Watch Guard Firebox T10 Infographic
•
0 recomendaciones•876 vistas
WatchGuard Technologies Launches Industry’s First Enterprise-Level Unified Threat Management Security Solution Designed for Home and Small Offices
Denunciar
Compartir
Denunciar
Compartir
Recomendados
Más contenido relacionado
La actualidad más candente
La actualidad más candente (20)
Network Security Tutorial | Introduction to Network Security | Network Securi...

Network Security Tutorial | Introduction to Network Security | Network Securi...
Understanding the Risk & Challenges of Cyber Security

Understanding the Risk & Challenges of Cyber Security
Network security desighn principles and authentication

Network security desighn principles and authentication
What is CryptoLocker and How Can I Protect My Business From It?

What is CryptoLocker and How Can I Protect My Business From It?
Similar a Watch Guard Firebox T10 Infographic
Similar a Watch Guard Firebox T10 Infographic (20)
Just-How-Secure-is-your-Remote-Workforce-Infinity-Group-Ebook.pdf

Just-How-Secure-is-your-Remote-Workforce-Infinity-Group-Ebook.pdf
Securing IoT at Scale Requires a Holistic Approach

Securing IoT at Scale Requires a Holistic Approach
Bolstering the security of iiot applications – how to go about it 

Bolstering the security of iiot applications – how to go about it
Presentazione CHECKPOINT Evento CloudGarage 5-11 giugno 2013

Presentazione CHECKPOINT Evento CloudGarage 5-11 giugno 2013
Securing Your Intellectual Property: Preventing Business IP Leaks

Securing Your Intellectual Property: Preventing Business IP Leaks
Enterprise secure identity in the cloud with Single Sign On and Strong Authen...

Enterprise secure identity in the cloud with Single Sign On and Strong Authen...
Drivelock modern approach of it security & amp; encryption solution -whitep...

Drivelock modern approach of it security & amp; encryption solution -whitep...
(2019) Hack All the Way Through From Fridge to Mainframe (v0.2)

(2019) Hack All the Way Through From Fridge to Mainframe (v0.2)
What are the Various Functions of Firewall Solutions.pdf

What are the Various Functions of Firewall Solutions.pdf
Más de Randolph Novino
Más de Randolph Novino (6)
Pinoyscreencast IBLOG9 - Building your identity as a Video Blogger

Pinoyscreencast IBLOG9 - Building your identity as a Video Blogger
“How to become competitive in the job market today"

“How to become competitive in the job market today"
Último
Último (20)
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Tech Trends Report 2024 Future Today Institute.pdf

Tech Trends Report 2024 Future Today Institute.pdf
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Watch Guard Firebox T10 Infographic
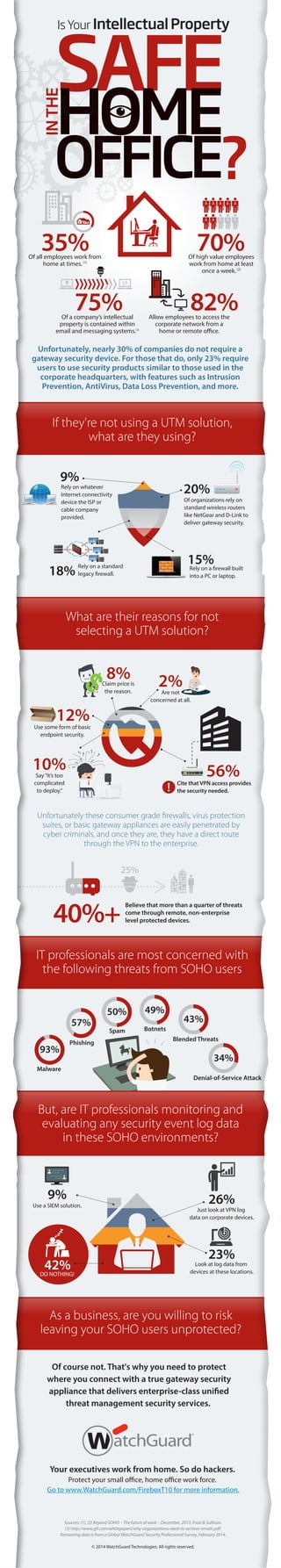
- 1. SAFE Of course not. That's why you need to protect where you connect with a true gateway security appliance that delivers enterprise-class unified threat management security services. Your executives work from home. So do hackers. Protect your small office, home office work force. Go to www.WatchGuard.com/FireboxT10 for more information. Is Your IntellectualProperty INTHE HOME OFFICE? Sources: (1), (2) Beyond SOHO – The future of work – December, 2013, Frost & Sullivan. (3) http://www.gfi.com/whitepapers/why-organizations-need-to-archive-emails.pdf. Remaining data is from a Global WatchGuard Security Professional Survey, February 2014. © 2014 WatchGuard Technologies. All rights reserved. As a business, are you willing to risk leaving your SOHO users unprotected? Of all employees work from home at times.(1) 35% Allow employees to access the corporate network from a home or remote office. 82% Of high value employees work from home at least once a week.(2) 70% 75%Of a company’s intellectual property is contained within email and messaging systems.(3) IT professionals are most concerned with the following threats from SOHO users Claim price is the reason. 8% Say“it’s too complicated to deploy.” 10% 40%+ Believe that more than a quarter of threats come through remote, non-enterprise level protected devices. 25% Unfortunately these consumer grade firewalls, virus protection suites, or basic gateway appliances are easily penetrated by cyber criminals, and once they are, they have a direct route through the VPN to the enterprise. Unfortunately, nearly 30% of companies do not require a gateway security device. For those that do, only 23% require users to use security products similar to those used in the corporate headquarters, with features such as Intrusion Prevention, AntiVirus, Data Loss Prevention, and more. But, are IT professionals monitoring and evaluating any security event log data in these SOHO environments? Spam 50% Blended Threats 43% Denial-of-Service Attack 34% Phishing 57% Botnets 49% Malware 93% If they're not using a UTM solution, what are they using? What are their reasons for not selecting a UTM solution? Of organizations rely on standard wireless routers like NetGear and D-Link to deliver gateway security. Rely on a standard legacy firewall. Rely on whatever Internet connectivity device the ISP or cable company provided. 20% 9% 18% Rely on a firewall built into a PC or laptop. 15% 42%DO NOTHING! 26% Just look at VPN log data on corporate devices. 9% Use a SIEM solution. 23% Look at log data from devices at these locations. Cite that VPN access provides the security needed. 56% Are not concerned at all. 2% Use some form of basic endpoint security. 12%
