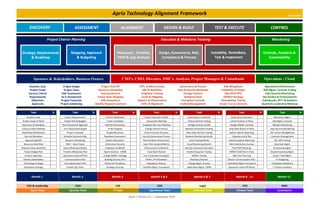
Technology Alignment Framework
•
2 recomendaciones•1,161 vistas
Let Aprio perform your next Technology Assessment There are many aspects, components and dependencies to consider when designing or improving a comprehensive technology environment for passing audits or compliance readiness. This framework was created back in 2015, revised in 2017 and improved again in January 2019 to help our clients' leadership, stakeholders and technology management teams understand the breadth of their 'current-state' environment and then help us articulate the many moving targets and critical controls requirements for 'future-state' planning, budgeting, execution, testing, operations hand-off, monitoring and achieving sustainability.
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
SOC-2 Framework - Plan, Budget, Design, Integrate & Audit Security Controls

My client Brad Schweizer, COO asked me to create a SOC Framework Diagram (36"x48" poster now hanging in the War Room) to include Terminology, Tasks, Milestones & Personnel to help monitor the implementation progress and more importantly communicate the status to the C-level stakeholders.
The Gartner IAM Program Maturity Model

The document describes the Gartner Identity and Access Management (IAM) Program Maturity Model which outlines 5 levels of maturity for an organization's IAM program:
1. Initial - Ad hoc processes with little awareness or value.
2. Defined - Certain business drivers identified and tactical priorities set with informal roles and processes.
3. Managed - IAM vision and strategy defined and aligned with business, formal processes and governance established.
4. Operational Excellence - IAM architecture refined, processes integrated and contribution to business imperatives is high.
5. Transformational - IAM vision, strategy, processes, architecture and governance optimized for maximum business value.
Cybersecurity Metrics: Reporting to BoD

The document discusses a cybersecurity metrics report for a company's board of directors. It summarizes the cyber threat landscape, digital assets at risk, the company's response to cyber risks, and a cyber risk scorecard. Key metrics include the company's BitSight security rating, number of security incidents, audit findings, and progress toward cybersecurity goals.
Cybersecurity roadmap : Global healthcare security architecture

Using NIST cybersecurity framework, one of the largest healthcare IT firms in the US developed the global security architecture and roadmap addressing security gaps by architecture domain and common security capability. This session will discuss the architecture framework, capability matrix, the architecture development methodology and key deliverables.
(Source : RSA Conference USA 2017)
NIST Cybersecurity Framework 101 

Presentation for March 2017 webcast by NIST.
www.nist.gov/cyberframework
Webcast video: https://www.nist.gov/news-events/events/2017/03/cybersecurity-framework-virtual-events
This presentation introduces the audience to the Framework for Improving Critical Infrastructure Cybersecurity (“The Framework”). It provides a brief history about why and how the Framework was developed, and an understanding of each of the three primary Framework components (the Core, Implementation Tiers, and Profiles). It covers potential benefits of Framework, and how the Framework can be used. It highlights industry resources, progress in Roadmap areas, and future direction of the Framework program.
Microsoft 365 Compliance and Security Overview

Intelligent compliance and risk management solutions.
First, we understand ‘compliance’ can have different meanings to various teams across enterprise. Compliance is an outcome of continuous risk management, involving compliance, risk, legal, privacy, security, IT and often even HR and finance teams which requires integrated approach to manage risk.
Let's start with the base pillar Compliance Management: compliance management is all about simplify risk assessment and mitigation in more automated way, providing visibility and insights to help meet compliance requirements.
Information Protection and Governance: we believe there is a huge opportunity for Microsoft to help our customers to know their data better, protect and govern data throughout its lifecycle in heterogenous environment. This is often the key starting point for many of our customers in their modern compliance journey – knowing what sensitive data they have, putting flexible, end-user friendly policies for both security and compliance outcomes, using more automation and intelligence.
Internal Risk Management: Internal risks are often what keeps business leaders up at night – regardless of negligent or malicious, identifying and being able to take action on internal risks are critical. The ability to quickly identify and manage risks from insiders (employees or contractors with corporate access) and minimize the negative impact on corporate compliance, competitive business position and brand reputation is a priority for organizations worldwide.
Last but not least, Discover and Respond: being able to discover relevant data for internal investigations, litigation, or regulatory requests and respond to them efficiently, and doing so without having to use multiple solutions and moving data in and out of systems to increase risk – is critical.
Technology Trend Roadmap.pdf

This webinar from Gartner discusses key findings from their 2021-2023 Emerging Technology Roadmap. It provides an overview of technology adoption trends seen this year, the most promising emerging technologies, and those being cautiously deployed. The webinar analyzes trends related to enabling business technologists, facilitating anywhere operations, and optimizing IT investments. It also explores how self-service delivery and data/analytics technologies are being deployed for both business and IT uses.
Cloud Adoption in the Enterprise

In this presentation from the AWS Lab at Cloud Expo Europe 2014 you will find details of the six patterns that Enterprise organisations typically to follow when adopting Amazon Web Services as well as a summary of the licensing options available for running enterprise applications on Amazon Web Services.
Recomendados
SOC-2 Framework - Plan, Budget, Design, Integrate & Audit Security Controls

My client Brad Schweizer, COO asked me to create a SOC Framework Diagram (36"x48" poster now hanging in the War Room) to include Terminology, Tasks, Milestones & Personnel to help monitor the implementation progress and more importantly communicate the status to the C-level stakeholders.
The Gartner IAM Program Maturity Model

The document describes the Gartner Identity and Access Management (IAM) Program Maturity Model which outlines 5 levels of maturity for an organization's IAM program:
1. Initial - Ad hoc processes with little awareness or value.
2. Defined - Certain business drivers identified and tactical priorities set with informal roles and processes.
3. Managed - IAM vision and strategy defined and aligned with business, formal processes and governance established.
4. Operational Excellence - IAM architecture refined, processes integrated and contribution to business imperatives is high.
5. Transformational - IAM vision, strategy, processes, architecture and governance optimized for maximum business value.
Cybersecurity Metrics: Reporting to BoD

The document discusses a cybersecurity metrics report for a company's board of directors. It summarizes the cyber threat landscape, digital assets at risk, the company's response to cyber risks, and a cyber risk scorecard. Key metrics include the company's BitSight security rating, number of security incidents, audit findings, and progress toward cybersecurity goals.
Cybersecurity roadmap : Global healthcare security architecture

Using NIST cybersecurity framework, one of the largest healthcare IT firms in the US developed the global security architecture and roadmap addressing security gaps by architecture domain and common security capability. This session will discuss the architecture framework, capability matrix, the architecture development methodology and key deliverables.
(Source : RSA Conference USA 2017)
NIST Cybersecurity Framework 101 

Presentation for March 2017 webcast by NIST.
www.nist.gov/cyberframework
Webcast video: https://www.nist.gov/news-events/events/2017/03/cybersecurity-framework-virtual-events
This presentation introduces the audience to the Framework for Improving Critical Infrastructure Cybersecurity (“The Framework”). It provides a brief history about why and how the Framework was developed, and an understanding of each of the three primary Framework components (the Core, Implementation Tiers, and Profiles). It covers potential benefits of Framework, and how the Framework can be used. It highlights industry resources, progress in Roadmap areas, and future direction of the Framework program.
Microsoft 365 Compliance and Security Overview

