 EXPERIMENT-5: Basic LAN Setup(Between Two PC’s) Procedure: On the host computer On the host computer, follow these steps to share the Internet connection: 1. Log on to the host computer as Administrator or as Owner. 2. Click Start, and then click Control Panel. 3. Click Network and Internet Connections. 4. Click Network Connections. 5. Right-click the connection that you use to connect to the Internet. For example, if you connect to the Internet by using a modem, right-click the connection that you want under Dial-up / other network available. 6. Click Properties. 7. Click the Advanced tab. 8. Under Internet Connection Sharing, select the Allow other network users to connect through this computer's Internet connection check box.
- 13. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 12 9. If you are sharing a dial-up Internet connection, select the Establish a dial-up connection whenever a computer on my network attempts to access the Internet check box if you want to permit your computer to automatically connect to the Internet. 10. Click OK. You receive the following message: When Internet Connection Sharing is enabled, your LAN adapter will be set to use IP address 192.168.0.1. Your computer may lose connectivity with other computers on your network. If these other computers have static IP addresses, it is a good idea to set them to obtain their IP addresses automatically. Are you sure you want to enable Internet Connection Sharing? 11. Click Yes. The connection to the Internet is shared to other computers on the local area network (LAN). The network adapter that is connected to the LAN is configured with a static IP address of 192.168.0.1 and a subnet mask of 255.255.255.0 On the client computer To connect to the Internet by using the shared connection, you must confirm the LAN adapter IP configuration, and then configure the client computer. To confirm the LAN adapter IP configuration, follow these steps: 1. Log on to the client computer as Administrator or as Owner. 2. Click Start, and then click Control Panel. 3. Click Network and Internet Connections. 4. Click Network Connections. 5. Right-click Local Area Connection and then click Properties. 6. Click the General tab, click Internet Protocol (TCP/IP) in the connection uses the following items list, and then click Properties. 7. In the Internet Protocol (TCP/IP) Properties dialog box, click Obtain an IP address
- 14. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 13 automatically (if it is not already selected), and then click OK. Note: You can also assign a unique static IP address in the range of 192.168.0.2 to 192.168.0.254. For example, you can assign the following static IP address, subnet mask, and default gateway: 8. IP Address 192.168.1.1 9. Subnet mask 255.255.255.0 10. Default gateway 192.168.31.1 11. In the Local Area Connection Properties dialog box, click OK.
- 15. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 14 EXPERIMENT-6: Designing & Implementing LAN using sub-netting Subnetting: Subnetting allows you to create multiple logical networks that exist within a single Class A, B, or C network. If you do not subnet, you are only able to use one network from your Class A, B, or C network, which is unrealistic. If an organization needs to allocate its ip addresses so that each department in it has its own network so that there is no interference of one department with other, subnetting is the solution. Steps involved in subnetting are:- • Open control panel • Go to network and sharing centre • Click on ‗change adapter settings‘ • You might have more than one Internet connection listed here. You will need to determine which adapter is your connection to the Internet if this is the case. Right click on your network adapter and choose properties to open up the properties window of this internet connection. • Click Internet Protocol Version 4(TCP/IPv4) and then the Properties button • By default you will see the class C subnet mask 255.255.255.0. Since the last byte contains all 0‘s i.e. there is no subnet bit(1‘s), you will have only one network and 28-2 hosts in this network. To subnet, you will need to add 1‘s in the last byte which will depend on the need of your organization. e.g If an organization needs 4 subnetworks with 57 pc‘s in each, you will set the first two bits of the last byte to 1(since 22=4 networks).
- 16. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 15 Hence your subnet mask will be 255.255.255.192 • You repeat the above steps for each host in the network. You can check your configuration settings by typing ipconfig command in cmd • In the end you can test your connections by pinging them.
