[Infographic] M-Trends 2016
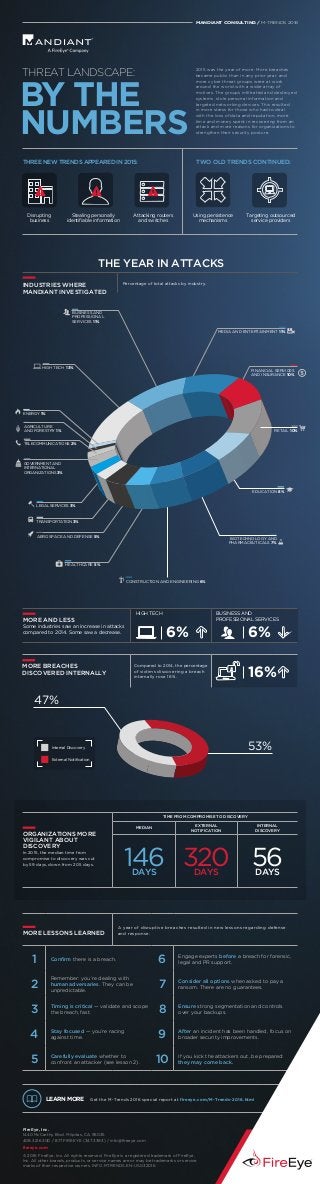
- 1. 2015 was the year of more. More breaches became public than in any prior year, and more cyber threat groups were at work around the world with a wider array of motives. The groups infiltrated and destroyed systems, stole personal information and targeted networking devices. This resulted in more stress for those who had to deal with the loss of data and reputation, more time and money spent in recovering from an attack and more reasons for organizations to strengthen their security posture. BY THE NUMBERS THREAT LANDSCAPE: MANDIANT CONSULTING / M-TRENDS 2016 ENERGY 1% AGRICULTURE AND FORESTRY 1% HIGH TECH 13% GOVERNMENT AND INTERNATIONAL ORGANIZATIONS 3% LEGAL SERVICES 3% TRANSPORTATION 3% BUSINESS AND PROFESSIONAL SERVICES 11% MEDIA AND ENTERTAINMENT 11% FINANCIAL SERVICES AND INSURANCE 10% RETAIL 10% EDUCATION 8% BIOTECHNOLOGY AND PHARMACEUTICALS 7% CONSTRUCTION AND ENGINEERING 6% HEALTHCARE 5% AEROSPACE AND DEFENSE 5% TELECOMMUNICATIONS 2% ORGANIZATIONS MORE VIGILANT ABOUT DISCOVERY In 2015, the median time from compromise to discovery was cut by 59 days, down from 205 days. TIME FROM COMPROMISE TO DISCOVERY MEDIAN EXTERNAL NOTIFICATION INTERNAL DISCOVERY 146DAYS 320DAYS 56DAYS MORE LESSONS LEARNED A year of disruptive breaches resulted in new lessons regarding defense and response. 1 Confirm there is a breach. 6 Engage experts before a breach for forensic, legal and PR support. 2 Remember: you’re dealing with human adversaries. They can be unpredictable. 7 Consider all options when asked to pay a ransom. There are no guarantees. 3 Timing is critical — validate and scope the breach, fast. 8 Ensure strong segmentation and controls over your backups. 4 Stay focused — you’re racing against time. 9 After an incident has been handled, focus on broader security improvements. 5 Carefully evaluate whether to confront an attacker (see lesson 2). 10 If you kick the attackers out, be prepared: they may come back. LEARN MORE Get the M-Trends 2016 special report at fireeye.com/M-Trends-2016.html FireEye, Inc. 1440 McCarthy Blvd. Milpitas, CA 95035 408.321.6300 / 877.FIREEYE (347.3393) / info@fireeye.com fireeye.com © 2016 FireEye, Inc. All rights reserved. FireEye is a registered trademark of FireEye, Inc. All other brands, products, or service names are or may be trademarks or service marks of their respective owners. INFO.MTRENDS.EN-US.032016 Disrupting business Stealing personally identifiable information Attacking routers and switches THREE NEW TRENDS APPEARED IN 2015: Using persistence mechanisms Targeting outsourced service providers TWO OLD TRENDS CONTINUED: THE YEAR IN ATTACKS 47% 53% External Notification Internal Discovery MORE BREACHES DISCOVERED INTERNALLY Compared to 2014, the percentage of victims discovering a breach internally rose 16%. 16% INDUSTRIES WHERE MANDIANT INVESTIGATED Percentage of total attacks by industry. MORE AND LESS Some industries saw an increase in attacks compared to 2014. Some saw a decrease. HIGH TECH BUSINESS AND PROFESSIONAL SERVICES 6%6%
