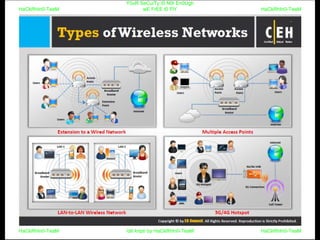
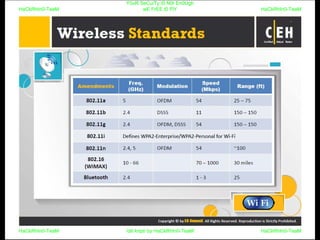
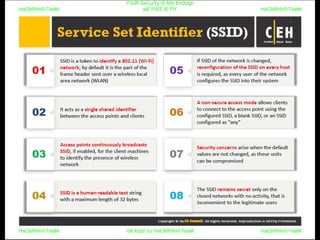
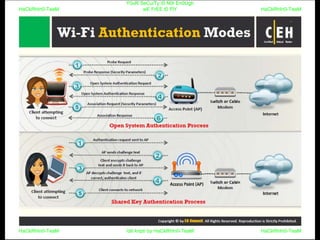
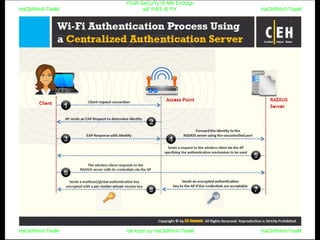
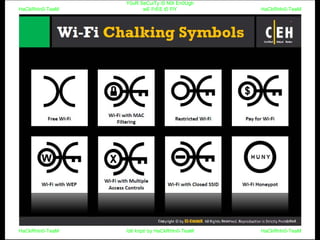
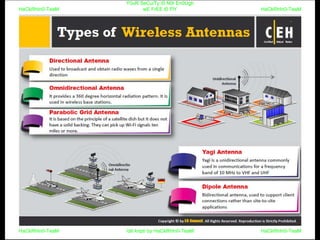
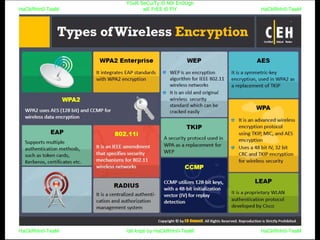
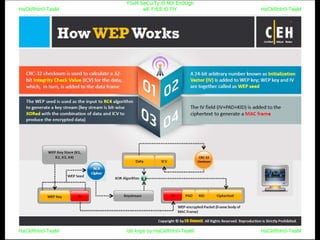
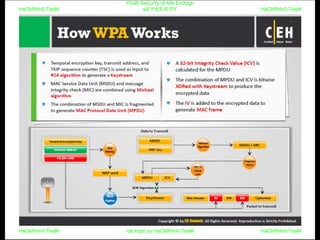
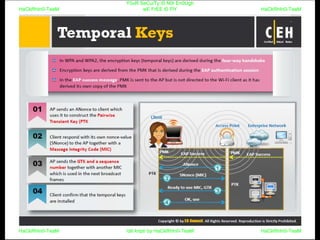
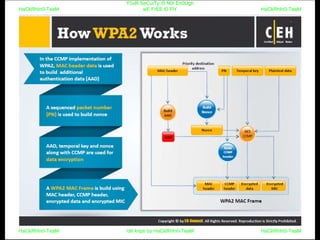
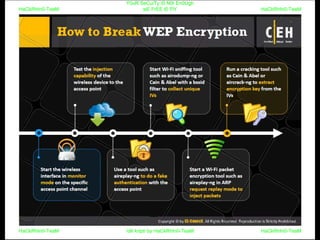
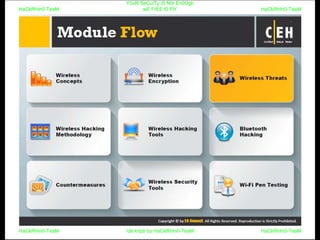
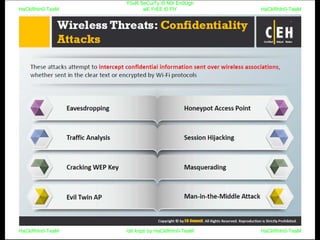
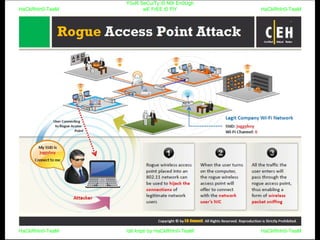
