INFOGRAPHIC: IS YOUR PATIENT DATA PROTECTED?
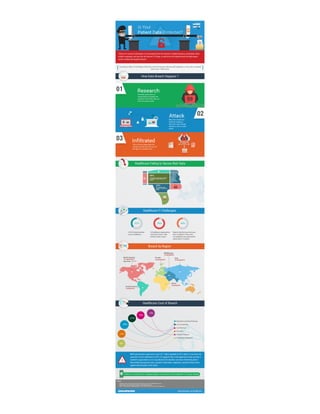
According to OCR, there were 253 breaches affecting 500 individuals or more w/ a combined loss of over 112M records. Healthcare Failing to secure their data 48% encountered a data breach or failed a compliance audit in the last 12 months 26% are protecting data because of a past data breach 138% jump in number of breached healthcare records since 2012 The estimated cost for HIPAA breaches since 2009 has reached over 31 billion dollars. Healthcare IT Challenges 42% of 2014 data breaches were in healthcare 90% of healthcare organizations have had at least 1 data breach in past 2 years 40% report that they have had more than 5 incidents of the entire U.S population was impacted by cybercrime in 9 months Healthcare Cost of Breach 29% Reputation and brand damage 21% lost productivity 19% Lost Revenue 12% Forensics 10% Technical Support 8% Compliance Regulatory With Data breaches expected to reach $2.1 trillion globally by 2019, which is four times the expected cost for cybercrime in 2015, It's apparent that a new approach to data security is needed if organizations are to stay ahead of the attackers and more effectively protect their intellectual property, data, customer information, employees, and their bottom lines against data breaches in the future Contact us to learn how to safeguard against such breaches and implement it security strategy.
Recomendados
Más contenido relacionado
La actualidad más candente
La actualidad más candente (20)
Destacado
Destacado (13)
Similar a INFOGRAPHIC: IS YOUR PATIENT DATA PROTECTED?
Similar a INFOGRAPHIC: IS YOUR PATIENT DATA PROTECTED? (20)
Más de Diaspark
Más de Diaspark (15)
Último
Último (20)
INFOGRAPHIC: IS YOUR PATIENT DATA PROTECTED?
- 1. According to Office Of Civil Rights (OCR), there were 253 breaches affecting 500 individuals or more with a combined loss of over 112M records How Data Breach Happens ? 01 ResearchCriminals spend hours on researching and targeting the weakness from where they can enter the system easily 03 Infiltrated This is the last stage where the attackers get the data and can use the data as a randsome tool 02Attack When the criminal has found the weakness, they try to enter through network or does a social attack Healthcare Failing to Secure their Data 63 INCIDENTS 14 INCIDENTS 2 INCIDENTS Middle East Asia Africa With Data breaches expected to reach $2.1 trillion globally by 2019, which is four times the expected cost for cybercrime in 2015, it's apparent that a new approach to data security is needed if organizations are to stay ahead of the attackers and more effectively protect their intellectual property, data, customer information, employees, and their bottom lines against data breaches in the future. Contact us to learn how to safeguard against such breaches and implement IT security strategy • Healthcare IT News - HIPAA data breaches climb 138 percent - http://www.healthcareitnews.com • Cyberresponse - Data breaches by the numbers - https://cybersponse.com • Forbes – Data breaches in healthcare totaled over 112 million records in 2015 - http://www.forbes.com/ Source www.diaspark.com/healthcare 94 INCIDENTS Europe 2 INCIDENTS South America 707 INCIDENTS United States – 671 North America Of 2014 data breaches were in healthcare 42% Of healthcare organizations have had at least 1 data breach in past 2 years 90% Reports that they have had more than 5 incidents of the entire U.S population was impacted by cybercrime in 9 months 40% Encountered a data breach or failed a compliance audit in the last 12 months Are protecting data because of a past data breach Increaed in number of breached healthcare records since 2012 Healthcare IT Challenges Breach by Region Healthcare Cost of Breach 29% 21% 19% 12% 10% 8% Elizabeth Kim, research analyst at Gartner Reputation and Brand Damage Lost Productivity Lost Revenue Forensics Technical Support Compliance Regulatory Is Your Patient Data Protected? Login Password “Interest in security technologies is increasingly driven by elements of digital business, particularly cloud, mobile computing, and now also the Internet of Things, as well as by the sophisticated and high-impact nature of advanced targeted attacks” 48% 26% 138%
