S sdlc datasheet q1-2015 v fnl
•
0 recomendaciones•160 vistas
Infoedge Consulting, SDLC Datasheet
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
Más contenido relacionado
La actualidad más candente
La actualidad más candente (20)
MCGlobalTech Commercial Cybersecurity Capability Statement

MCGlobalTech Commercial Cybersecurity Capability Statement
The Future of Your Security Operations - Part 2: Tech Integration

The Future of Your Security Operations - Part 2: Tech Integration
An Intro to Resolver's Incident Management Application

An Intro to Resolver's Incident Management Application
Moving Forward: Setting The Direction - A Findings Review of CTEK’s 2020 Annu...

Moving Forward: Setting The Direction - A Findings Review of CTEK’s 2020 Annu...
Why Corporate Security Professionals Should Care About Information Security 

Why Corporate Security Professionals Should Care About Information Security
SOC 2 Type 1 Vs. Type 2: Do You Really Need It? This Will Help You Decide! 

SOC 2 Type 1 Vs. Type 2: Do You Really Need It? This Will Help You Decide!
Cybersecurity: Intelligence, innovation, and information warfare

Cybersecurity: Intelligence, innovation, and information warfare
ISO 27004- Information Security Metrics Implementation

ISO 27004- Information Security Metrics Implementation
Destacado
Destacado (18)
03 DSD-NL 2016 - Simona Gebruikersmiddag - Floating point onnauwkeurigheid en...

03 DSD-NL 2016 - Simona Gebruikersmiddag - Floating point onnauwkeurigheid en...
04 DSD-NL 2016 - Simona Gebruikersmiddag - Detailmodellen, modellering tot aa...

04 DSD-NL 2016 - Simona Gebruikersmiddag - Detailmodellen, modellering tot aa...
17 DSD-NL 2016 - Delft-FEWS Gebruikersdag - Hoe goed is mijn kansverwachting ...

17 DSD-NL 2016 - Delft-FEWS Gebruikersdag - Hoe goed is mijn kansverwachting ...
2 identificação e interpretação dos riscos ocupacionais 2

2 identificação e interpretação dos riscos ocupacionais 2
16 DSD-NL 2016 - Delft-FEWS Gebruikersdag - Jeroen Ligtenberg, RWS-WVL & Edwi...

16 DSD-NL 2016 - Delft-FEWS Gebruikersdag - Jeroen Ligtenberg, RWS-WVL & Edwi...
02 - DSD-NL 2016 - Geo Klantendag - Workshop funderingen voor on- en offshore...

02 - DSD-NL 2016 - Geo Klantendag - Workshop funderingen voor on- en offshore...
Similar a S sdlc datasheet q1-2015 v fnl
Similar a S sdlc datasheet q1-2015 v fnl (20)
Meraj Ahmad - Information security in a borderless world

Meraj Ahmad - Information security in a borderless world
Security of the future - Adapting Approaches to What We Need

Security of the future - Adapting Approaches to What We Need
IT Guide for Mobility: Making the case for Security leaders

IT Guide for Mobility: Making the case for Security leaders
Strategic Insights on IT & Cyber Risk Assessments.pdf

Strategic Insights on IT & Cyber Risk Assessments.pdf
Building a business case for expanding your AppSec Program

Building a business case for expanding your AppSec Program
Building Success from Scratch Custom Web Application Development Strategies.pdf

Building Success from Scratch Custom Web Application Development Strategies.pdf
Último
Falcon stands out as a top-tier P2P Invoice Discounting platform in India, bridging esteemed blue-chip companies and eager investors. Our goal is to transform the investment landscape in India by establishing a comprehensive destination for borrowers and investors with diverse profiles and needs, all while minimizing risk. What sets Falcon apart is the elimination of intermediaries such as commercial banks and depository institutions, allowing investors to enjoy higher yields.Falcon Invoice Discounting: The best investment platform in india for investors