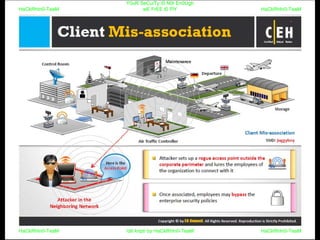
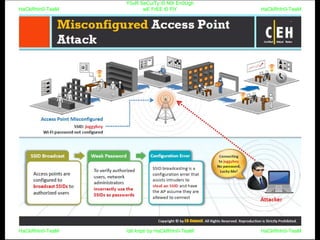
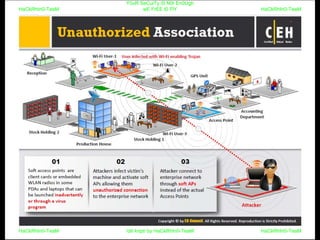
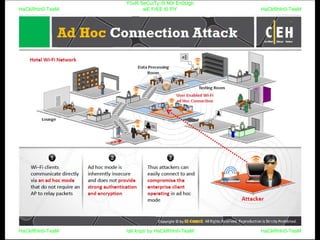
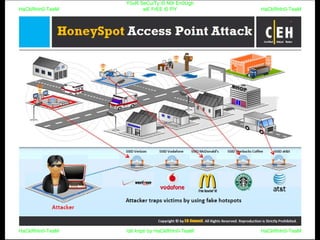
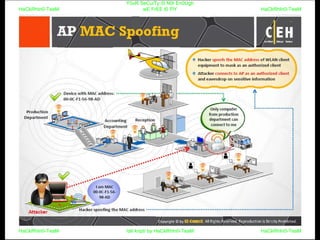
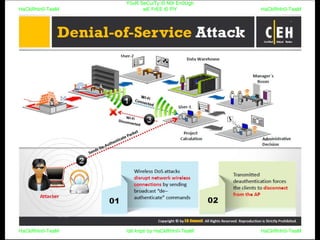
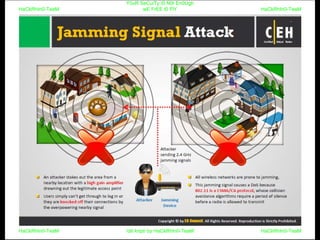
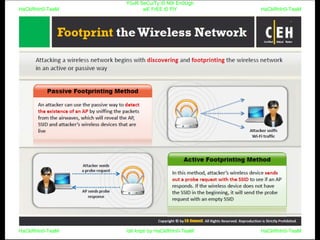
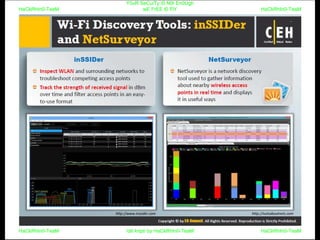
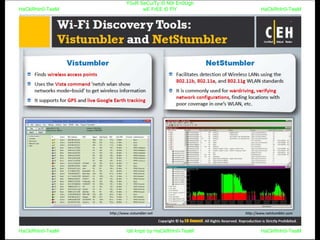
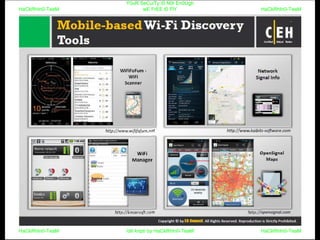
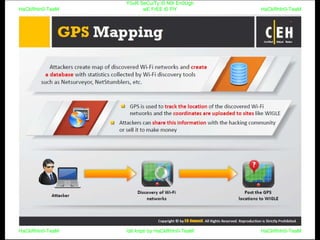
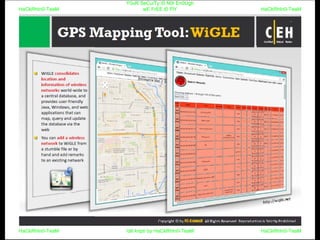
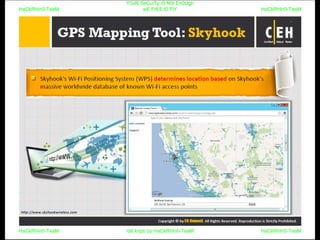