Intelligent compliance and risk management solutions.
First, we understand ‘compliance’ can have different meanings to various teams across enterprise. Compliance is an outcome of continuous risk management, involving compliance, risk, legal, privacy, security, IT and often even HR and finance teams which requires integrated approach to manage risk.
Let's start with the base pillar Compliance Management: compliance management is all about simplify risk assessment and mitigation in more automated way, providing visibility and insights to help meet compliance requirements.
Information Protection and Governance: we believe there is a huge opportunity for Microsoft to help our customers to know their data better, protect and govern data throughout its lifecycle in heterogenous environment. This is often the key starting point for many of our customers in their modern compliance journey – knowing what sensitive data they have, putting flexible, end-user friendly policies for both security and compliance outcomes, using more automation and intelligence.
Internal Risk Management: Internal risks are often what keeps business leaders up at night – regardless of negligent or malicious, identifying and being able to take action on internal risks are critical. The ability to quickly identify and manage risks from insiders (employees or contractors with corporate access) and minimize the negative impact on corporate compliance, competitive business position and brand reputation is a priority for organizations worldwide.
Last but not least, Discover and Respond: being able to discover relevant data for internal investigations, litigation, or regulatory requests and respond to them efficiently, and doing so without having to use multiple solutions and moving data in and out of systems to increase risk – is critical.
Technology Trend Roadmap.pdf

This webinar from Gartner discusses key findings from their 2021-2023 Emerging Technology Roadmap. It provides an overview of technology adoption trends seen this year, the most promising emerging technologies, and those being cautiously deployed. The webinar analyzes trends related to enabling business technologists, facilitating anywhere operations, and optimizing IT investments. It also explores how self-service delivery and data/analytics technologies are being deployed for both business and IT uses.
Cloud Adoption in the Enterprise

In this presentation from the AWS Lab at Cloud Expo Europe 2014 you will find details of the six patterns that Enterprise organisations typically to follow when adopting Amazon Web Services as well as a summary of the licensing options available for running enterprise applications on Amazon Web Services.
Identity and Access Management Introduction

The Identity management solutions required specific skill to successfully deploy it. This presentation will help you to star build some of them.
Making a cloud first strategy a practical reality

1) The document discusses strategies for adopting a cloud-first approach, including establishing executive sponsorship, experimenting with cloud technologies, educating staff, creating a cloud center of excellence, adopting hybrid cloud models, establishing a cloud-first standard, engaging partners, and making cloud adoption a reality.
2) It presents traditional IT organization structures and how these can be adapted by adopting AWS services for different functions like infrastructure, applications, security, and end user computing.
3) The key steps outlined are gaining executive support, starting with small experiments, educating staff on cloud benefits and technologies, and establishing centers of excellence and processes to guide ongoing cloud adoption.
Building A Cloud Strategy PowerPoint Presentation Slides

It covers all the important concepts and has relevant templates which cater to your business needs. This complete deck has PPT slides on Building A Cloud Strategy PowerPoint Presentation Slides with well suited graphics and subject driven content. This deck consists of total of twenty five slides. All templates are completely editable for your convenience. You can change the colour, text and font size of these slides. You can add or delete the content as per your requirement. Get access to this professionally designed complete deck presentation by clicking the download button below. https://bit.ly/2LuZsQP
IT Governance Presentation

IT Governance Presentation
Field Project II
Team 2
Juan Manuel Cardenas
Maria Lucia Peraza
Amilcar Alfredo Umaña
Gabriel Gomez Silva
Victor Gutiérrez
Cybersecurity Frameworks | NIST Cybersecurity Framework | Cybersecurity Certi...

** CyberSecurity Certification Training: https://www.edureka.co/cybersecurity-certification-training **
This Edureka tutorial on "Cybersecurity Frameworks" will help you understand why and how the organizations are using the cybersecurity framework to Identify, Protect and Recover from cyber attacks.
Cybersecurity Training Playlist: https://bit.ly/2NqcTQV
Integrating It Frameworks, Methodologies And Best Practices Into It Delivery ...

The document proposes an integrated IT solution and operations management approach consisting of two pillars: 1) Architecture and Realisation, which is concerned with enterprise vision, strategy, architecture, implementation and operation. 2) Management and Processes, which addresses management of initiatives, programmes, projects and associated processes. It suggests grouping relevant frameworks under these pillars to provide guidance on core functions. Frameworks can help organizations quickly develop core competencies across functions like quality management, resource management, and financial management.
Security architecture frameworks

This document discusses security architecture frameworks and concepts. It outlines different frameworks for security architecture like TOGAF, SABSA, and FAIR. It then discusses key concepts in security architecture like assets, threats, domains, risks, and security measures. Risks can come from assets, threats, or domains and security architecture aims to reduce business risks from IT through frameworks, standards, and applying the right security measures.
Microsoft-CISO-Workshop-Security-Strategy-and-Program (1).pdf

The document discusses a CISO workshop agenda to modernize a security strategy and program. It includes:
- An overview of who should attend, such as the CISO, CIO, security directors, and business leaders.
- The agenda covers key context and fundamentals, business alignment, and security disciplines.
- Exercises are included to assess maturity, discuss recommendations, and assign next steps.
- Modules will provide guidance on initiatives like secure identities and access, security operations, and data security.
NIST cybersecurity framework

The NIST Cybersecurity Framework acts as a bridge between the management and Cybersecurity ecosystem.
Cybersecurity Roadmap Development for Executives

Secrets to managing your Duty of Care in an ever- changing world.
How well do you know your risks?
Are you keeping up with your responsibilities to provide Duty of Care?
How well are you prioritising Cybersecurity initiatives?
Liability for Cybersecurity attacks sits with Executives and Board members who may not have the right level of technical security knowledge. This session will outline what practical steps executives can take to implement a Cybersecurity Roadmap that is aligned with its strategic objectives.
Led by Krist Davood, who has spent over 28 years implementing secure mission critical systems for executives. Krist is an expert in protecting the interconnectedness of technology, intellectual property and information systems, as evidenced through his roles at The Good Guys, Court Services Victoria and Schiavello.
The seminar will cover:
• Fiduciary responsibility
• How to efficiently deal with personal liability and the threat of court action
• The role of a Cybersecurity Executive Dashboard and its ability to simplify risk and amplify informed decision making
• How to identify and bridge the gap between your Cybersecurity Compliance Rating and the threat of court action
Enterprise Security Architecture

Enterprise Architecture
Enterprise Architectural Methodologies
A Brief History of Enterprise Architecture
Zachman Framework
Business Attributes
Features & Advantages
SABSA Lifecycle
SABSA Development Process
SMP Maturity Levels
Steps to iso 27001 implementation

Here are some small steps to achieve ISO 27001 implementation.
I believe ISO 27001/2 is a key to establish security in the organizations and help the companies to keep the whole ISMS program running aligned with continues improvement.
As ISO 27001 has been identified by ICO and recognized by GCHQ/NCSC in the past as the key standard to support GDPR.
Security operations center-SOC Presentation-مرکز عملیات امنیت

Cyber Security Trends
Business Concerns
Cyber Threats
The Solutions
Security Operation Center
requirement
SOC Architecture model
SOC Implementation
SOC & NOC
SOC & CSIRT
SIEM & Correlation
-----------------------------------------------------------
Definition
Gartner defines a SOC as both a team, often operating in shifts around the clock, and a facility dedicated to and organized to prevent, detect, assess and respond to cybersecurity threats and incidents, and to fulfill and assess regulatory compliance. The term "cybersecurity operation center "is often used synonymously for SOC.
A network operations center (NOC) is not a SOC, which focuses on network device management rather than detecting and responding to cybersecurity incidents. Coordination between the two is common, however.
A managed security service is not the same as having a SOC — although a service provider may offer services from a SOC. A managed service is a shared resource and not solely dedicated to a single organization or entity. Similarly, there is no such thing as a managed SOC.
Most of the technologies, processes and best practices that are used in a SOC are not specific to a SOC. Incident response or vulnerability management remain the same, whether delivered from a SOC or not. It is a meta-topic, involving many security domains and disciplines, and depending on the services and functions that are delivered by the SOC.
Services that often reside in a SOC are:
• Cyber security incident response
• Malware analysis
• Forensic analysis
• Threat intelligence analysis
• Risk analytics and attack path modeling
• Countermeasure implementation
• Vulnerability assessment
• Vulnerability analysis
• Penetration testing
• Remediation prioritization and coordination
• Security intelligence collection and fusion
• Security architecture design
• Security consulting
• Security awareness training
• Security audit data collection and distribution
Alternative names for SOC :
Security defense center (SDC)
Security intelligence center
Cyber security center
Threat defense center
security intelligence and operations center (SIOC)
Infrastructure Protection Centre (IPC)
مرکز عملیات امنیت
Top management role to implement ISO 27001