Falcon Invoice Discounting: The best investment platform in india for investorsFalcon Invoice Discounting
VIP Call Girls Napur Anamika Call Now: 8617697112 Napur Escorts Booking Contact Details WhatsApp Chat: +91-8617697112 Napur Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus they look fabulously elegant; making an impressionable. Independent Escorts Napur understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together. We provide –(Anamika) VIP Call Girls Napur Call Now 8617697112 Napur Escorts 24x7

(Anamika) VIP Call Girls Napur Call Now 8617697112 Napur Escorts 24x7Call Girls in Nagpur High Profile Call Girls
Último (20)
Falcon Invoice Discounting: The best investment platform in india for investors

Falcon Invoice Discounting: The best investment platform in india for investors
The Path to Product Excellence: Avoiding Common Pitfalls and Enhancing Commun...

The Path to Product Excellence: Avoiding Common Pitfalls and Enhancing Commun...
FULL ENJOY Call Girls In Majnu Ka Tilla, Delhi Contact Us 8377877756

FULL ENJOY Call Girls In Majnu Ka Tilla, Delhi Contact Us 8377877756
Call Girls Service In Old Town Dubai ((0551707352)) Old Town Dubai Call Girl ...

Call Girls Service In Old Town Dubai ((0551707352)) Old Town Dubai Call Girl ...
Malegaon Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service

Malegaon Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service
(Anamika) VIP Call Girls Napur Call Now 8617697112 Napur Escorts 24x7

(Anamika) VIP Call Girls Napur Call Now 8617697112 Napur Escorts 24x7
Russian Call Girls In Gurgaon ❤️8448577510 ⊹Best Escorts Service In 24/7 Delh...

Russian Call Girls In Gurgaon ❤️8448577510 ⊹Best Escorts Service In 24/7 Delh...
Value Proposition canvas- Customer needs and pains

Value Proposition canvas- Customer needs and pains
Call Girls In Noida 959961⊹3876 Independent Escort Service Noida

Call Girls In Noida 959961⊹3876 Independent Escort Service Noida
Chandigarh Escorts Service 📞8868886958📞 Just📲 Call Nihal Chandigarh Call Girl...

Chandigarh Escorts Service 📞8868886958📞 Just📲 Call Nihal Chandigarh Call Girl...
Business Model Canvas (BMC)- A new venture concept

Business Model Canvas (BMC)- A new venture concept
Call Now ☎️🔝 9332606886🔝 Call Girls ❤ Service In Bhilwara Female Escorts Serv...

Call Now ☎️🔝 9332606886🔝 Call Girls ❤ Service In Bhilwara Female Escorts Serv...
BAGALUR CALL GIRL IN 98274*61493 ❤CALL GIRLS IN ESCORT SERVICE❤CALL GIRL

BAGALUR CALL GIRL IN 98274*61493 ❤CALL GIRLS IN ESCORT SERVICE❤CALL GIRL
The Abortion pills for sale in Qatar@Doha [+27737758557] []Deira Dubai Kuwait![The Abortion pills for sale in Qatar@Doha [+27737758557] []Deira Dubai Kuwait](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![The Abortion pills for sale in Qatar@Doha [+27737758557] []Deira Dubai Kuwait](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
The Abortion pills for sale in Qatar@Doha [+27737758557] []Deira Dubai Kuwait
Falcon's Invoice Discounting: Your Path to Prosperity