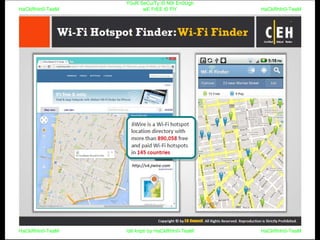
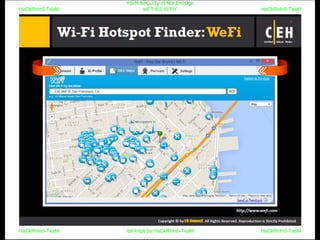
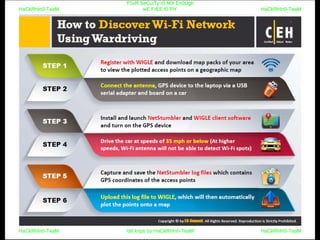
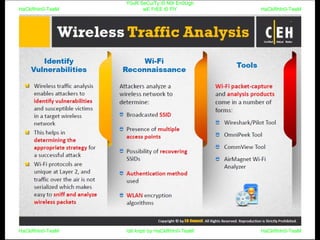
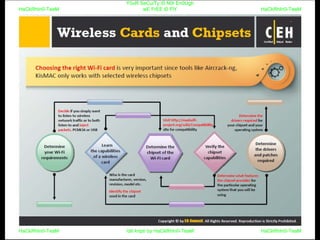
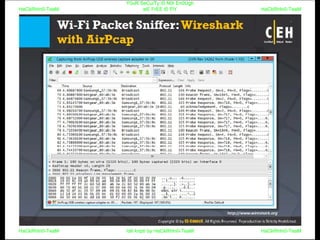
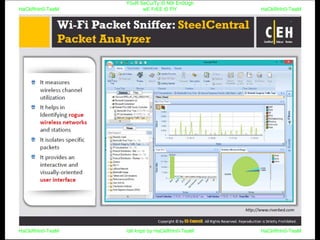
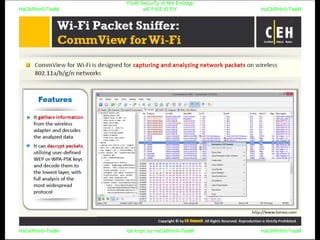
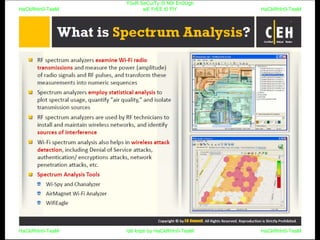
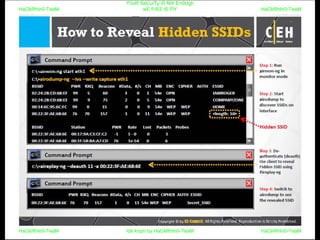
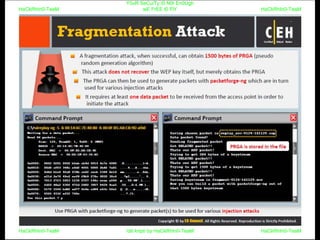
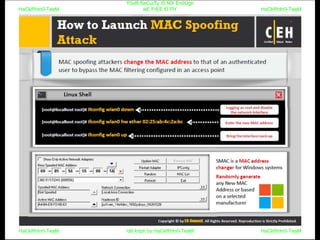
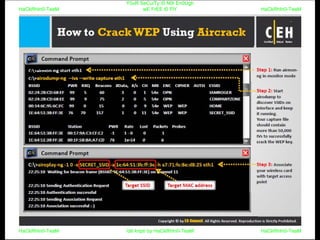
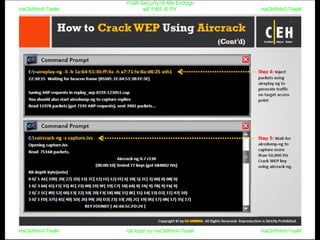
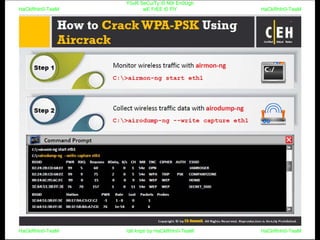
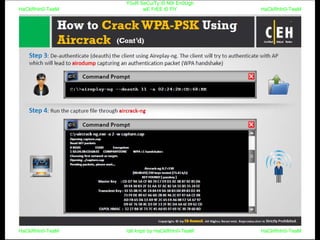
