Software defect estimation using machine learning algorithms
•Descargar como DOCX, PDF•
0 recomendaciones•298 vistas
output screens, project output, python projects, machinelearning projects, data science projects, Artificial Intelegance projects, support vector machine, ramdom forest tree, Dession tree, linear Regression, logistic regression, Feature Selection, Naive Bayes, Machine learning Algorithms, Dimensionality Reduction Algorithms, Gradient Boosting algorithm, Logistic Regression, TensorFlow,Scikit-Learn,Numpy,Keras,PyTorch ,LightGBM, Eli5 ,SciPy,Theano,Pandas,imageProcessing Deep Learning,
Denunciar
Compartir
Denunciar
Compartir
Recomendados
Recomendados
Cloud computing is used to define a new class of computing that is based on the network technology. Cloud computing takes place over the internet. It comprises of a collection of integrated and networked hardware, software and internet infrastructures. These infrastructures are used to provide various services to the users. Distributed computing comprises of multiple software components that belong to multiple computers. The system works or runs as a single system. Cloud computing can be referred to as a form that originated from distributed computing and virtualization.Cloud Computing & Distributed Computing

Cloud Computing & Distributed ComputingAmity University | FMS - DU | IMT | Stratford University | KKMI International Institute | AIMA | DTU
Más contenido relacionado
La actualidad más candente
Cloud computing is used to define a new class of computing that is based on the network technology. Cloud computing takes place over the internet. It comprises of a collection of integrated and networked hardware, software and internet infrastructures. These infrastructures are used to provide various services to the users. Distributed computing comprises of multiple software components that belong to multiple computers. The system works or runs as a single system. Cloud computing can be referred to as a form that originated from distributed computing and virtualization.Cloud Computing & Distributed Computing

Cloud Computing & Distributed ComputingAmity University | FMS - DU | IMT | Stratford University | KKMI International Institute | AIMA | DTU
La actualidad más candente (20)
IMAGE QUALITY ASSESSMENT- A SURVEY OF RECENT APPROACHES 

IMAGE QUALITY ASSESSMENT- A SURVEY OF RECENT APPROACHES
Similar a Software defect estimation using machine learning algorithms
Similar a Software defect estimation using machine learning algorithms (20)
Prediction of quality for different type of winebased on different feature se...

Prediction of quality for different type of winebased on different feature se...
Prediction of quality for different type of winebased on different feature se...

Prediction of quality for different type of winebased on different feature se...
Qrsvm (fast and communication efficient algorithm for distributed support vec...

Qrsvm (fast and communication efficient algorithm for distributed support vec...
Qrsvm (fast and communication efficient algorithm for distributed support vec...

Qrsvm (fast and communication efficient algorithm for distributed support vec...
Feature extraction for classifying students based on theirac ademic performance

Feature extraction for classifying students based on theirac ademic performance
Comparison of machine learning methods for breast cancer diagnosis

Comparison of machine learning methods for breast cancer diagnosis
Dynamic autoselection and autotuning of machine learning models forcloud netw...

Dynamic autoselection and autotuning of machine learning models forcloud netw...
A new architecture of internet of things and big data ecosystem for

A new architecture of internet of things and big data ecosystem for
10.sentiment analysis of customer product reviews using machine learni

10.sentiment analysis of customer product reviews using machine learni
Driver drowsiness monitoring system using visual behaviour and machine learning

Driver drowsiness monitoring system using visual behaviour and machine learning
Hybrid feature selection using correlation coefficient and particle swarm opt...

Hybrid feature selection using correlation coefficient and particle swarm opt...
Support Vector Machines USING MACHINE LEARNING HOW IT WORKS

Support Vector Machines USING MACHINE LEARNING HOW IT WORKS
Recommender system with artificial intelligence for fitness assistance system

Recommender system with artificial intelligence for fitness assistance system
Recommender system with artificial intelligence for fitness assistance system

Recommender system with artificial intelligence for fitness assistance system
Network intrusion detection using supervised machine learning technique with ...

