Does your sales team have enough trusted content to close?
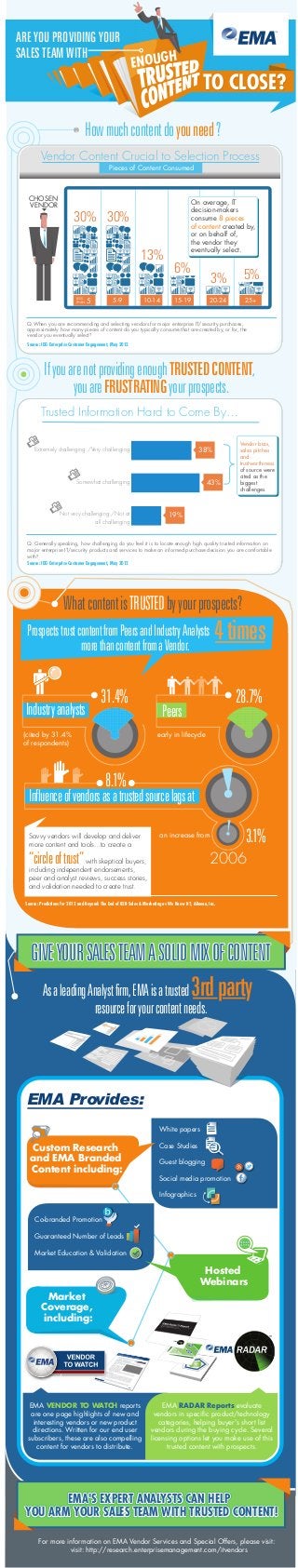
- 1. Howmuchcontentdoyouneed? Vendor Content Crucial to Selection Process Pieces of Content Consumed IfyouarenotprovidingenoughTRUSTEDCONTENT, youareFRUSTRATINGyourprospects. Trusted Information Hard to Come By… Extremely challenging /Very challenging Somewhat challenging Not very challenging /Not at all challenging 38% 43% 19% WhatcontentisTRUSTEDbyyourprospects? ProspectstrustcontentfromPeersandIndustryAnalysts Industryanalysts 31.4% (cited by 31.4% of respondents) 28.7% early in lifecycle Peers Influenceofvendorsasatrustedsourcelagsat 8.1% 3.1% 2006 TO CLOSE?TO CLOSE? ARE YOU PROVIDING YOUR SALES TEAM WITH ENOUGH an increase from White papers Case Studies Guest blogging Social media promotion Infographics CHOSEN VENDOR 5LESS THAN 30% 5-9 30% 10-14 13% 15-19 6% 20-24 3% 25+ 5% On average, IT decision-makers consume 8 pieces of content created by, or on behalf of, the vendor they eventually select. Vendor bias, sales pitches and trustworthiness of source were cited as the biggest challenges. Savvy vendors will develop and deliver more content and tools...to create a “circleoftrust”with skeptical buyers, including independent endorsements, peer and analyst reviews, success stories, and validation needed to create trust. Custom Research and EMA Branded Content including: GIVEYOURSALESTEAMASOLIDMIXOFCONTENT GIVEYOURSALESTEAMASOLIDMIXOFCONTENT GIVEYOURSALESTEAMASOLIDMIXOFCONTENTGIVEYOURSALESTEAMASOLIDMIXOFCONTENTGIVEYOURSALESTEAMASOLIDMIXOFCONTENT resourceforyourcontentneeds. Market Coverage, including: EMA'S EXPERT ANALYSTS CAN HELPEMA'S EXPERT ANALYSTS CAN HELP YOU ARM YOUR SALES TEAM WITH TRUSTED CONTENT!YOU ARM YOUR SALES TEAM WITH TRUSTED CONTENT! EMA'S EXPERT ANALYSTS CAN HELPEMA'S EXPERT ANALYSTS CAN HELP YOU ARM YOUR SALES TEAM WITH TRUSTED CONTENT!YOU ARM YOUR SALES TEAM WITH TRUSTED CONTENT! EMA'S EXPERT ANALYSTS CAN HELP YOU ARM YOUR SALES TEAM WITH TRUSTED CONTENT! For more information on EMA Vendor Services and Special Offers, please visit: visit: http://research.enterprisemanagement.com/itvendors EMA RADAR Reports evaluate vendors in specific product/technology categories, helping buyer's short list vendors during the buying cycle. Several licensing options let you make use of this trusted content with prospects. EMA VENDOR TO WATCH reports are one page highlights of new and interesting vendors or new product directions. Written for our end user subscribers, these are also compelling content for vendors to distribute. AsaleadingAnalystfirm,EMAisatrusted3rdparty Q.When you are recommending and selecting vendors for major enterprise IT/security purchases, approximately how many pieces of content do you typically consume that are created by, or for, the vendor you eventually select? Source: IDG Enterprise Customer Engagement, May 2012 Source: Predictions for 2012 and Beyond: The End of B2B Sales & Marketing as We Know It?, Alinean, Inc. Source: IDG Enterprise Customer Engagement, May 2012 Q. Generally speaking, how challenging do you feel it is to locate enough high quality trusted information on major enterprise IT/security products and services to make an informed purchase decision you are comfortable with? morethancontentfromaVendor. 4times EMA Provides: Co-branded Promotion Guaranteed Number of Leads Market Education & Validation Hosted Webinars