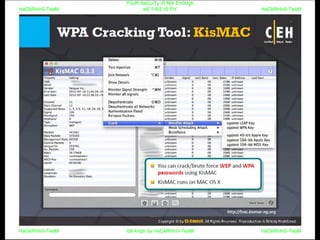
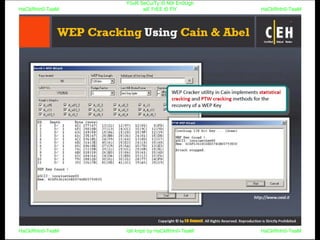
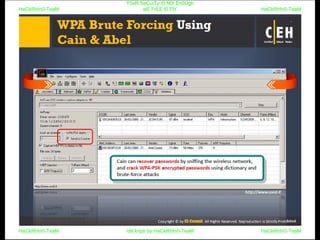
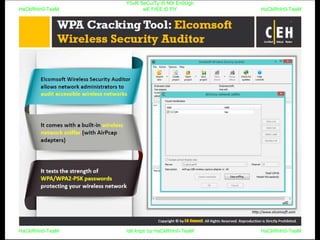
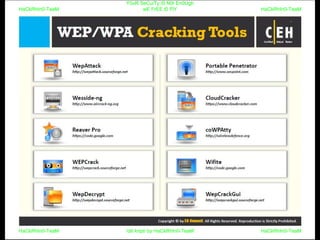
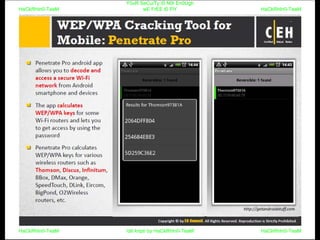
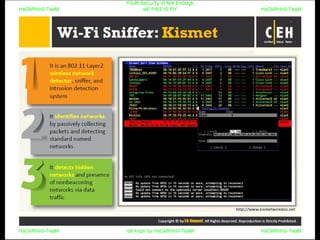
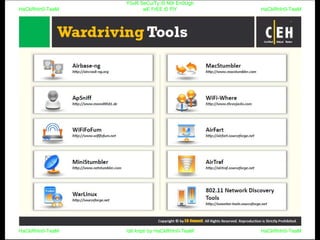
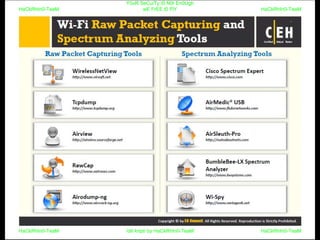
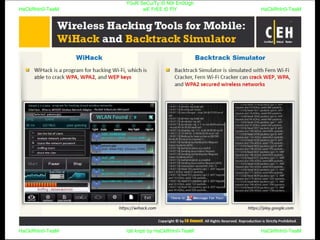
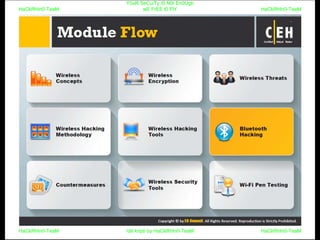
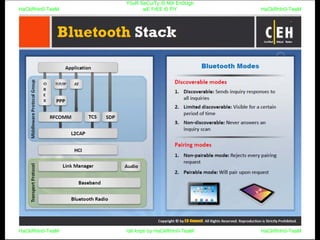
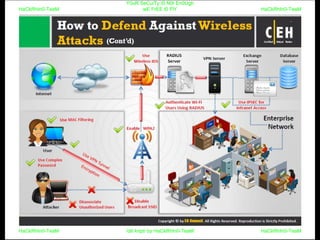
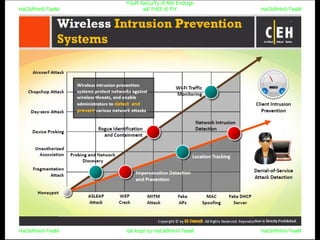
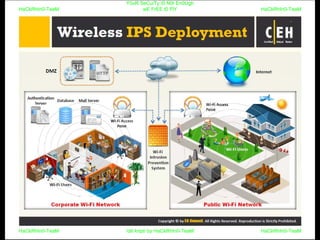
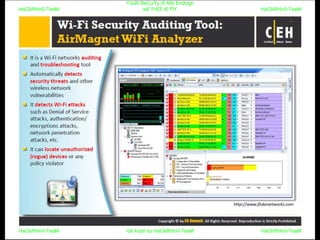
