The Gartner IAM Program Maturity Model
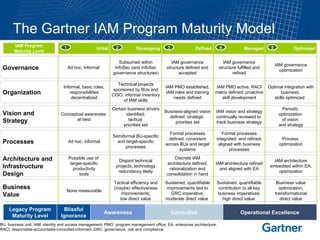
- 1. BU: business unit; IAM: identity and access management; PMO: program management office; EA: enterprise architecture; RACI: responsible-accountable-consulted-informed; GRC: governance, risk and compliance The Gartner IAM Program Maturity Model Developing Optimized Initial Defined Managed 2 5 1 3 4 IAM Program Maturity Level Business Value Architecture and Infrastructure Design Processes Vision and Strategy Organization Conceptual awareness at best Certain business drivers identified; tactical priorities set Business-aligned vision defined; strategic priorities set IAM vision and strategy continually reviewed to track business strategy Periodic optimization of vision and strategy Informal, basic roles, responsibilities decentralized Technical projects sponsored by BUs and CISO; informal inventory of IAM skills IAM PMO established, IAM roles and training needs defined IAM PMO active, RACI matrix defined; proactive skill development Optimal integration with business; skills optimized Ad hoc, informal Semiformal BU-specific and target-specific processes Formal processes defined, consistent across BUs and target systems Formal processes integrated and refined; aligned with business processes Process optimization Possible use of target-specific productivity tools Disjoint technical projects; technology redundancy likely Discrete IAM architecture defined; rationalization and consolidation in hand IAM architecture refined and aligned with EA IAM architecture embedded within EA; optimization None measurable Tactical efficiency and (maybe) effectiveness improvements; low direct value Sustained, quantifiable improvements tied to GRC imperative; moderate direct value Sustained, quantifiable contribution to all key business imperatives; high direct value Business value optimization; transformational direct value Blissful Ignorance Awareness Corrective Operational Excellence Legacy Program Maturity Level Governance Ad hoc, informal Subsumed within InfoSec (and InfoSec governance structures) IAM governance structure defined and accepted IAM governance structure fulfilled and refined IAM governance optimization
Notas del editor
- The Gartner IAM Program Maturity Model considers the maturity level of five aspects of an IAM program: Governance: Does IAM have executive sponsorship? Is a formal governance structure in place? Organization: Is there a program management office (PMO) with a charter to manage the IAM program and its portfolio of projects, applications and products? Are the roles of different constituents (people and organizational functions) well defined and documented, typically in a responsible, accountable, consulted and informed (RACI) matrix ? Is there a personal development program in place to ensure that participants' skills meet program needs? Vision and Strategy: Is there a clearly defined, enterprisewide vision and strategy for IAM? Are formal planning mechanisms in place? Processes: What is the formalization, integration, organizational alignment, and so on of the IAM processes? This may be considered in abstract or (better) based on a detailed process maturity assessment. Architecture and Infrastructure Design: Is there an IAM architecture and overall infrastructure design? To what degree is this aligned with or embedded within enterprise architecture (EA)? Note that this aspect of IAM program maturity should not be judged on the kind of IAM technologies that an enterprise has selected and implemented; for example, lack of a user provisioning tool doesn't indicate immaturity, as there may be several reasons why an enterprise has chosen a different technology set to address identity-administration process automation and intelligence needs. Business Value: How — and to what degree — does IAM contribute to security efficiency, security effectiveness (including governance, risk and compliance [GRC] management) and business enablement (direct business value)? The IAM program maturity criteria are summarized above.