Falcon's Invoice Discounting: Your Path to Prosperity
S sdlc datasheet q1-2015 v fnl
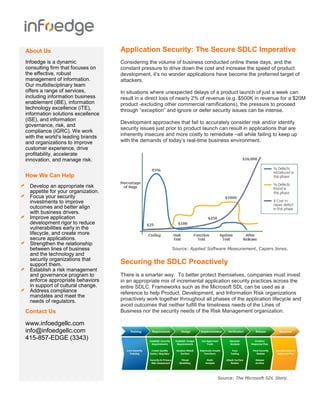
- 1. Application Security: The Secure SDLC Imperative Considering the volume of business conducted online these days, and the constant pressure to drive down the cost and increase the speed of product development, it’s no wonder applications have become the preferred target of attackers. In situations where unexpected delays of a product launch of just a week can result in a direct loss of nearly 2% of revenue (e.g. $500K in revenue for a $20M product -excluding other commercial ramifications), the pressure to proceed through “exception” and ignore or defer security issues can be intense. Development approaches that fail to accurately consider risk and/or identify security issues just prior to product launch can result in applications that are inherently insecure and more costly to remediate –all while failing to keep up with the demands of today’s real-time business environment. Securing the SDLC Proactively There is a smarter way. To better protect themselves, companies must invest in an appropriate mix of incremental application security practices across the entire SDLC. Frameworks such as the Microsoft SDL can be used as a reference to help Product, Development, and Information Risk organizations proactively work together throughout all phases of the application lifecycle and avoid outcomes that neither fulfill the timeliness needs of the Lines of Business nor the security needs of the Risk Management organization. ` About Us Infoedge is a dynamic consulting firm that focuses on the effective, robust management of information. Our multidisciplinary team offers a range of services, including information business enablement (iBE), information technology excellence (iTE), information solutions excellence (iSE), and information governance, risk, and compliance (iGRC). We work with the world’s leading brands and organizations to improve customer experience, drive profitability, accelerate innovation, and manage risk. How We Can Help Develop an appropriate risk appetite for your organization. Focus your security investments to improve outcomes and better align with business drivers. Improve application development rigor to reduce vulnerabilities early in the lifecycle, and create more secure applications. Strengthen the relationship between lines of business and the technology and security organizations that support them. Establish a risk management and governance program to enforce appropriate behaviors in support of cultural change. Address compliance mandates and meet the needs of regulators. Contact Us www.infoedgellc.com info@infoedgellc.com 415-857-EDGE (3343) Source: Applied Software Measurement, Capers Jones. Source: The Microsoft SDL Story.
- 2. Secure Software Development Lifecycle (S-SDLC) Services We understand that different organizations have different requirements and our Secure Software Development Lifecycle approach works for companies at every level of maturity. The S-SDLC service mix delivers a unique set of capabilities to fit each client’s specific security needs and investment appetite. There are four complimentary service offerings that support our approach: Assessment—We work with our clients to thoroughly understand their existing capabilities across the S-SDLC, and then identify opportunities for focused improvement and capability development. Advisory—Using our extensive industry and domain knowledge, we help clients develop practices and apply the most up-to-date S-SDLC thinking across the areas of people, process, and technology. Operationalization—We help our clients implement their S- SDLC strategy using actionable and sustainable program initiatives, coupled with automation activities that ease the developer burden and drive lasting cultural change. Assurance—We help identify impactful business metrics and governance processes that demonstrate the program’s value, and ensure the level of risk management is aligned with the needs of the organization. Examples of Our S-SDLC Services in Action S-SDLC Maturity Assessment S-SDLC Advisory and Operationalization S-SDLC Assessment and Advisory CLIENT CONCERN: Repeated delays in the launch of new products due to late detection of security issues that had to be fixed prior to launch. CLIENT CONCERN: A serious application security bug was released into production without detection, resulting in a potential breach of confidentiality. CLIENT CONCERN: Regulators required additional confidence that the client had taken the right approach to securing applications. OUR SOLUTION: Assessed the service environment and developed new strategies aimed at early notification. Worked with client personnel to implement new services and drive awareness of new touch points and capabilities. OUR SOLUTION: Performed root cause analysis and identified the service gap. Developed capability integration service models and strategy for more effective partnering. Worked with client to implement solution. OUR SOLUTION: Worked with client to develop a multi-year S-SDLC roadmap. Developed and led the implementation of several services across a variety of development approaches (e.g. Agile & Waterfall) and third- party support structures. CLIENT IMPACT: Improved client’s relationship with peers and partners. Reduced the number of last- minute findings and therefore the extent of delays. CLIENT IMPACT: Avoided significant costs and risks by enhancing existing capabilities and integrating new ones. CLIENT IMPACT: Avoided regulatory action, and jump-started an enterprise-wide security transformation across all phases of the application lifecycle.