Network intrusion detection using supervised machine learning technique with ...
IRJET - Cognitive based Emotion Analysis of a Child Reading a Book

IRJET - Cognitive based Emotion Analysis of a Child Reading a Book
Más de Venkat Projects
Más de Venkat Projects (20)
1.AUTOMATIC DETECTION OF DIABETIC RETINOPATHY USING CNN.docx

1.AUTOMATIC DETECTION OF DIABETIC RETINOPATHY USING CNN.docx
12.BLOCKCHAIN BASED MILK DELIVERY PLATFORM FOR STALLHOLDER DAIRY FARMERS IN K...

12.BLOCKCHAIN BASED MILK DELIVERY PLATFORM FOR STALLHOLDER DAIRY FARMERS IN K...
10.ATTENDANCE CAPTURE SYSTEM USING FACE RECOGNITION.docx

10.ATTENDANCE CAPTURE SYSTEM USING FACE RECOGNITION.docx
9.IMPLEMENTATION OF BLOCKCHAIN IN FINANCIAL SECTOR TO IMPROVE SCALABILITY.docx

9.IMPLEMENTATION OF BLOCKCHAIN IN FINANCIAL SECTOR TO IMPROVE SCALABILITY.docx
8.Geo Tracking Of Waste And Triggering Alerts And Mapping Areas With High Was...

8.Geo Tracking Of Waste And Triggering Alerts And Mapping Areas With High Was...
Image Forgery Detection Based on Fusion of Lightweight Deep Learning Models.docx

Image Forgery Detection Based on Fusion of Lightweight Deep Learning Models.docx
6.A FOREST FIRE IDENTIFICATION METHOD FOR UNMANNED AERIAL VEHICLE MONITORING ...

6.A FOREST FIRE IDENTIFICATION METHOD FOR UNMANNED AERIAL VEHICLE MONITORING ...
4.LOCAL DYNAMIC NEIGHBORHOOD BASED OUTLIER DETECTION APPROACH AND ITS FRAMEWO...

4.LOCAL DYNAMIC NEIGHBORHOOD BASED OUTLIER DETECTION APPROACH AND ITS FRAMEWO...
Application and evaluation of a K-Medoidsbased shape clustering method for an...

Application and evaluation of a K-Medoidsbased shape clustering method for an...
OPTIMISED STACKED ENSEMBLE TECHNIQUES IN THE PREDICTION OF CERVICAL CANCER US...

OPTIMISED STACKED ENSEMBLE TECHNIQUES IN THE PREDICTION OF CERVICAL CANCER US...
1.AUTOMATIC DETECTION OF DIABETIC RETINOPATHY USING CNN.docx

1.AUTOMATIC DETECTION OF DIABETIC RETINOPATHY USING CNN.docx
9.data analysis for understanding the impact of covid–19 vaccinations on the ...

9.data analysis for understanding the impact of covid–19 vaccinations on the ...
6.iris recognition using machine learning technique

6.iris recognition using machine learning technique
5.local community detection algorithm based on minimal cluster

5.local community detection algorithm based on minimal cluster
4.detection of fake news through implementation of data science application

4.detection of fake news through implementation of data science application
Último
This presentation was provided by William Mattingly of the Smithsonian Institution, during the fourth segment of the NISO training series "AI & Prompt Design." Session Four: Structured Data and Assistants, was held on April 25, 2024.Mattingly "AI & Prompt Design: Structured Data, Assistants, & RAG"

Mattingly "AI & Prompt Design: Structured Data, Assistants, & RAG"National Information Standards Organization (NISO)
God is a creative God Gen 1:1. All that He created was “good”, could also be translated “beautiful”. God created man in His own image Gen 1:27. Maths helps us discover the beauty that God has created in His world and, in turn, create beautiful designs to serve and enrich the lives of others.
Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...

Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...christianmathematics
Último (20)
SECOND SEMESTER TOPIC COVERAGE SY 2023-2024 Trends, Networks, and Critical Th...

SECOND SEMESTER TOPIC COVERAGE SY 2023-2024 Trends, Networks, and Critical Th...
Mattingly "AI & Prompt Design: Structured Data, Assistants, & RAG"

Mattingly "AI & Prompt Design: Structured Data, Assistants, & RAG"
Presentation by Andreas Schleicher Tackling the School Absenteeism Crisis 30 ...

Presentation by Andreas Schleicher Tackling the School Absenteeism Crisis 30 ...
Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...

Explore beautiful and ugly buildings. Mathematics helps us create beautiful d...
Unit-IV; Professional Sales Representative (PSR).pptx

Unit-IV; Professional Sales Representative (PSR).pptx
Z Score,T Score, Percential Rank and Box Plot Graph

Z Score,T Score, Percential Rank and Box Plot Graph
Unit-V; Pricing (Pharma Marketing Management).pptx

Unit-V; Pricing (Pharma Marketing Management).pptx
Web & Social Media Analytics Previous Year Question Paper.pdf

Web & Social Media Analytics Previous Year Question Paper.pdf
Software defect estimation using machine learning algorithms
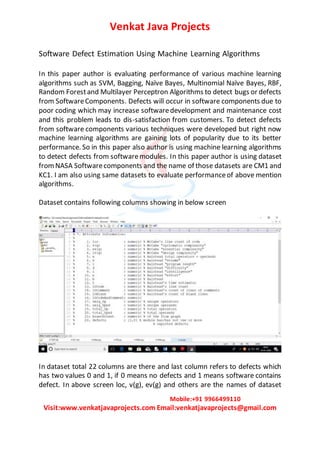
- 1. Venkat Java Projects Mobile:+91 9966499110 Visit:www.venkatjavaprojects.com Email:venkatjavaprojects@gmail.com Software Defect Estimation Using Machine Learning Algorithms In this paper author is evaluating performance of various machine learning algorithms such as SVM, Bagging, Naïve Bayes, Multinomial Naïve Bayes, RBF, Random Forestand Multilayer Perceptron Algorithms to detect bugs or defects from SoftwareComponents. Defects will occur in software components due to poor coding which may increase softwaredevelopment and maintenance cost and this problem leads to dis-satisfaction from customers. To detect defects from software components various techniques were developed but right now machine learning algorithms are gaining lots of popularity due to its better performance. So in this paper also author is using machine learning algorithms to detect defects from softwaremodules. In this paper author is using dataset fromNASA Softwarecomponents and the name of those datasets are CM1 and KC1. I am also using same datasets to evaluate performanceof above mention algorithms. Dataset contains following columns showing in below screen In dataset total 22 columns are there and last column refers to defects which has two values 0 and 1, if 0 means no defects and 1 means software contains defect. In above screen loc, v(g), ev(g) and others are the names of dataset
- 2. Venkat Java Projects Mobile:+91 9966499110 Visit:www.venkatjavaprojects.com Email:venkatjavaprojects@gmail.com columns. Beside all columns you can see column description also. This datasets I saved inside ‘dataset’ folder. Using those datasets we will train machine learning algorithms and generate a model and whenever user gives new test software values then algorithm will apply train model on that new test values to predict whether given software values contains defect or not. Algorithm details SVM Algorithm: Machine learning involves predicting and classifying data and to do so we employ various machinelearning algorithms according to the dataset. SVM or Support Vector Machine is a linear model for classification and regression problems. Itcan solve linear and non-linear problems and work well for many practical problems. The idea of SVMis simple: The algorithm creates a line or a hyper plane which separates the data into classes. In machinelearning, the radial basis function kernel, or RBF kernel, is a popular kernel function used in various kernelized learning algorithms. In particular, it is commonly used in support vector machine classification. As a simple example, for a classification taskwith only twofeatures (likethe imageabove),youcan think of a hyperplane as a line that linearly separates and classifies a set of data. Intuitively, the further from the hyper plane our data points lie, the more confident we are that they have been correctly classified. We