- 17. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 16 EXPERIMENT-7: Overview and Basic Configuration of Router CONFIGURE COMMANDS Command Purpose Step 1 enable Example: Router> enable Enables privileged EXEC mode. • Enter your password if prompted. Step 2 configure terminal Example: Router# configure terminal Enters global configuration mode. Configuring Global Commands To configure selected global parameters for your router, perform these steps: SUMMARY STEPS 1. configure terminal 2. hostname name 3. enable secret password DETAILED STEPS Command Purpose Step 1 configure terminal Example: Router# configure terminal Enters global configuration mode when using the console port. If you are connecting to the router using a remote terminal, use the following: telnet router name or address Login: login id Password: ********* Router> enable Step 2 hostname name Example: Router(config)# hostname Router Specifies the name for the router. Step 3 enable secret password Example: Router(config)# enable secret cr1ny5ho Specifies an encrypted password to prevent unauthorized access to the router. EXAMPLE Router#config t Enter configuration commands, one per line. End with CNTL/Z. Router(config)#service password-encryption
- 18. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 17 Router(config)#enable password nit Router(config)#line vty 0 197 Router(config-line)#login Router(config-line)#password nit2 Router(config-line)#line con 0 Router(config-line)#login Router(config-line)#password nit1 Router(config-line)#line aux 0 Router(config-line)#login Router(config-line)#password nit Router(config-line)#exit Router(config)#no service password-encryption Router(config)#^Z Configuring Fast Ethernet To configure the Fast Ethernet interface on a Cisco 861 or 881 ISR, perform these steps, beginning in global configuration mode: SUMMARY STEPS 1. interface type number 2. ip address ip-address mask 3. no shutdown 4. exit DETAILED STEPS Command Purpose Step 1 interface type number Example: Router(config)# interface fastethernet 0/0 Enters the configuration mode for a Fast Ethernet WAN interface on the router. Step 2 ip address ip-address mask Example: Router(config-if)# ip address 192.168.12.2 255.255.255.0 Sets the IP address and subnet mask for the specified Fast Ethernet interface. Step 3 no shutdown Example: Router(config-if)# no shutdown Enables the Ethernet interface, changing its state from administratively down to administratively up. Step 4 exit Example: Router(config-if)# exit Router(config)# Exits configuration mode for the Fast Ethernet interface and returns to global configuration mode. Configuring Static Routes Static routes provide fixed routing paths through the network. They are manually configured on the router. If the network topology changes, the static route must be updated with a new route. Static routes are private routes unless they are redistributed by a routing protocol. Follow these steps to configure static routes, beginning in global configuration mode.
- 19. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 18 SUMMARY STEPS 1. ip route prefix mask {ip-address | interface-type interface-number [ip-address]} 2. end DETAILED STEPS Command Purpose Step 1 ip route prefix mask {ip-address |interface- type interface-number [ip-address]} Example: Router(config)# ip route 192.168.1.0 255.255.0.0 10.10.10.2 Specifies the static route for the IP packets. Step 2 end Example: Router(config)# end Router# Exits router configuration mode, and enters privileged EXEC mode. BASIC CONFIGURATION COMMANDS REQUIREMENT CISCO COMMAND Set a console password Router(config)#line con 0 Router(config-line)#login Router(config-line)#password cisco Set a telnet password Router(config)#line vty 0 4 Router(config-line)#login Router(config-line)#password cisco Set the enable password to cisco Router(config)#enable password cisco Set the enable secret password to peter. This password overrides the enable password and is encypted within the config file Router(config)#enable secret peter Enable an interface Router(config-if)#no shutdown To disable an interface Router(config-if)#shutdown Set the clock rate for a router with a DCE cable to 64K Router(config-if)clock rate 64000
- 20. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 19 To add an IP address to a interface Router(config-if)#ip addr 10.1.1.1 255.255.255.0 To enable RIP on all 172.16.x.y interfaces Router(config)#router rip Router(config-router)#network 172.16.0.0 Disable RIP Router(config)#no router rip Static route the remote network is 172.16.1.0, with a mask of 255.255.255.0, the next hop is 172.16.2.1, at a cost of 5 hops Router(config)#ip route 172.16.1.0 255.255.255.0 172.16.2.1 5
- 21. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 20 EXPERIMENT-8: Router Show Command 1) Sh ip route: The command show ip route shows the IP routing table, the metric used, and the interface used to find a remote network. 2) Sh ip int brief: This command displays a brief summary of the interfaces on a device. Its useful for quickly checking the status of the device.