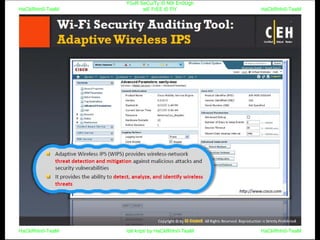
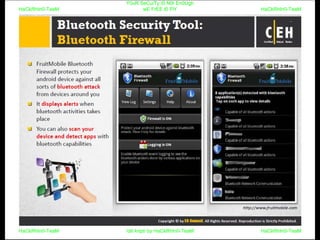
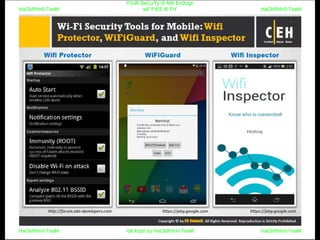
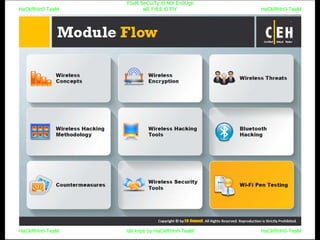
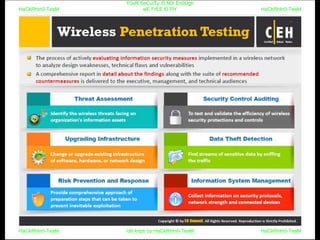
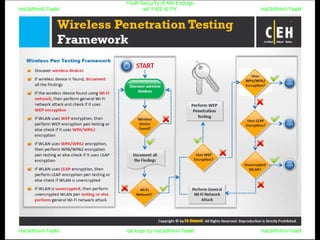
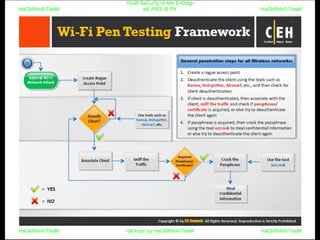
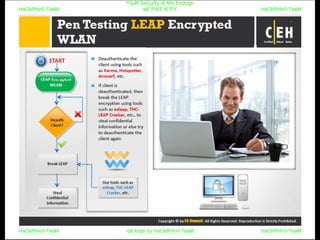
El documento repite la frase 'y0ur secuity is n0t en0ugh we free t0 fly' varias veces, indicando una preocupación sobre la seguridad. Destaca la necesidad de fortalecer la seguridad en el contexto actual. La repetición sugiere un énfasis en la urgencia de abordar la vulnerabilidad mencionada.