Seurity policy
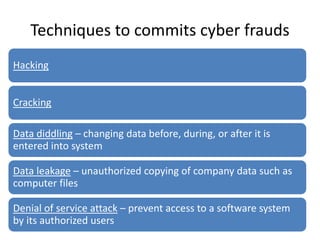
- 1. Techniques to commits cyber frauds Hacking Cracking Data diddling – changing data before, during, or after it is entered into system Data leakage – unauthorized copying of company data such as computer files Denial of service attack – prevent access to a software system by its authorized users
- 2. Techniques to commits cyber frauds Internet terrorism – using internet to disrupt e-commerce ex. - SONY Logic time bombs – program that lies idle until some specified circumstances triggers; after this programs or data destroyed Masquerading or impersonation – perpetrator gsins access to the system by pretending to be an authorized user Password cracking – steals the file containing valid passwords, decrypts them and use them to gain access to system resources Piggybacking – tapping into a telecomm. Line and latching on to a legitimate user before he got into the system
- 3. Techniques to commits cyber frauds Round down – all int. calculation up to 2 decimal places, remaining fraction is placed in account controlled by perpetrator Scavenging or dumpster diving – searching confidential info in rubbish bin of corporate records Social engineering techniques – perpetrator tricks an employee into giving out info needed Super zapping – unauthorized use of special system programs to bypass regular system controls and perform illegal acts Trap door - enter into the system using a back door
- 4. Impact of cyber frauds on enterprises Financial loss Legal repercussions Loss of credibility or competitive edge Disclosure of confidential, sensitive or embarrassing information sabotage
- 5. Examples of impact Unauthorized data access of citi bank Sony mail hack
- 6. Reason behind Cyber frauds Organization to update themselves to new set of risks Smart fraudsters Failure of internal control system
- 7. Cyber frauds (any type of deliberate deception that occur online) Pure cyber frauds Cyber enabled frauds
- 8. IS security policy Introduction Tools to implement policy Issues to address Members Policies and hierarchy Components
- 9. Introduction • Intent by top level mgmt. about how to protect info. Assets • Formal statement of rules (documented) • IS security program • Direction and instruction to employees
- 10. Security policy invariably includes rules intended Preserve and protect information from unauthorized access Limit legal liability from employees or third party Prevent waste or inappropriate use of organization resources
- 11. Tools to implement policy (standard, guideline & procedures) • Offer users a clear approach about implementing policy and meeting organizational goals • Procedures – detailed steps to be followed • Uniform use of specific technologies • Guidelines are useful to understand standard
- 12. Issues to address Guiding documents to middle and lower level management Formally, written, available to everyone, updated, state roles and responsibilities to everyone, stating scope of the policy Security policy manual Does not need to be extremely extensive
- 13. Members of security policy Managerial Technologicallegal who have budget and policy authority IT EXPERTS What can and cannot be supported Who know the legal Ramifications of Various policy charges
- 14. Components • Purpose and scope of document • Security infrastructure • Response mechanism and incident reporting • Environmental security policy • It operations management • It communication • System development and maintenance control • Legal compliances • Monitoring and auditing requirements
- 15. Information security policy and their hierarchy Information security policy User security policy Acceptable usage policy Organizational info security policy Network and system security policy Info classification policy Conditions of connection
- 16. Information security policy and their hierarchy Information security policy – definition of info security User security policy – specify responsibilities and requirements Acceptable usage policy – satisfactory use of email and internet services Organizational info security policy – group policy of security of its info assets Network and system security policy – system and network security Info classification policy –sets out policy for classification of information Conditions of connection – sets out the group policy for connecting to their network