- 22. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 21 3) Sh ip rip database: To display summary address entries in the Routing Information Protocol (RIP) routing database entries if relevant are routes being summarized based upon a summary address, use the show ip rip database command in privileged EXEC mode. show ip rip database [ip-address mask] 4) Sh access- lists: Displays all access lists and their parameters configured on the router. This command doesn't show which interface the list is configured on. 5) Sh access-lists: Shows only the parameters for the access list specified. This command does not show you the interface the list is configured on. Eg: Router#sh access-lists 101 Extended IP access list 101 deny icmp host 10.10.10.21 host 10.10.10.6 echo permit icmp any any echo
- 23. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 22 EXPERIMENT-9:Implementation of Distance Vector Routing Algorithm #include<stdio.h> #include<conio.h> struct node { unsigned dist[20]; unsigned from[20]; }rt[10]; int main() { int costmat[20][20]; int nodes,i,j,k,count=0; printf("nEnter the number of nodes : "); scanf("%d",&nodes);//Enter the nodes printf("nEnter the cost matrix :n"); for(i=0;i<nodes;i++) { for(j=0;j<nodes;j++) { scanf("%d",&costmat[i][j]); costmat[i][i]=0; rt[i].dist[j]=costmat[i][j];//initialise the distance equal to cost matrix rt[i].from[j]=j; } } do { count=0; for(i=0;i<nodes;i++) for(j=0;j<nodes;j++) for(k=0;k<nodes;k++) if(rt[i].dist[j]>costmat[i][k]+rt[k].dist[j]) { rt[i].dist[j]=rt[i].dist[k]+rt[k].dist[j]; rt[i].from[j]=k; count++; } }while(count!=0); for(i=0;i<nodes;i++) { printf("nn For router %dn",i+1); for(j=0;j<nodes;j++) { printf("tnnode %d via %d Distance %d ",j+1,rt[i].from[j]+1,rt[i].dist[j]); } } }
- 24. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 23 INPUT GRAPH: (Router 2) (Router 3) (Router 1) (Router 4) (Router 5) OUTPUT:
- 25. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 24 EXPERIMENT-10: Simulation & Study of Simple network using Hubs 4-port Ethernet hub An Ethernet hub, active hub, network hub, repeater hub or hub is a device for connecting multiple twisted pair or fiber optic Ethernet devices together and making them act as a single network segment. Hubs work at the physical layer (layer 1) of the OSI model. The device is a form of multiport repeater. Repeater hubs also participate in collision detection, forwarding a jam signal to all ports if it detects a collision. Hubs also often come with a BNC and/or Attachment Unit Interface (AUI) connector to allow connection to legacy 10BASE2 or 10BASE5 network segments. The availability of low-priced network switches has largely rendered hubs obsolete but they are still seen in older installations and more specialized applications. Technical information: A network hub is a fairly unsophisticated broadcast device. Hubs do not manage any of the traffic that comes through them, and any packet entering any port is regenerated and broadcast out on all other ports. Since every packet is being sent out through all other ports, packet collisions result—which greatly impedes the smooth flow of traffic. Hubs are classified as Layer 1 (physical layer) devices in the OSI model. At the physical layer, hubs support little in the way of sophisticated networking. Hubs do not read any of the data passing through them and are not aware of their source or destination. A hub simply receives incoming Ethernet frames, regenerates the electrical signal, and broadcasts these packets out to all other devices on the network
- 26. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 25 PINGING PC0 with LAPTOP1
- 27. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 26 EXPERIMENT-11: Simulation & Study of Networks using router Routing is used for taking a packet from one device and sending it through the network to another device on a different network. If your network has no routers, then you are not routing. Routers route traffic to all the networks in your internetwork. To be able to route packets, a router must know, at a minimum, the following: (i) Destination address (ii) Neighbor routers from which it can learn about remote networks (iii) Possible routes to all remote networks (iv) The best route to each remote network (v) How to maintain and verify routing information _ Global configuration (config): To configure any feature of the router, you must enter configuration mode. This is the first sub-mode of the parent mode. In the parent mode, issue the command config terminal. Router#config terminal Router(config)# Configuring interfaces: To display the configuration of the interface you use the command: r1#show interface fastethernet 0/0 r1#show interface serial 1/0 Here is an example of configuring a fastethernet port with an IP address: r1#config r1(config)#interface fastethernet 1/0 r1(config-if)#ip address 10.10.10.5 255.255.255.252 r1(config-if)#no shutdown PINGING LAPTOP 2 with LAPTOP1