The webinar covers:
1- Build a business case to implement ISO27001
- Who are stakeholders?
- Who is project executive sponsor?
- Incentives to implement? Is BOD in support? Industry /market pressures?
- History (previous attempts/audits/issues/implications if failed)
- Consultant selection
- Cost and budgetary constraints.
- Resources constraints
2- Costs of not implementing ISO 27001
3- Wrap-up
Presenter:
The webinar was presented from PECB Partner and Trainer Mr. Mohamad Khachab who has 30 years of professional experience in management consultancy, project management, teaching/training, IT Procurement, preparing proposals, information risk management, research, developing bidding documents, and business development activities.
Link of the recorded session published on YouTube: https://youtu.be/6kBp3SxKDP8
Cybersecurity Frameworks for DMZCON23 230905.pdf

This document discusses cybersecurity frameworks and provides an overview of the most popular frameworks. It begins by defining frameworks, regulations, standards and guidelines. Some of the main benefits of frameworks mentioned are providing a comprehensive security baseline, enabling measurement and benchmarking, and demonstrating maturity. Twelve of the most popular frameworks are then listed and described briefly. The document outlines different types of frameworks and provides tips for choosing an appropriate framework based on mandatory requirements, country practices, industry usage, certification needs, organization size and maturity. It also discusses mappings between frameworks and attributes of information security controls.
Roadmap to IT Security Best Practices

The document discusses the importance of IT security best practices for healthcare organizations. It outlines why IT security is important, how to get started with a security program, and provides information on specific best practices. These include recommendations for securing remote users' access to protected health information, implementing system log management, and meeting meaningful use security criteria. The document aims to help healthcare organizations develop an IT security roadmap.
Data Governance Workshop

The document outlines several upcoming workshops hosted by CCG, an analytics consulting firm, including:
- An Analytics in a Day workshop focusing on Synapse on March 16th and April 20th.
- An Introduction to Machine Learning workshop on March 23rd.
- A Data Modernization workshop on March 30th.
- A Data Governance workshop with CCG and Profisee on May 4th focusing on leveraging MDM within data governance.
More details and registration information can be found on ccganalytics.com/events. The document encourages following CCG on LinkedIn for event updates.
MITRE ATT&CKcon 2.0: Prioritizing ATT&CK Informed Defenses the CIS Way; Phili...

MITRE ATT&CKcon 2.0: Prioritizing ATT&CK Informed Defenses the CIS Way; Philippe Langlois, Verizon and Joshua Franklin, CIS
IT Governance – The missing compass in a technology changing world

Oladapo Ogundeji, CTO of Digital Jewels Ltd, gave a presentation on IT governance and its importance in today's technology changing world. He discussed that IT governance provides a formal process to define IT strategy and oversee its execution to achieve business goals. It also helps balance priorities like maximizing returns, increasing agility, and mitigating risks. Ogundeji covered frameworks like COBIT 5 and ISO 38500 that provide guidance on implementing IT governance and highlighted critical success factors like executive commitment, focus on execution, and competence in resources.
Information Security Governance and Strategy 

The document discusses information security governance and strategy based on ISO 38500:2008. It covers key aspects of IT governance including evaluating who makes IT decisions, directing the implementation of decisions, and monitoring conformance. The six principles of IT governance outlined are responsibility, strategy, acquisition, performance, conformance, and human behavior. An IT governance model is illustrated showing how the principles relate to evaluating, directing, and monitoring IT processes.
PRP - 21st Century Program/Project Management

Simple scheduling no longer makes the grade. 21st Century Progra/Project Managers Need Cutting Edge Tools. Project Resource Planning platforms are the first fully integrated automated tool set for managing projects in the 21st Century.
Experience and Qualifications

April B. White has over 10 years of experience in marketing and proposals. She has submitted over 100 proposals and marketing pieces in 2010. She also has experience in data collection, contact management, surveys, and strategic networking projects.
Más contenido relacionado
La actualidad más candente
Identity and Access Management Introduction

The Identity management solutions required specific skill to successfully deploy it. This presentation will help you to star build some of them.
Making a cloud first strategy a practical reality

1) The document discusses strategies for adopting a cloud-first approach, including establishing executive sponsorship, experimenting with cloud technologies, educating staff, creating a cloud center of excellence, adopting hybrid cloud models, establishing a cloud-first standard, engaging partners, and making cloud adoption a reality.
2) It presents traditional IT organization structures and how these can be adapted by adopting AWS services for different functions like infrastructure, applications, security, and end user computing.
3) The key steps outlined are gaining executive support, starting with small experiments, educating staff on cloud benefits and technologies, and establishing centers of excellence and processes to guide ongoing cloud adoption.
Building A Cloud Strategy PowerPoint Presentation Slides

It covers all the important concepts and has relevant templates which cater to your business needs. This complete deck has PPT slides on Building A Cloud Strategy PowerPoint Presentation Slides with well suited graphics and subject driven content. This deck consists of total of twenty five slides. All templates are completely editable for your convenience. You can change the colour, text and font size of these slides. You can add or delete the content as per your requirement. Get access to this professionally designed complete deck presentation by clicking the download button below. https://bit.ly/2LuZsQP
IT Governance Presentation

IT Governance Presentation
Field Project II
Team 2
Juan Manuel Cardenas
Maria Lucia Peraza
Amilcar Alfredo Umaña
Gabriel Gomez Silva
Victor Gutiérrez
Cybersecurity Frameworks | NIST Cybersecurity Framework | Cybersecurity Certi...

** CyberSecurity Certification Training: https://www.edureka.co/cybersecurity-certification-training **
This Edureka tutorial on "Cybersecurity Frameworks" will help you understand why and how the organizations are using the cybersecurity framework to Identify, Protect and Recover from cyber attacks.
Cybersecurity Training Playlist: https://bit.ly/2NqcTQV
Integrating It Frameworks, Methodologies And Best Practices Into It Delivery ...

