Web Sec Auditor
•
0 recomendaciones•191 vistas
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
Más contenido relacionado
La actualidad más candente
La actualidad más candente (20)
Lidiia 'Alice' Skalytska - Security Checklist for Web Developers

Lidiia 'Alice' Skalytska - Security Checklist for Web Developers
Security Testing of Online Stores and Banking Applications

Security Testing of Online Stores and Banking Applications
Step by step guide for web application security testing

Step by step guide for web application security testing
Automatically detecting security vulnerabilities in WordPress

Automatically detecting security vulnerabilities in WordPress
Destacado
Destacado (16)
Preservation of Web Resources Part II, Ed Pinsent, ULCC

Preservation of Web Resources Part II, Ed Pinsent, ULCC
Preservation of Web Resources Part I, Kevin Ashley, ULCC

Preservation of Web Resources Part I, Kevin Ashley, ULCC
Similar a Web Sec Auditor
Exploring Web Security Threats: A Practical Study on SQL Injection and CSRF

Exploring Web Security Threats: A Practical Study on SQL Injection and CSRFBoston Institute of Analytics
Similar a Web Sec Auditor (20)
Deep understanding on Cross-Site Scripting and SQL Injection

Deep understanding on Cross-Site Scripting and SQL Injection
IRJET- A Survey on Various Cross-Site Scripting Attacks and Few Prevention Ap...

IRJET- A Survey on Various Cross-Site Scripting Attacks and Few Prevention Ap...
Routine Detection Of Web Application Defence Flaws

Routine Detection Of Web Application Defence Flaws
website vulnerability scanner and reporter research paper

website vulnerability scanner and reporter research paper
Exploring Web Security Threats: A Practical Study on SQL Injection and CSRF

Exploring Web Security Threats: A Practical Study on SQL Injection and CSRF
Analysis of Field Data on Web Security Vulnerabilities

Analysis of Field Data on Web Security Vulnerabilities
Más de Aung Khant
Más de Aung Khant (20)
Último
VIP Call Girl Service Andheri West ⚡ 9920725232 What It Takes To Be The Best ...

VIP Call Girl Service Andheri West ⚡ 9920725232 What It Takes To Be The Best ...dipikadinghjn ( Why You Choose Us? ) Escorts
(INDIRA) Call Girl Mumbai Call Now 8250077686 Mumbai Escorts 24x7

(INDIRA) Call Girl Mumbai Call Now 8250077686 Mumbai Escorts 24x7Call Girls in Nagpur High Profile Call Girls
( Jasmin ) Top VIP Escorts Service Dindigul 💧 7737669865 💧 by Dindigul Call G...

( Jasmin ) Top VIP Escorts Service Dindigul 💧 7737669865 💧 by Dindigul Call G...dipikadinghjn ( Why You Choose Us? ) Escorts
VIP Independent Call Girls in Andheri 🌹 9920725232 ( Call Me ) Mumbai Escorts...

VIP Independent Call Girls in Andheri 🌹 9920725232 ( Call Me ) Mumbai Escorts...dipikadinghjn ( Why You Choose Us? ) Escorts
(Vedika) Low Rate Call Girls in Pune Call Now 8250077686 Pune Escorts 24x7

(Vedika) Low Rate Call Girls in Pune Call Now 8250077686 Pune Escorts 24x7Call Girls in Nagpur High Profile Call Girls
VIP Kalyan Call Girls 🌐 9920725232 🌐 Make Your Dreams Come True With Mumbai E...

VIP Kalyan Call Girls 🌐 9920725232 🌐 Make Your Dreams Come True With Mumbai E...roshnidevijkn ( Why You Choose Us? ) Escorts
VIP Independent Call Girls in Bandra West 🌹 9920725232 ( Call Me ) Mumbai Esc...

VIP Independent Call Girls in Bandra West 🌹 9920725232 ( Call Me ) Mumbai Esc...dipikadinghjn ( Why You Choose Us? ) Escorts
(INDIRA) Call Girl Srinagar Call Now 8617697112 Srinagar Escorts 24x7

(INDIRA) Call Girl Srinagar Call Now 8617697112 Srinagar Escorts 24x7Call Girls in Nagpur High Profile Call Girls
Último (20)
Navi Mumbai Cooperetive Housewife Call Girls-9833754194-Natural Panvel Enjoye...