- 28. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 27 EXPERIMENT-12: Simulation & Study of Internetwork Communication Using Routers Configure the Router : 1.To connect to the router, you need to assign an IP address for each interface of the router. When we get a new router, we use console cable to assign an IP address and then connect via telnet. 2. We need to assign an IP address for both the fast Ethernet interface cards. We should be privileged mode. An example is given below: #config t (config)# interface FastEthernet 0/0 → configure Ethernet interface 0/0 (config-if)#ip address 10.10.10.1 255.255.255.252 →IP address and the subnet mask. (config-if)#no shut (or no shutdown) → ensure that interface is not administratively down (config-if)#ctrl-z (or exit) → execute all of the above and return to parent 3. Now the connection between networks connected via a single router should work. We can ping among 10.10.10.1/30 & 10.10.10.2/30 network and between 10.10.10.5/30 & 10.10.10.6/30 networks and soo on... 4. All the hosts can connect to the router using telnet. You can telnet to the respective gateway address. The routing table at this time can be viewed using show ip route 5. Now we need to assign an IP address for the Serial interface. We should be at the privileged mode. #config t (config)# interface Serial 1/0 → configure Serial interface 1/0 (config-if)#ip address 10.10.10.30 255.255.255.252 (config-if)#no shutdown (or no shut) (config-if)#bandwidth 64 (config-if)#clock rate 64000will work only with DCE connections (config-if)#ctrl-z (or exit) → execute all of the above and return to parent 6.From the hosts, the users should be able to ping to IP address of the serial interface present in the router connected to their network. 7.All the necessary IP address setups are done. We need to enable routing protocols to have the necessary routing among the networks connected to different routers. To setup the RIP protocol, we do as below: # config t (config)# router rip (config-router)# network 10.10.10.0 Note: We need to add the network entries for the serial connection that connects different routers. We need to add entry for all the directly connected networks [both fastethernet and serial]. 8.All the necessary connections are done and all the hosts should be able to ping other hosts present in different networks. Show ip route command will show that routes are learnt using RIP protocol.
- 29. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 28 PINGING LAPTOP 2 with PC0 :PATH followed By packet From LAPTOP2 to PC0 Using DYNAMIC Routing
- 30. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 29 EXPERIMENT-13: Simulation & Study of Dynamic Routing Using RIP Protocol OPERATIONS OF DYNAMIC PROTOCOL: 1. The router sends and receives routing messages on its interfaces. 2. The router shares routing messages and routing information with other routers that are using the same routing protocol. 3. Routers exchange routing information to learn about remote networks. 4. When a router detects a topology change, the routing protocol can advertise this change to other routers. Role of Dynamic Routing Protocol: Routing protocols are used to facilitate the exchange of routing information between routers. Routing protocols allow routers to dynamically learn information about remote networks and automatically add this information to their own routing tables Routing protocols determine the best path to each network, which is then added to the routing table. One of the primary benefits of using a dynamic routing protocol is that routers exchange routing information whenever there is a topology change. This exchange allows routers to automatically learn about new networks and also to find alternate paths if there is a link failure to a current network. Compared to static routing, dynamic routing protocols require less administrative overhead. However, the expense of using dynamic routing protocols is dedicating part of a router‘s resources for protocol operation, including CPU time and network link bandwidth.
- 31. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 30 Figure : Shows the RIP table for Router0: Dynamic Routing Advantages and Disadvantages: Dynamic routing advantages are as follows: ■ Administrator has less work in maintaining the configuration when adding or deleting networks. ■ Protocols automatically react to the topology changes. ■ Configuration is less error-prone. ■ More scalable; growing the network usually does not present a problem. Dynamic routing disadvantages are as follows: ■ Router resources are used (CPU cycles, memory, and link bandwidth). ■ More administrator knowledge is required for configuration, verification, and troubleshooting.