The document proposes an integrated IT solution and operations management approach consisting of two pillars: 1) Architecture and Realisation, which is concerned with enterprise vision, strategy, architecture, implementation and operation. 2) Management and Processes, which addresses management of initiatives, programmes, projects and associated processes. It suggests grouping relevant frameworks under these pillars to provide guidance on core functions. Frameworks can help organizations quickly develop core competencies across functions like quality management, resource management, and financial management.
Security architecture frameworks

This document discusses security architecture frameworks and concepts. It outlines different frameworks for security architecture like TOGAF, SABSA, and FAIR. It then discusses key concepts in security architecture like assets, threats, domains, risks, and security measures. Risks can come from assets, threats, or domains and security architecture aims to reduce business risks from IT through frameworks, standards, and applying the right security measures.
Microsoft-CISO-Workshop-Security-Strategy-and-Program (1).pdf

The document discusses a CISO workshop agenda to modernize a security strategy and program. It includes:
- An overview of who should attend, such as the CISO, CIO, security directors, and business leaders.
- The agenda covers key context and fundamentals, business alignment, and security disciplines.
- Exercises are included to assess maturity, discuss recommendations, and assign next steps.
- Modules will provide guidance on initiatives like secure identities and access, security operations, and data security.
NIST cybersecurity framework

The NIST Cybersecurity Framework acts as a bridge between the management and Cybersecurity ecosystem.
Cybersecurity Roadmap Development for Executives

Secrets to managing your Duty of Care in an ever- changing world.
How well do you know your risks?
Are you keeping up with your responsibilities to provide Duty of Care?
How well are you prioritising Cybersecurity initiatives?
Liability for Cybersecurity attacks sits with Executives and Board members who may not have the right level of technical security knowledge. This session will outline what practical steps executives can take to implement a Cybersecurity Roadmap that is aligned with its strategic objectives.
Led by Krist Davood, who has spent over 28 years implementing secure mission critical systems for executives. Krist is an expert in protecting the interconnectedness of technology, intellectual property and information systems, as evidenced through his roles at The Good Guys, Court Services Victoria and Schiavello.
The seminar will cover:
• Fiduciary responsibility
• How to efficiently deal with personal liability and the threat of court action
• The role of a Cybersecurity Executive Dashboard and its ability to simplify risk and amplify informed decision making
• How to identify and bridge the gap between your Cybersecurity Compliance Rating and the threat of court action
Enterprise Security Architecture

Enterprise Architecture
Enterprise Architectural Methodologies
A Brief History of Enterprise Architecture
Zachman Framework
Business Attributes
Features & Advantages
SABSA Lifecycle
SABSA Development Process
SMP Maturity Levels
Steps to iso 27001 implementation

Here are some small steps to achieve ISO 27001 implementation.
I believe ISO 27001/2 is a key to establish security in the organizations and help the companies to keep the whole ISMS program running aligned with continues improvement.
As ISO 27001 has been identified by ICO and recognized by GCHQ/NCSC in the past as the key standard to support GDPR.
Security operations center-SOC Presentation-مرکز عملیات امنیت

Cyber Security Trends
Business Concerns
Cyber Threats
The Solutions
Security Operation Center
requirement
SOC Architecture model
SOC Implementation
SOC & NOC
SOC & CSIRT
SIEM & Correlation
-----------------------------------------------------------
Definition
Gartner defines a SOC as both a team, often operating in shifts around the clock, and a facility dedicated to and organized to prevent, detect, assess and respond to cybersecurity threats and incidents, and to fulfill and assess regulatory compliance. The term "cybersecurity operation center "is often used synonymously for SOC.
A network operations center (NOC) is not a SOC, which focuses on network device management rather than detecting and responding to cybersecurity incidents. Coordination between the two is common, however.
A managed security service is not the same as having a SOC — although a service provider may offer services from a SOC. A managed service is a shared resource and not solely dedicated to a single organization or entity. Similarly, there is no such thing as a managed SOC.
Most of the technologies, processes and best practices that are used in a SOC are not specific to a SOC. Incident response or vulnerability management remain the same, whether delivered from a SOC or not. It is a meta-topic, involving many security domains and disciplines, and depending on the services and functions that are delivered by the SOC.
Services that often reside in a SOC are:
• Cyber security incident response
• Malware analysis
• Forensic analysis
• Threat intelligence analysis
• Risk analytics and attack path modeling
• Countermeasure implementation
• Vulnerability assessment
• Vulnerability analysis
• Penetration testing
• Remediation prioritization and coordination
• Security intelligence collection and fusion
• Security architecture design
• Security consulting
• Security awareness training
• Security audit data collection and distribution
Alternative names for SOC :
Security defense center (SDC)
Security intelligence center
Cyber security center
Threat defense center
security intelligence and operations center (SIOC)
Infrastructure Protection Centre (IPC)
مرکز عملیات امنیت
Top management role to implement ISO 27001

The webinar covers:
1- Build a business case to implement ISO27001
- Who are stakeholders?
- Who is project executive sponsor?
- Incentives to implement? Is BOD in support? Industry /market pressures?
- History (previous attempts/audits/issues/implications if failed)
- Consultant selection
- Cost and budgetary constraints.
- Resources constraints
2- Costs of not implementing ISO 27001
3- Wrap-up
Presenter:
The webinar was presented from PECB Partner and Trainer Mr. Mohamad Khachab who has 30 years of professional experience in management consultancy, project management, teaching/training, IT Procurement, preparing proposals, information risk management, research, developing bidding documents, and business development activities.
Link of the recorded session published on YouTube: https://youtu.be/6kBp3SxKDP8
Cybersecurity Frameworks for DMZCON23 230905.pdf

This document discusses cybersecurity frameworks and provides an overview of the most popular frameworks. It begins by defining frameworks, regulations, standards and guidelines. Some of the main benefits of frameworks mentioned are providing a comprehensive security baseline, enabling measurement and benchmarking, and demonstrating maturity. Twelve of the most popular frameworks are then listed and described briefly. The document outlines different types of frameworks and provides tips for choosing an appropriate framework based on mandatory requirements, country practices, industry usage, certification needs, organization size and maturity. It also discusses mappings between frameworks and attributes of information security controls.
Roadmap to IT Security Best Practices

The document discusses the importance of IT security best practices for healthcare organizations. It outlines why IT security is important, how to get started with a security program, and provides information on specific best practices. These include recommendations for securing remote users' access to protected health information, implementing system log management, and meeting meaningful use security criteria. The document aims to help healthcare organizations develop an IT security roadmap.
Data Governance Workshop

The document outlines several upcoming workshops hosted by CCG, an analytics consulting firm, including:
- An Analytics in a Day workshop focusing on Synapse on March 16th and April 20th.
- An Introduction to Machine Learning workshop on March 23rd.
- A Data Modernization workshop on March 30th.
- A Data Governance workshop with CCG and Profisee on May 4th focusing on leveraging MDM within data governance.
More details and registration information can be found on ccganalytics.com/events. The document encourages following CCG on LinkedIn for event updates.
MITRE ATT&CKcon 2.0: Prioritizing ATT&CK Informed Defenses the CIS Way; Phili...

MITRE ATT&CKcon 2.0: Prioritizing ATT&CK Informed Defenses the CIS Way; Philippe Langlois, Verizon and Joshua Franklin, CIS
IT Governance – The missing compass in a technology changing world

Oladapo Ogundeji, CTO of Digital Jewels Ltd, gave a presentation on IT governance and its importance in today's technology changing world. He discussed that IT governance provides a formal process to define IT strategy and oversee its execution to achieve business goals. It also helps balance priorities like maximizing returns, increasing agility, and mitigating risks. Ogundeji covered frameworks like COBIT 5 and ISO 38500 that provide guidance on implementing IT governance and highlighted critical success factors like executive commitment, focus on execution, and competence in resources.
Information Security Governance and Strategy 

The document discusses information security governance and strategy based on ISO 38500:2008. It covers key aspects of IT governance including evaluating who makes IT decisions, directing the implementation of decisions, and monitoring conformance. The six principles of IT governance outlined are responsibility, strategy, acquisition, performance, conformance, and human behavior. An IT governance model is illustrated showing how the principles relate to evaluating, directing, and monitoring IT processes.
La actualidad más candente (20)
Building A Cloud Strategy PowerPoint Presentation Slides

Building A Cloud Strategy PowerPoint Presentation Slides
Cybersecurity Frameworks | NIST Cybersecurity Framework | Cybersecurity Certi...

Cybersecurity Frameworks | NIST Cybersecurity Framework | Cybersecurity Certi...
Integrating It Frameworks, Methodologies And Best Practices Into It Delivery ...