Navi Mumbai Cooperetive Housewife Call Girls-9833754194-Natural Panvel Enjoye...
cost-volume-profit analysis.ppt(managerial accounting).pptx

cost-volume-profit analysis.ppt(managerial accounting).pptx
VIP Call Girl Service Andheri West ⚡ 9920725232 What It Takes To Be The Best ...

VIP Call Girl Service Andheri West ⚡ 9920725232 What It Takes To Be The Best ...
(INDIRA) Call Girl Mumbai Call Now 8250077686 Mumbai Escorts 24x7

(INDIRA) Call Girl Mumbai Call Now 8250077686 Mumbai Escorts 24x7
Business Principles, Tools, and Techniques in Participating in Various Types...

Business Principles, Tools, and Techniques in Participating in Various Types...
Diva-Thane European Call Girls Number-9833754194-Diva Busty Professional Call...

Diva-Thane European Call Girls Number-9833754194-Diva Busty Professional Call...
( Jasmin ) Top VIP Escorts Service Dindigul 💧 7737669865 💧 by Dindigul Call G...

( Jasmin ) Top VIP Escorts Service Dindigul 💧 7737669865 💧 by Dindigul Call G...
Strategic Resources May 2024 Corporate Presentation

Strategic Resources May 2024 Corporate Presentation
20240419-SMC-submission-Annual-Superannuation-Performance-Test-–-design-optio...

20240419-SMC-submission-Annual-Superannuation-Performance-Test-–-design-optio...
Cybersecurity Threats in Financial Services Protection.pptx

Cybersecurity Threats in Financial Services Protection.pptx
VIP Independent Call Girls in Andheri 🌹 9920725232 ( Call Me ) Mumbai Escorts...

VIP Independent Call Girls in Andheri 🌹 9920725232 ( Call Me ) Mumbai Escorts...
(Vedika) Low Rate Call Girls in Pune Call Now 8250077686 Pune Escorts 24x7

(Vedika) Low Rate Call Girls in Pune Call Now 8250077686 Pune Escorts 24x7
VIP Kalyan Call Girls 🌐 9920725232 🌐 Make Your Dreams Come True With Mumbai E...

VIP Kalyan Call Girls 🌐 9920725232 🌐 Make Your Dreams Come True With Mumbai E...
Vasai-Virar Fantastic Call Girls-9833754194-Call Girls MUmbai

Vasai-Virar Fantastic Call Girls-9833754194-Call Girls MUmbai
Kharghar Blowjob Housewife Call Girls NUmber-9833754194-CBD Belapur Internati...

Kharghar Blowjob Housewife Call Girls NUmber-9833754194-CBD Belapur Internati...
VIP Independent Call Girls in Bandra West 🌹 9920725232 ( Call Me ) Mumbai Esc...

VIP Independent Call Girls in Bandra West 🌹 9920725232 ( Call Me ) Mumbai Esc...
(INDIRA) Call Girl Srinagar Call Now 8617697112 Srinagar Escorts 24x7

(INDIRA) Call Girl Srinagar Call Now 8617697112 Srinagar Escorts 24x7
Web Sec Auditor
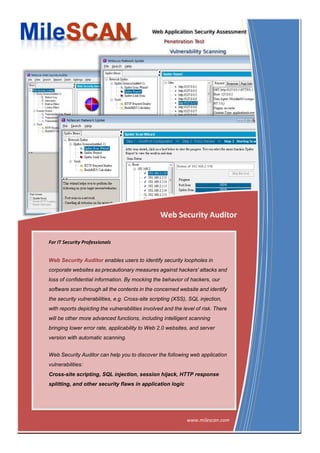
- 1. Web Security Auditor For IT Security Professionals Web Security Auditor enables users to identify security loopholes in corporate websites as precautionary measures against hackers' attacks and loss of confidential information. By mocking the behavior of hackers, our software scan through all the contents in the concerned website and identify the security vulnerabilities, e.g. Cross-site scripting (XSS), SQL injection, with reports depicting the vulnerabilities involved and the level of risk. There will be other more advanced functions, including intelligent scanning bringing lower error rate, applicability to Web 2.0 websites, and server version with automatic scanning. Web Security Auditor can help you to discover the following web application vulnerabilities: Cross-site scripting, SQL injection, session hijack, HTTP response splitting, and other security flaws in application logic