- 32. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 31 EXPERIMENT-14: Simulation & Study of Static Routing in Network Static routing occurs when you manually add routes in each router's routing table. Static routing is the term used to refer to a manual method that is used to set up routing between networks. The network administrator configures static routes in a router by entering routes directly into the routing table of a router. Static routing has the advantage of being predictable and simple to set up. It is easy to manage in small networks but does not scale well. Static routing has the following advantages: 1) There is no overhead on the router CPU. 2) There is no bandwidth usage between routers. 3) It adds security because the administrator can choose to allow routing access to certain networks only. Static routing has the following disadvantages: 1) The administrator must really understand the internetwork and how each router is connected in order to configure routes correctly. 2) If a network is added to the internetwork, the administrator has to add a route to it on all routers— manually. 3) It's not possible in large networks because maintaining it would be a full-time job in itself. Command syntax for static route: ip route [destination_network] [mask] [next-hop_address or exit_interface] [administrative_distance] [permanent] ip route: The command used to create the static route. destination_network: The network you're placing in the routing table. mask: The subnet mask being used on the network. next-hop_address: The address of the next-hop router that will receive the packet and forward it to the remote network. exit_interface: Used in place of the next-hop address if you want, and shows up as a directly connected route. administrative_distance: By default, static routes have an administrative distance of 1 (or even 0 if you use an exit interface instead of a next-hop address). permanent Keyword (Optional): Without the permanent keyword in a static route statement, a static route will be removed if an interface goes down. Adding the permanent keyword to a static route statement will keep the static routes in the routing table even if the interface goes down and the directly connected networks are removed. Router>enable Router#config t Enter configuration commands, one per line. End with CNTL/Z. Router(config)#ip route 10.10.10.0 255.255.255.252 10.10.10.33 Router(config)# (For Router3)
- 33. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 32 :PATH followed By packet From LAPTOP2 to PC0 Using Static Routing
- 34. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 33 EXPERIMENT-15: Simulation & Study of Using Access-lists :PATH followed By packet From LAPTOP2 to PC1 Using Access Lists Access lists are essentially lists of conditions that control access. They‘re powerful tools that control access both to and from network segments. They can filter unwanted packets and be used to implement security policies. With the right combination of access lists, network managers willbe armed with the power to enforce nearly any access policy they can invent. There are a few important rules a packet follows when it‘s being compared with an access list: 1) It‘s always compared with each line of the access list in sequential order, i.e., it‘ll always start with line 1, then go to line 2, then line 3, and so on. 2) It‘s compared with lines of the access list only until a match is made. Once the packet matches a line of the access list, it‘s acted upon, and no further comparisons take place. 3) There is an implicit ―deny‖ at the end of each access list—this means that if a packet doesn‘t match up to any lines in the access list, it‘ll be discarded. Types of Access Lists : Standard access lists: These use only the source IP address in an IP packet to filter the network. This basically permits or denies an entire suite of protocols. IPX standards can filter on both source and destination IPX address. Extended access lists: These check for both source and destination IP address, protocol field in the Network layer header, and port number at the Transport layer header. IPX extended access lists use source and destination IPX addresses, Network layer protocol fields, and socket numbers in the Transport layer header.
- 35. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 34 Applying To Interface: Inbound access lists: Packets are processed through the access list before being routed to the outbound interface. Outbound access lists: Packets are routed to the outbound interface and then processed through the access list. Extended IP Access List Example: access-list 100-199 {permit|deny} {ip|tcp|udp|icmp} source source-mask [lt|gt|eq|neq] [source-port] destination dest-mask [lt|gt|eq|neq] [dest-port] [log] Variable Definition 100-199 Extended IP access lists are represented by a number ranging from 100-199 or text names with IOS 11.2 or greater. {permit|deny} Used to specify the nature of the access list either a permit or deny statement. {ip|tcp|udp|icmp} The IP protocol to be filtered can be IP (includes all protocols in the TCP/IP suite) TCP,UDP,ICMP,or others. source The IP address of the source source-mask A wildcard mask, or inverse mask, applied to determine which bits of source address are significant. [lt|gt|eq|neq] Can contain lt (less than), gt (greater than), eq (equal to), or neq (not equal to). It is used if an extended list filters by a specific port number or range of ports. [source-port] If necessary, the source port number of the protocol to be filtered. destination The IP address of the destination dest-mask A wildcard mask, or inverse mask, applied to determine which bits of destination address are significant. [lt|gt|eq|neq] Can contain lt (less than), gt (greater than), eq (equal to), or neq (not equal to). It is used if an extended list filters by a specific port number or range of ports. [dest-port] If necessary, the destination port number of the protocol to be filtered. [log] Turns on logging of access list activity.