Integrating It Frameworks, Methodologies And Best Practices Into It Delivery ...
Microsoft-CISO-Workshop-Security-Strategy-and-Program (1).pdf

Microsoft-CISO-Workshop-Security-Strategy-and-Program (1).pdf
Security operations center-SOC Presentation-مرکز عملیات امنیت

Security operations center-SOC Presentation-مرکز عملیات امنیت
MITRE ATT&CKcon 2.0: Prioritizing ATT&CK Informed Defenses the CIS Way; Phili...

MITRE ATT&CKcon 2.0: Prioritizing ATT&CK Informed Defenses the CIS Way; Phili...
IT Governance – The missing compass in a technology changing world

IT Governance – The missing compass in a technology changing world
Similar a Technology Alignment Framework
PRP - 21st Century Program/Project Management

Simple scheduling no longer makes the grade. 21st Century Progra/Project Managers Need Cutting Edge Tools. Project Resource Planning platforms are the first fully integrated automated tool set for managing projects in the 21st Century.
Experience and Qualifications

April B. White has over 10 years of experience in marketing and proposals. She has submitted over 100 proposals and marketing pieces in 2010. She also has experience in data collection, contact management, surveys, and strategic networking projects.
PMP CAPM Study Guide Risk Management

CAPM Study Guide Risk Management,
PMP Study Guide Risk Management,
PMI PMBK Study Guide Risk Management,Higazi PMP CSM,Ahmed Higazi,PMBK4th,
Risk Management ITTO
Project Management

This document provides an overview of project management concepts including definitions of key terms, the project life cycle, tools and techniques used in project management, and components involved in planning, executing, monitoring, and closing projects. It discusses aspects of project management such as time, cost, quality management, risk management, and stakeholder management. The document also covers topics like project feasibility, scheduling, estimation, and control.
PMO & CMMI

The document discusses the purpose and setup of a Project Management Office (PMO). It states that a PMO aims to standardize processes, provide governance and oversight of projects, and help align projects with business strategy. The document outlines the typical services a PMO provides, such as resource management, portfolio management, and reporting. It also discusses how a PMO's processes and goals evolve over the near, medium and long term to eventually establish common development practices, centralized project planning, and continuous process improvements.
Mastering T&T analysis in PMP - PMBOK Ver5

It can't be better than this. Perfect slides to make a head start to PMP. Sure short score and understanding increasr... Its Sanjeenvani ..
This gives you insights about how the data flows from
proces to another
pmos.pptx

The document outlines key components for establishing a project management office (PMO), including the PMO mandate, goals and benefits, stakeholders, timeline, roles and responsibilities, and risk assessment. It also discusses how most PMOs initially focus on improving project delivery but later take on broader responsibilities like program and portfolio management as they earn credibility. Finally, it provides a sample PMO responsibilities matrix detailing common PMO functions.
Usability And Project Management

The document discusses project management and usability. It provides an overview of project management, including the key aspects of integration management, scope management, time management, cost management, quality management, human resources management, communications management, risk management, and procurement management. It also discusses the history of project management and some common project management frameworks and standards.
PMO Framework Corus360 V2B

This document outlines the processes and procedures for managing discovery projects at Corus360, including governance groups, documentation requirements, and project lifecycle stages from initiation to close. It details the roles and responsibilities of various teams in sales, engineering, project management, and operations. Key aspects of the framework include governance approvals at three gates, status reporting, and financial analysis to track project profitability.
Pm training (planning and tracking) - Project Leader Ramp-Up 

Course Objective
The purpose of this course is to make a short summary about the Fsoft processes & practices to be used in the project context.
This course is not aimed to replace the normal training courses.
Governance, Risk & Compliance Management Solution

This document discusses governance, risk, and compliance (GRC) management solutions. It outlines challenges organizations face with GRC such as siloed management, a reactive approach, and lack of integration with core processes. The document proposes moving from basic compliance programs to an optimized, holistic GRC approach supported by IT and business alignment. It presents Rishabh's GRC capabilities and services to help clients implement integrated GRC management.
Managed it services

This document discusses managed IT services provided by GSS America. It outlines various challenges faced by organizations including budget constraints, lack of skills, and regulatory compliance issues. GSS provides a range of managed services including infrastructure management, application management, and service delivery frameworks. Case studies demonstrate how GSS has helped clients through dedicated support teams, standard operating procedures, and optimized costs while ensuring quality of service and end user satisfaction.
Managed It Services

GSS America\'s Workplace Services aim at equipping customer’s business with round-the-clock support, through its Global Operations Command Center (GOCC). Its comprehensive range of workplace services gives customers the ability to reduce their costs and improve their service levels. GSS intends to help global enterprises cut down on their infrastructure maintenance costs and provide access to expert skills.
David Schroeder Summary

David Schroeder has extensive experience in project management, business analysis, and solution development across multiple industries. He has led teams to deliver solutions such as enhancements to medical systems, financial system integrations, procurement systems, and CRM implementations. Schroeder has strengths in defining requirements, estimating projects, managing budgets and schedules, and ensuring successful delivery of products.
Actualize Practice Groups 1

The document discusses the expertise of a firm in capital markets, mortgage and fixed income operations, accounting and financial analysis, and risk management. It provides details on the various areas of industry and business process expertise, asset classes, accounting and financial analysis services, and project experience of teams in capital markets, mortgage and fixed income operations, and accounting and financial analysis.
Actualize Practice Groups 1

The document discusses the expertise of a firm in capital markets, mortgage and fixed income operations, accounting and financial analysis, and risk management. It provides details on the various areas of industry and business process expertise, asset classes, accounting and financial analysis services, and project experience of teams in capital markets, mortgage and fixed income operations, and accounting and financial analysis.
PMP ITTOs Quick Review 

This document contains a quick review of all the PMP processes Inputs, output and Tools& Techniques ITTOs
01 Corporate Profile Green Intl_PM Services,Training and Oil & Gas

Green International provides project management and consulting services globally. It offers a range of services including project management, construction management, LEED consulting, training programs, and safety consulting. The document provides details on each service line and lists the company's locations and certifications. It aims to help clients deliver projects on time, within budget and to a high quality.
Project management methodology pmo example (short sanitised)

The document outlines the stages of an operational excellence framework including appraise, select, define, execute, and operate gates. At each gate, core items are reviewed such as the project charter, scope, financials, risks, and stakeholders. The goal is to choose the right projects, deliver them successfully, and hand them over to the operating unit once complete through effective project portfolio management and governance.
Paul charife-allen resume-it security

Over the past 17 years, he has worked with numerous companies in Atlantic Canada, assisting with system development, operations planning and marketing initiatives; ensuring suitable alignment of technology with your long-term business goals. His consulting experience, project management, and business analyst background constitute the perfect fusion of skills to ensure requirements are identified; resolving projects on time and budget. Unlike others with similar skills, his commitment to customer satisfaction is unmatched. His outstanding IT skills encompass IT security audit and reporting adhering to CISSA Standards.
Similar a Technology Alignment Framework (20)
Pm training (planning and tracking) - Project Leader Ramp-Up 

Pm training (planning and tracking) - Project Leader Ramp-Up
01 Corporate Profile Green Intl_PM Services,Training and Oil & Gas

01 Corporate Profile Green Intl_PM Services,Training and Oil & Gas
Project management methodology pmo example (short sanitised)

Project management methodology pmo example (short sanitised)
Más de Mark S. Mahre
Technology Assessment Framework

There are many aspects, components and dependencies to consider when designing and improving a comprehensive technology environment for passing audits or compliance readiness. This framework was created by Mark Mahre back in 2015, revised in 2017 and improved again in January 2019 to help our clients' leadership, stakeholders and technology management teams understand the breadth of the 'current-state' environment and then help articulate the many moving targets and critical controls requirements for 'future-state' planning, budgeting, executing, testing, operations hand-off, monitoring and sustainability.
Aprio Consulting Services - Cloud, ITFM, Compliance, Innovation, Technology

