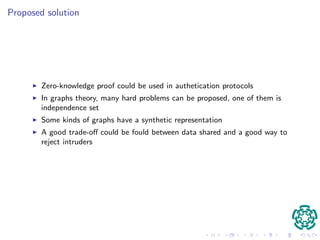
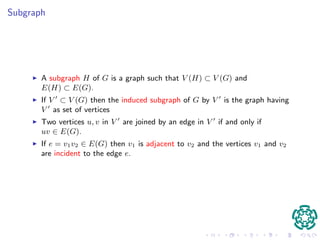
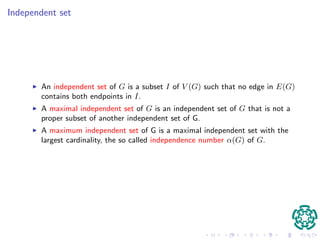
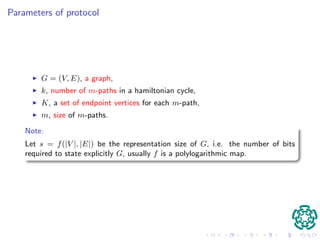
El documento presenta un protocolo de autenticación basado en pruebas de conocimiento cero, diseñado para dispositivos móviles, donde se propone utilizar la teoría de grafos para enfrentar problemas de compartición de credenciales. Se describe un protocolo de identificación que utiliza caminos no cruzados y disjuntos en un ciclo hamiltoniano, garantizando la seguridad frente a intrusos mediante la complejidad computacional del problema. Se espera que las contribuciones incluyan una implementación eficiente del protocolo y la caracterización de caminos en grafos.