- 36. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 35 Creating Access Lists: access−list 101 deny icmp host 10.10.10.21 host 10.10.10.6echo access−list 101 permit ip any 10.1.1.0 0.0.0.255 Edit ACLs: When you edit an ACL, it requires special attention. For example, if you intend to delete a specific line from a numbered ACL that exists as shown here, the entire ACL is deleted. router#configure terminal Enter configuration commands, one per line. End with CNTL/Z. router(config)#access−list 101 deny icmp any any echo router(config)#access−list 101 permit ip any any echo router(config)#^Z router#show access−list Extended IP access list 101 deny icmp any any permit ip any any router# *Mar 9 00:43:12.784: %SYS−5−CONFIG_I: Configured from console by console router#configure terminal Enter configuration commands, one per line. End with CNTL/Z. router(config)#no access−list 101 deny icmp any any echo router(config)#^Z router#show access−list router# *Mar 9 00:43:29.832: %SYS−5−CONFIG_I: Configured from console by console Applying ACL To An Interface: interface <interface> ip access−group {number|name} {in|out} interface FastEthernet 1/0 ip access−group 101 in Removing an ACL from an Interface: Go into configuration mode and enter no in front of the access−group command, as shown in this example, in order to remove an ACL from an interface. interface <interface> no ip access−group # in|out interface FastEthernet 1/0 no ip access−group 101 in
- 37. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 36 EXPERIMENT-16: About Packet Tracer Packet Tracer is a medium fidelity, network-capable, simulation-based learning environment for networking novices to design, configure, and troubleshoot computer networks at a CCNA-level of complexity. Packet Tracer is an integrated simulation, visualization, collaboration, and assessment environment. Packet Tracer supports student and instructor creation of simulations, visualizations, and animations of networking phenomena. Like any simulation, Packet Tracer relies on a simplified model of networking devices and protocols. Real computer networks, experienced both in-person/hands-on and remotely, remain the benchmark for understanding network behavior and developing networking skills. Packet Tracer was created to help address the Digital Divide in networking education, where many students and teachers lack access to equipment, bandwidth, and interactive modes of learning networking 1 Menu Bar: This bar provides the File, Edit, Options, View, Tools, Extensions, and Help menus. You will find basic commands such as Open, Save, Save as Pkz, Print, and Preferences in these menus. You will also be able to access the Activity Wizard from the Extensions menu. 2 Main Tool Bar: This bar provides shortcut icons to the File and Edit menu commands. This bar also provides buttons for Copy, Paste, Undo, Redo, Zoom, the Drawing Palette, and the Custom Devices Dialog. On the right, you will also find the Network Information button, which you can use to enter a description for the current network (or any text you wish to include). 3 Common Tools Bar: This bar provides access to these commonly used workspace tools: Select, Move Layout, Place Note, Delete, Inspect, Resize Shape, Add Simple PDU, and Add Complex PDU. See "Workspace Basics" for more information. 4 Logical/Physical Workspace and Navigation Bar: You can toggle between the Physical Workspace and the Logical Workspace with the tabs on this bar. In Logical Workspace, this bar also allows you to go back to a previous level in a cluster, create a New Cluster, Move Object, Set Tiled Background, and Viewport. In Physical Workspace, this bar allows you to navigate through physical locations, create a New City, create a New Building, create a New Closet, Move Object, apply a Grid to the background, Set Background, and go to the Working Closet. 5 Workspace: This area is where you will create your network, watch simulations, and view many kinds of information and statistics. 6 Realtime/Simulation Bar: You can toggle between Realtime Mode and Simulation Mode with the tabs on this bar. This bar also provides buttons to Power Cycle Devices and Fast Forward Time as well as the Play Control buttons and the Event List toggle button in Simulation Mode. Also, it contains a clock that displays the relative Time in Realtime Mode and Simulation Mode. 7 Network Component Box: This box is where you choose devices and connections to put into the workspace. It contains the Device-Type Selection Box and the Device-Specific Selection Box. 8 Device-Type Selection Box: This box contains the type of devices and connections available in Packet Tracer. The Device-Specific Selection Box will change depending on which type of device you choose. 9 Device-Specific Selection Box: This box is where you choose specifically which devices you want to put in your network and which connections to make.