Aprio's Business Technology Consulting Services offers strategic and tactical technology solutions to help clients improve existing systems and design and implement new solutions to achieve significant returns on their technology investments. Services include evaluating and executing cloud strategies and migrations, assessing technology budgets and risks, and ensuring technology supports business goals. Aprio works with companies having $10 million to $1 billion in revenue to provide guidance across their entire technology landscape.
Governance - Project Management Office Professional Services

This document outlines a project management framework that includes four phases - Initiate, Plan, Execute, and Close. It describes the key documents, approvals, and stakeholders involved at each stage of a project from initial request through completion and sign-off. Key deliverables include scoping analyses, statements of work, project plans, status reports, and lessons learned documentation. The framework is intended to provide governance and standard processes for managing technology projects.
SOC-2 Compliance Status Report sample v10.0

An effective way to communicate to the Stakeholders, Executive Sponsors and Project Team Members, I use this status report format on a bi-monthly basis.
SOC Certification Runbook Template

Trying to manage all the critical controls, testing and procedures to prepare for your SOC Audit? We created a Runbook and Framework to help manage the project execution process before your SOC Audit.
US State Government Case Study

The State Government was using an outdated spreadsheet to track IT costs and needed more transparency. They implemented the ClearCost IT cost modeling tool to accurately track costs across departments and services. The tool was implemented within 6-8 months and replaced the spreadsheet. It provides accurate reporting and a blended chargeback/showback model for budgeting and justifying costs to stakeholders.
ClearCost License & Implementation under $50K

ClearCost has an enterprise web-based solution that can be implemented within 3-weeks and for under $50K. ClearCost provides standard ITFM accounting templates for rapid deployment with a flexible Maturity Model integration. Comes with over 100 customized spreadsheets for Budget Planning and Data Analytics. Our solution offers over 50 TBM web-based customized dashboards with drill-down meta data.
ClearCost

This document lists contact information for 3 leaders of ClearCost, an international consulting firm. It provides the names, titles, locations, phone numbers and emails for Steven Middeldorp, founder and CEO based in Sydney, Australia, Mark Mahre, managing partner of ClearCost US based in Atlanta, Georgia, and Simon Ray, director of ClearCost Europe based in London, England.
ClearCost Introduction 2015

This document provides an introduction and overview of ClearCost, an IT financial management software company. It summarizes ClearCost's products and services, including its Enterprise application for managing IT costs and Explorer tool for analytics and reporting. It also outlines ClearCost's implementation approach including proof of concept pricing, licensing and consulting estimates. Key capabilities of ClearCost's solution include cost transparency, chargeback, asset management, and budget forecasting.
Mark S Mahre - Info-Tech final

- Optimus Consulting is a firm that offers business process management, middleware system integration, and collaborative/web-enabled solutions using leading tools and techniques.
- The VP enjoys the varied challenges of working with Fortune 1000 companies and government agencies to design strong, repeatable processes that replace disjointed practices.
- The firm helps organizations increase agility through business process management to accommodate continuous change and ensure process alignment with business goals.
Spending Request Example V4

The document provides guidelines for enterprise technology finance spending requests at ClearCost Consulting US. It outlines when a spending request is required, such as for purchases over $10,000 or changes to original project scopes. It details the approval limits and processes based on request amounts. For requests under $100,000, only SLT approval is needed, while requests over $500,000 require SLT, CIO and corporate approval. The document walks through each step of the request process from creation to purchase order issuance. Timelines and service level agreements for each stage are also provided.
IT Dashboard User Manual V2.2

The document provides user instructions for version 2.2 of an IT Dashboard tool. It describes the different views available in the dashboard including a Financial View, Services View, and IT PM View. The Financial View shows key performance metrics and allows comparison of budgets to actuals. The Services View displays costs by categories of services provided. The IT PM View tracks top projects by approved budget and spending. Navigation options and filters allow users to view global or regional data by currency, year, and time period.
Capacity Management Process Handbook

This document provides an overview of capacity management processes and concepts. It discusses key ITIL processes like incident management, problem management, change management and others. It then focuses on capacity management, describing the different levels of capacity planning from business to service to component. The document outlines the key activities, roles and artifacts of a capacity management process. It also discusses concepts like capacity planning, storage capacity planning and capacity models.
Data Migrations Framework V33

This document outlines the key stages and activities involved in executing a cloud and data center migration project. It includes planning and initiation, discovery and assessment, design, execution and delivery, and closing stages. Key activities involve developing requirements, strategies, and plans, designing technical specifications, resource planning, compliance reviews, building and migrating in waves, acceptance testing, and reporting lessons learned. The process brings together business stakeholders, consultants, architects, engineers, and subject matter experts to successfully migrate applications and workloads to new target environments.
FundFlow V3.6 Overview (Printable) 08-18-03

FundFlow is a web-based financial management tool developed by Mahre Consulting, Inc. and Everest Technologies, Inc. to monitor project budgets, track costs and vendor invoices, and enhance capital expenditure project success. It allows users to manage projects, budgets, and financial reporting in a centralized system with workflow automation and real-time dashboards. FundFlow addresses common challenges like reconciling vendor invoices, generating capital spending forecasts, and integrating financial data across projects and reports.
Enterprise Project Process Diagram May 2010

The document outlines the detailed life cycle process for IT projects at ClearCost Consulting US. It includes a flow chart that maps the initiation, planning, execution, monitoring and closing phases of a project. Key steps in the process include submitting preliminary plans for approval, developing project documentation like requirements, budgets, test plans and getting sign off at various stages and from appropriate levels of management depending on the project size. The process also addresses handling interdependencies between projects, testing, implementation, integration and decommissioning an existing system.
Más de Mark S. Mahre (18)
Aprio Consulting Services - Cloud, ITFM, Compliance, Innovation, Technology

Aprio Consulting Services - Cloud, ITFM, Compliance, Innovation, Technology
Governance - Project Management Office Professional Services

Governance - Project Management Office Professional Services
Último
HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU

Webinar Recording: https://www.panagenda.com/webinars/hcl-notes-und-domino-lizenzkostenreduzierung-in-der-welt-von-dlau/
DLAU und die Lizenzen nach dem CCB- und CCX-Modell sind für viele in der HCL-Community seit letztem Jahr ein heißes Thema. Als Notes- oder Domino-Kunde haben Sie vielleicht mit unerwartet hohen Benutzerzahlen und Lizenzgebühren zu kämpfen. Sie fragen sich vielleicht, wie diese neue Art der Lizenzierung funktioniert und welchen Nutzen sie Ihnen bringt. Vor allem wollen Sie sicherlich Ihr Budget einhalten und Kosten sparen, wo immer möglich. Das verstehen wir und wir möchten Ihnen dabei helfen!
Wir erklären Ihnen, wie Sie häufige Konfigurationsprobleme lösen können, die dazu führen können, dass mehr Benutzer gezählt werden als nötig, und wie Sie überflüssige oder ungenutzte Konten identifizieren und entfernen können, um Geld zu sparen. Es gibt auch einige Ansätze, die zu unnötigen Ausgaben führen können, z. B. wenn ein Personendokument anstelle eines Mail-Ins für geteilte Mailboxen verwendet wird. Wir zeigen Ihnen solche Fälle und deren Lösungen. Und natürlich erklären wir Ihnen das neue Lizenzmodell.
Nehmen Sie an diesem Webinar teil, bei dem HCL-Ambassador Marc Thomas und Gastredner Franz Walder Ihnen diese neue Welt näherbringen. Es vermittelt Ihnen die Tools und das Know-how, um den Überblick zu bewahren. Sie werden in der Lage sein, Ihre Kosten durch eine optimierte Domino-Konfiguration zu reduzieren und auch in Zukunft gering zu halten.
Diese Themen werden behandelt
- Reduzierung der Lizenzkosten durch Auffinden und Beheben von Fehlkonfigurationen und überflüssigen Konten
- Wie funktionieren CCB- und CCX-Lizenzen wirklich?
- Verstehen des DLAU-Tools und wie man es am besten nutzt
- Tipps für häufige Problembereiche, wie z. B. Team-Postfächer, Funktions-/Testbenutzer usw.
- Praxisbeispiele und Best Practices zum sofortigen Umsetzen
June Patch Tuesday

Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities.
Azure API Management to expose backend services securely

How to use Azure API Management to expose backend service securely
TrustArc Webinar - 2024 Global Privacy Survey

How does your privacy program stack up against your peers? What challenges are privacy teams tackling and prioritizing in 2024?
In the fifth annual Global Privacy Benchmarks Survey, we asked over 1,800 global privacy professionals and business executives to share their perspectives on the current state of privacy inside and outside of their organizations. This year’s report focused on emerging areas of importance for privacy and compliance professionals, including considerations and implications of Artificial Intelligence (AI) technologies, building brand trust, and different approaches for achieving higher privacy competence scores.
See how organizational priorities and strategic approaches to data security and privacy are evolving around the globe.
This webinar will review:
- The top 10 privacy insights from the fifth annual Global Privacy Benchmarks Survey
- The top challenges for privacy leaders, practitioners, and organizations in 2024
- Key themes to consider in developing and maintaining your privacy program
Skybuffer AI: Advanced Conversational and Generative AI Solution on SAP Busin...

Skybuffer AI, built on the robust SAP Business Technology Platform (SAP BTP), is the latest and most advanced version of our AI development, reaffirming our commitment to delivering top-tier AI solutions. Skybuffer AI harnesses all the innovative capabilities of the SAP BTP in the AI domain, from Conversational AI to cutting-edge Generative AI and Retrieval-Augmented Generation (RAG). It also helps SAP customers safeguard their investments into SAP Conversational AI and ensure a seamless, one-click transition to SAP Business AI.
With Skybuffer AI, various AI models can be integrated into a single communication channel such as Microsoft Teams. This integration empowers business users with insights drawn from SAP backend systems, enterprise documents, and the expansive knowledge of Generative AI. And the best part of it is that it is all managed through our intuitive no-code Action Server interface, requiring no extensive coding knowledge and making the advanced AI accessible to more users.
Generating privacy-protected synthetic data using Secludy and Milvus

During this demo, the founders of Secludy will demonstrate how their system utilizes Milvus to store and manipulate embeddings for generating privacy-protected synthetic data. Their approach not only maintains the confidentiality of the original data but also enhances the utility and scalability of LLMs under privacy constraints. Attendees, including machine learning engineers, data scientists, and data managers, will witness first-hand how Secludy's integration with Milvus empowers organizations to harness the power of LLMs securely and efficiently.
Letter and Document Automation for Bonterra Impact Management (fka Social Sol...

Sidekick Solutions uses Bonterra Impact Management (fka Social Solutions Apricot) and automation solutions to integrate data for business workflows.
We believe integration and automation are essential to user experience and the promise of efficient work through technology. Automation is the critical ingredient to realizing that full vision. We develop integration products and services for Bonterra Case Management software to support the deployment of automations for a variety of use cases.
This video focuses on automated letter generation for Bonterra Impact Management using Google Workspace or Microsoft 365.
Interested in deploying letter generation automations for Bonterra Impact Management? Contact us at sales@sidekicksolutionsllc.com to discuss next steps.
System Design Case Study: Building a Scalable E-Commerce Platform - Hiike

This case study explores designing a scalable e-commerce platform, covering key requirements, system components, and best practices.
Monitoring and Managing Anomaly Detection on OpenShift.pdf

Monitoring and Managing Anomaly Detection on OpenShift
Overview
Dive into the world of anomaly detection on edge devices with our comprehensive hands-on tutorial. This SlideShare presentation will guide you through the entire process, from data collection and model training to edge deployment and real-time monitoring. Perfect for those looking to implement robust anomaly detection systems on resource-constrained IoT/edge devices.
Key Topics Covered
1. Introduction to Anomaly Detection
- Understand the fundamentals of anomaly detection and its importance in identifying unusual behavior or failures in systems.
2. Understanding Edge (IoT)
- Learn about edge computing and IoT, and how they enable real-time data processing and decision-making at the source.
3. What is ArgoCD?
- Discover ArgoCD, a declarative, GitOps continuous delivery tool for Kubernetes, and its role in deploying applications on edge devices.
4. Deployment Using ArgoCD for Edge Devices
- Step-by-step guide on deploying anomaly detection models on edge devices using ArgoCD.
5. Introduction to Apache Kafka and S3
- Explore Apache Kafka for real-time data streaming and Amazon S3 for scalable storage solutions.
6. Viewing Kafka Messages in the Data Lake
- Learn how to view and analyze Kafka messages stored in a data lake for better insights.
7. What is Prometheus?
- Get to know Prometheus, an open-source monitoring and alerting toolkit, and its application in monitoring edge devices.
8. Monitoring Application Metrics with Prometheus
- Detailed instructions on setting up Prometheus to monitor the performance and health of your anomaly detection system.
9. What is Camel K?
- Introduction to Camel K, a lightweight integration framework built on Apache Camel, designed for Kubernetes.
10. Configuring Camel K Integrations for Data Pipelines
- Learn how to configure Camel K for seamless data pipeline integrations in your anomaly detection workflow.
11. What is a Jupyter Notebook?
- Overview of Jupyter Notebooks, an open-source web application for creating and sharing documents with live code, equations, visualizations, and narrative text.
12. Jupyter Notebooks with Code Examples
- Hands-on examples and code snippets in Jupyter Notebooks to help you implement and test anomaly detection models.
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
Skybuffer SAM4U tool for SAP license adoption

Manage and optimize your license adoption and consumption with SAM4U, an SAP free customer software asset management tool.
SAM4U, an SAP complimentary software asset management tool for customers, delivers a detailed and well-structured overview of license inventory and usage with a user-friendly interface. We offer a hosted, cost-effective, and performance-optimized SAM4U setup in the Skybuffer Cloud environment. You retain ownership of the system and data, while we manage the ABAP 7.58 infrastructure, ensuring fixed Total Cost of Ownership (TCO) and exceptional services through the SAP Fiori interface.
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Simplify your search for a reliable Python development partner! This list presents the top 10 trusted US providers offering comprehensive Python development services, ensuring your project's success from conception to completion.
Choosing The Best AWS Service For Your Website + API.pptx

Have you ever been confused by the myriad of choices offered by AWS for hosting a website or an API?
Lambda, Elastic Beanstalk, Lightsail, Amplify, S3 (and more!) can each host websites + APIs. But which one should we choose?
Which one is cheapest? Which one is fastest? Which one will scale to meet our needs?
Join me in this session as we dive into each AWS hosting service to determine which one is best for your scenario and explain why!
A Comprehensive Guide to DeFi Development Services in 2024