therefore want our data points to be as far away from the hyper plane as possible, while still being on the correct side of it. So when new testing data is added, whatever side of the hyper plane it lands will decide the class that we assign to it. Random Forest Algorithm: it’s an ensemblealgorithm which means internally it will use multiple classifier algorithms to build accurate classifier model. Internally this algorithm will use decision tree algorithm to generate it train model for classification. Bagging: This algorithms work similar to learning tree the only difference is voting conceptwhere each class will get majority of votes based on values close
- 3. Venkat Java Projects Mobile:+91 9966499110 Visit:www.venkatjavaprojects.com Email:venkatjavaprojects@gmail.com to it and that class will form a branch. If new values arrived then that new value will applied on entire tree to get close matching class. Naive Bayes:Naive Bayes which is one of the most commonly used algorithms for classifying problems is simple probabilistic classifier and is based on Bayes Theorem. It determines the probability of each features occurring in each class and returns the outcome with the highest probability. Multinomial Naive Bayes: Multinomial Naive Bayes classifier is obtained by enlarging Naive Bayes classifier. Differently from the Naive Bayes classifier, a multinomial distribution is used for each features. Multilayer Perceptron: Multilayer Perceptron which is one of the types of Neural Networks comprises of one input layer, one output layer and at least one or more hidden layers. This algorithm transfers the data from the input layer to the output layer, which is called feed forward. Fortraining, the back propagation technique is used. One hidden layer with (attributes + classes) / 2 units are used for this experiment. Each dataset has 22 attributes and 2 classes which are false and true. We determined the learning rate as 0.3 and momentum as 0.2 for each dataset. RadialBasis Function: Radial Basis Function Network includes an input vector for classification, a layer of RBF neurons, and an output layer which has a node for each class. Dot products method is used between inputs and weights and for activation sigmoidal activation functions are used in MLP while in RBFN between inputs and weights Euclidean distances method is used and as activation function, Gaussian activation functions are used. Screen shots To run this project double click on ‘run.bat’ file to get below screen
- 4. Venkat Java Projects Mobile:+91 9966499110 Visit:www.venkatjavaprojects.com Email:venkatjavaprojects@gmail.com In above screenclick on‘Upload Nasa Software Dataset’ buttonto upload dataset In above screen uploading ‘CM1.txt’ dataset and information of this dataset you can read from internet of ‘DATASET_INFORMATION’ file from above screen. After uploading dataset will get below screen
- 5. Venkat Java Projects Mobile:+91 9966499110 Visit:www.venkatjavaprojects.com Email:venkatjavaprojects@gmail.com In above screen we can see total dataset size and training size records and testing size records application obtained from dataset to build train model. Now click on ‘Run Multilayer Perceptron Algorithm’ button to generate model and to get its accuracy In above screen we can see multilayer perceptron fmeasure, recall and accuracy values and scroll down in text area to see all details.
- 6. Venkat Java Projects Mobile:+91 9966499110 Visit:www.venkatjavaprojects.com Email:venkatjavaprojects@gmail.com In above screen we can see multilayer perceptronaccuracyis 93%. Similarly you click on all other algorithms button to see their accuracies and then click on ‘All Algorithms Accuracy Graph’ button to see all algorithms accuracy in graph to understand which algorithm is giving high accuracy.
- 7. Venkat Java Projects Mobile:+91 9966499110 Visit:www.venkatjavaprojects.com Email:venkatjavaprojects@gmail.com In above graph x-axis represents algorithm name and y-axis represents accuracy of those algorithms. In all algorithms we can see MLP, Bagging is giving better accuracy.