- 38. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 37 10 User Created Packet Window: This window manages the packets you put in the network during simulation scenarios. See the "Simulation Mode" section for more details. Capturing Events and Viewing Animations in Simulation Mode: 1. Open the previously saved file. 2. Switch to Simulation Mode. 3. Click Edit Filters and click All/None to uncheck all fields. Then click ICMP to only view ICMP packets in the animation. 4. Add a simple PDU from the PC to the Server. Notice that the newly created PDU is added to the User Created PDU List. This packet has been captured as the first event in the event list and a new packet icon (envelope) appears in the workspace. The eye icon to the left of the event list indicates that this packet is currently displayed. 5. Click the Capture/Forward button once. This simulates a network sniffing program, capturing the next event that occurs on the network. Note that after clicking Capture/Forward, the packet in the workspace moves from one device to another (this is the ICMP echo request message from the PC to the Server). Another event is added in the event list – this reflects the change in the workspace. The first time through an animation, the meaning of the Capture/Forward is capture; after resetting the simulation, the meaning is forward. 6. Adjust the speed of the animation by dragging the Play Speed slider to the right making it go faster. Dragging the speed slider in the opposite direction (to the left) will slow down the animation. 7. Click the Capture/Forward button a second time. This captures the next network event (this is the echo reply from the Server to the PC, shown as successful with a green check mark on the envelope).
- 39. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 38 8. Click Capture/Forward button again. The Server has already sent an echo reply to the PC therefore, there are no more ICMP events left to capture. Looking Inside Packets in Simulation Mode: 1. Click Reset Simulation. This clears the entries in the event list except for the original packet. 2. Select the packet envelope on the workspace to show the PDU Information window like the one shown in the screenshot below. This window contains the OSI Model tab, which shows how the packet is processed at each layer of the OSI model by the current device. Close this window, noting that this packet is indicated in the event list by the eye icon. The whole row in the event list is also highlighted. Clicking on the color square in the Info column is equivalent to clicking directly on the packet envelope 3. Use the Next Layer and Previous Layer buttons to see details of the packet processing at the relevant OSI layers. Note that only the Out Layers can be viewed in the case of this original echo request message. 4. Click on the Outbound PDU Details tab. This tab shows exactly what makes up the PDU headers. It is organized into header type and the individual fields in each header. 5. Close the PDU Information window. Click on Capture/Forward button once. 6. Click on the packet in the workspace again to open the PDU Information window. Notice that this time, information regarding both the In Layers and Out Layers can be viewed. 7. Click on the Inbound PDU Details tab. This shows the details of the inbound echo request packet from the PC to the Server. The Outbound PDU Details tab, shows similar information, but for the echo reply packet from the Server to the PC.
- 40. Data Communication Lab Record 11103044 CSE 4th Sem, NIT J 39 8. Click on Reset Simulation again. Now click on Auto Capture/Play. The echo request and echo reply are automatically captured. Click on the Back Button to rewind the animation one step at a time. Now click on the Capture/Forward button to forward the packet through the animation. Note the change in the event list and the workspace. Remember that at any time, a PDU Information Window can be opened by clicking directly on the envelope on the workspace, or by clicking the Info column in the Event List. 9. Click on the Back Button twice to rewind the animation. Now click Auto Capture/Play and the packet animation will automatically occur.