DeFi represents a paradigm shift in the financial industry. Instead of relying on traditional, centralized institutions like banks, DeFi leverages blockchain technology to create a decentralized network of financial services. This means that financial transactions can occur directly between parties, without intermediaries, using smart contracts on platforms like Ethereum.
In 2024, we are witnessing an explosion of new DeFi projects and protocols, each pushing the boundaries of what’s possible in finance.
In summary, DeFi in 2024 is not just a trend; it’s a revolution that democratizes finance, enhances security and transparency, and fosters continuous innovation. As we proceed through this presentation, we'll explore the various components and services of DeFi in detail, shedding light on how they are transforming the financial landscape.
At Intelisync, we specialize in providing comprehensive DeFi development services tailored to meet the unique needs of our clients. From smart contract development to dApp creation and security audits, we ensure that your DeFi project is built with innovation, security, and scalability in mind. Trust Intelisync to guide you through the intricate landscape of decentralized finance and unlock the full potential of blockchain technology.
Ready to take your DeFi project to the next level? Partner with Intelisync for expert DeFi development services today!
Ocean lotus Threat actors project by John Sitima 2024 (1).pptx

Ocean Lotus cyber threat actors represent a sophisticated, persistent, and politically motivated group that poses a significant risk to organizations and individuals in the Southeast Asian region. Their continuous evolution and adaptability underscore the need for robust cybersecurity measures and international cooperation to identify and mitigate the threats posed by such advanced persistent threat groups.
Best 20 SEO Techniques To Improve Website Visibility In SERP

Boost your website's visibility with proven SEO techniques! Our latest blog dives into essential strategies to enhance your online presence, increase traffic, and rank higher on search engines. From keyword optimization to quality content creation, learn how to make your site stand out in the crowded digital landscape. Discover actionable tips and expert insights to elevate your SEO game.
Trusted Execution Environment for Decentralized Process Mining

Presentation of the paper "Trusted Execution Environment for Decentralized Process Mining" given during the CAiSE 2024 Conference in Cyprus on June 7, 2024.
Último (20)
Deep Dive: Getting Funded with Jason Jason Lemkin Founder & CEO @ SaaStr

Deep Dive: Getting Funded with Jason Jason Lemkin Founder & CEO @ SaaStr
HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU

HCL Notes und Domino Lizenzkostenreduzierung in der Welt von DLAU
Nordic Marketo Engage User Group_June 13_ 2024.pptx

Nordic Marketo Engage User Group_June 13_ 2024.pptx
Azure API Management to expose backend services securely

Azure API Management to expose backend services securely
Skybuffer AI: Advanced Conversational and Generative AI Solution on SAP Busin...

Skybuffer AI: Advanced Conversational and Generative AI Solution on SAP Busin...
Generating privacy-protected synthetic data using Secludy and Milvus

Generating privacy-protected synthetic data using Secludy and Milvus
Letter and Document Automation for Bonterra Impact Management (fka Social Sol...

Letter and Document Automation for Bonterra Impact Management (fka Social Sol...
System Design Case Study: Building a Scalable E-Commerce Platform - Hiike

System Design Case Study: Building a Scalable E-Commerce Platform - Hiike
Monitoring and Managing Anomaly Detection on OpenShift.pdf

Monitoring and Managing Anomaly Detection on OpenShift.pdf
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Your One-Stop Shop for Python Success: Top 10 US Python Development Providers
Choosing The Best AWS Service For Your Website + API.pptx

Choosing The Best AWS Service For Your Website + API.pptx
A Comprehensive Guide to DeFi Development Services in 2024

A Comprehensive Guide to DeFi Development Services in 2024
Ocean lotus Threat actors project by John Sitima 2024 (1).pptx

Ocean lotus Threat actors project by John Sitima 2024 (1).pptx
Best 20 SEO Techniques To Improve Website Visibility In SERP

Best 20 SEO Techniques To Improve Website Visibility In SERP
Trusted Execution Environment for Decentralized Process Mining

Trusted Execution Environment for Decentralized Process Mining
Technology Alignment Framework
- 1. Monitoring AProject Charter Planning Execution & Milestone Tracking Design, Governance, Risk, Compliance & Process Mapping, Approach & Budgeting Mark S Mahre Aprio Technology Alignment Framework ASSESSMENTDISCOVERY Suitability, Remediate, Test & Implement CONTROL CXO s, CISO, Directors, SME s, Analysts, Project Managers & Consultants Resources , Timeline, PMO & Gap Analysis Sponsors & Stakeholders, Business Owners Strategy, Requirements & Roadmap Business Case Project Scope Success Criteria Requirements Objectives Approvals Project Design Project Tasks Risk Assessment As-Is Assessment Project Financials Project Scheduling Project Kick-Off Resource Scheduling Gap Assessment Future State Mapping Risk Assessment Identify Required Controls Governance & Process Data & Security Mandates Change Controls Authentication Encryption Controls IncidentManagement KPI s & Metrics Goals GRC & Readiness Employee Training Controls Mapping Systems & Infrastructure SOP s & Alignment Operational Effectiveness Risk Mgmt. Controls Testing Data Security Monitoring Ops Review & Enhancements Dashboards, KPI s & Analytics Quarterly Leadership Meetings DESIGN & BUILD TEST & EXECUTE Controls, Analytics & Sustainability Risk Mitigations Suitability of Design Data RPO/RTO DR/BCP Strategy Remediation Testing Cloud / Co-Lo Contracts Mahre 2017 ALIGNMENT Operations / Cloud Task % Task % Task % Task % Task % Task % Task % Business Case Project Requirements Confirm Milestones Project Execution Kickoff Governance Framework Governance Execution Operations Mgmt. Project Scope of Work Project Plan & Budgets Create Templates Assessment Meeting Critical Controls Testing Critical Controls in Place Risk Mgmt. Controls Data Security Mandates Risk Assessment Approach Identify Partnerships Employee SOC Intro Meeting Change Controls Tested Change MGMG. Controls Network Monitoring Success Criteria Defined As-Is Assessment (Gaps) To-Be (Targets) Change Control Process Network Penetration Testing Help Desk System in Place Data Security Monitoring Road Map (Milestones) Project Financials People/Resources Critical Controls Accuracy Client Data Security Testing System Uptime Reporting SW License Management Security Mandates Schedule Quarterly Mtg. Readiness Assessment Security Governance Process Network Monitoring Results Cybersecurity & Risk Contracts Management Approval Signoffs Resource Scheduling System Description Risk Avoidance Governance Cloud Testing Results Data Encryption Reporting DR / BCP Testing Resources Identified PMO – New Project Information Security Cyber Risk Analysis/Metrics Cloud Monitoring Results Client Satisfaction Surveys Help Desk Mgmt. Blackout Dates Identified Status Meeting Schedule Employee Handbook Infrastructure & Network Security Awareness Education Final PMO Meetings Provisioning Mgmt. Project Budget Plan Timeline-Milestones Plan Asset Inventory - CMDB Cloud Stack Review Incident Response Testing DR/BCP 2018 Plan in Place Decommissioning Mgmt. Contact Legal Rep. Operations Hand-Off Plan Change MGMT. Strategy End-2-End Data Encryption DR/BCP Testing Next Year Planning Cloud / TAM Mgmt. Identify Stakeholders Communications Plan Building Security Plan HIPAA / PHI Mandates Readiness Reviews Breach Communication Plan FY Budgeting Technology Strategy Cost Optimization Plan Policies & Procedures Regulations Policies Change Mgmt. Process Availability Mgmt Framework Compliance Readiness Operations Strategy Project Org. Chart Strategic Sourcing Portfolio Mgmt. Framework Application Mgmt. CMDB Operations Hand-Off Notice IT Finance Analytics CXO & Leadership CISO CIO COO Legal CFO PMO Aprio Team Security Team IT Team Operations Team Contracts Team Finance Team Consultants Month 1 Month 2 Month 3 Month 4 & 5 Month 6 & 7 Month 8 - 11 Month 12 Aprio | Version 25.1 | September 2019
