Salt Cryptography & Cracking Salted Hashes by fb1h2s
•Descargar como PPT, PDF•
3 recomendaciones•4,334 vistas
Salt Cryptography & Cracking Salted Hashes by fb1h2s @ null Pune Meet, August, 2010
Denunciar
Compartir
Denunciar
Compartir
Recomendados
Recomendados
Más contenido relacionado
Similar a Salt Cryptography & Cracking Salted Hashes by fb1h2s
Similar a Salt Cryptography & Cracking Salted Hashes by fb1h2s (20)
Hybrid Analyzer for Web Application Security (HAWAS) by Lavakumar Kuppan

Hybrid Analyzer for Web Application Security (HAWAS) by Lavakumar Kuppan
A Survey of Password Attacks and Safe Hashing Algorithms

A Survey of Password Attacks and Safe Hashing Algorithms
Password Storage And Attacking In PHP - PHP Argentina

Password Storage And Attacking In PHP - PHP Argentina
Safely Protect PostgreSQL Passwords - Tell Others to SCRAM

Safely Protect PostgreSQL Passwords - Tell Others to SCRAM
Making it Work Offline: Current & Future Offline APIs for Web Apps

Making it Work Offline: Current & Future Offline APIs for Web Apps
IRJET- Login System for Web: Session Management using BCRYPTJS

IRJET- Login System for Web: Session Management using BCRYPTJS
Más de n|u - The Open Security Community
Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_girls_chd_v1.0Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...

Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...n|u - The Open Security Community
Más de n|u - The Open Security Community (20)
Hardware security testing 101 (Null - Delhi Chapter)

Hardware security testing 101 (Null - Delhi Chapter)
Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...

Gibson 101 -quick_introduction_to_hacking_mainframes_in_2020_null_infosec_gir...
Último
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Último (20)
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Salt Cryptography & Cracking Salted Hashes by fb1h2s
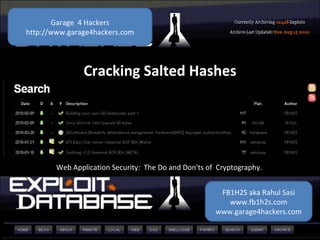
- 1. FB1H2S aka Rahul Sasi www.fb1h2s.com www.garage4hackers.com Garage 4 Hackers http://www.garage4hackers.com Cracking Salted Hashes Web Application Security: The Do and Don'ts of Cryptography.
- 5. So now what if the data are Encrypted , IS it secured ?? www.fb1h2s.com www.garage4hackkers.com
Notas del editor
- www.garage4hackers.com
