Demo preorder-stack
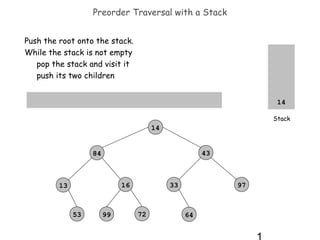
- 1. Preorder Traversal with a Stack Push the root onto the stack. While the stack is not empty pop the stack and visit it push its two children 14 84 13 53 06 99 72 43 33 64 97 51 25 14 Stack 14 43 84 16 13 53 99 33 72 97 64
- 2. Preorder Traversal with a Stack Push the root onto the stack. While the stack is not empty pop the stack and visit it push its two children 84 43 14 84 13 53 06 99 72 43 33 64 97 51 25 Stack 14 43 84 16 13 53 99 33 72 97 64
- 3. Preorder Traversal with a Stack Push the root onto the stack. While the stack is not empty pop the stack and visit it push its two children 13 16 43 14 84 13 53 06 99 72 43 33 64 97 51 25 Stack 14 43 84 16 13 53 99 33 72 97 64
- 4. Preorder Traversal with a Stack Push the root onto the stack. While the stack is not empty pop the stack and visit it push its two children 53 16 43 14 84 13 53 06 99 72 43 33 64 97 51 25 Stack 14 43 84 16 13 53 99 33 72 97 64
- 5. Preorder Traversal with a Stack Push the root onto the stack. While the stack is not empty pop the stack and visit it push its two children 16 43 14 84 13 53 06 99 72 43 33 64 97 51 25 Stack 14 43 84 16 13 53 99 33 72 97 64
- 6. Preorder Traversal with a Stack Push the root onto the stack. While the stack is not empty pop the stack and visit it push its two children 99 72 43 14 84 13 53 16 99 72 43 33 64 97 51 25 Stack 14 43 84 16 6 13 53 99 33 72 97 64
- 7. Preorder Traversal with a Stack Push the root onto the stack. While the stack is not empty pop the stack and visit it push its two children 72 43 14 84 13 53 16 99 72 43 33 64 97 51 25 Stack 14 43 84 16 13 53 99 33 72 97 64
- 8. Preorder Traversal with a Stack Push the root onto the stack. While the stack is not empty pop the stack and visit it push its two children 14 84 13 53 16 99 72 43 33 64 97 51 25 43 Stack 14 43 84 16 13 53 99 33 72 97 64
- 9. Preorder Traversal with a Stack Push the root onto the stack. While the stack is not empty pop the stack and visit it push its two children 33 97 14 84 13 53 16 99 72 43 33 64 97 51 25 Stack 14 43 84 16 13 53 99 33 72 97 64
- 10. Preorder Traversal with a Stack Push the root onto the stack. While the stack is not empty pop the stack and visit it push its two children 64 97 14 84 13 53 16 99 72 43 33 64 97 51 25 Stack 14 43 84 16 13 53 99 33 72 97 64
- 11. Preorder Traversal with a Stack Push the root onto the stack. While the stack is not empty pop the stack and visit it push its two children 14 84 13 53 16 99 72 43 33 64 97 51 25 97 Stack 14 43 84 16 13 53 99 33 72 97 64
- 12. Preorder Traversal with a Stack Push the root onto the stack. While the stack is not empty pop the stack and visit it push its two children 14 84 13 53 16 99 72 43 33 64 97 51 25 Stack 14 43 84 16 13 53 99 33 72 97 64
- 13. Preorder Traversal with a Stack Push the root onto the stack. While the stack is not empty pop the stack and visit it push its two children 14 84 13 53 16 99 72 43 33 64 97 51 25 Stack 14 43 84 16 13 53 99 33 72 97 64
